-
What Is RMAN in AWS Environments
-
How to Use RMAN with Oracle on EC2?
-
How to Use RMAN with Amazon RDS?
-
Why Choose Advanced Protection Beyond Native Tools?
-
Enterprise-Level Database Protection: Vinchin Backup & Recovery
-
AWS RMAN FAQs
-
Conclusion
Are you running Oracle databases on AWS and wondering how to protect your data? Many administrators rely on Oracle Recovery Manager (RMAN) for backup and recovery tasks. But how does RMAN work in AWS environments, what are the key differences and limitations, and what are the best practices? In this guide, we’ll break down these essentials step by step—covering both Amazon EC2 and Amazon RDS scenarios—so you can confidently safeguard your Oracle workloads in the cloud.
What Is RMAN in AWS Environments
RMAN, or Oracle Recovery Manager, is Oracle’s built-in tool for backing up, restoring, and recovering databases. In AWS environments, you can use RMAN with Oracle databases running on either Amazon EC2 or Amazon RDS for Oracle.
On EC2 instances, you have full control over both the operating system and database configuration. This means you can use RMAN just as you would in an on-premises setup—scheduling jobs via cron or other schedulers, managing scripts directly at OS level, and storing backups wherever needed.
With Amazon RDS for Oracle—a managed service—you do not have direct OS-level access. Instead, AWS provides special stored procedures that allow limited interaction with RMAN through SQL commands.
RMAN supports full backups (capturing all data), incremental backups (only changed blocks), archived log backups (for point-in-time recovery), validation operations (to check backup integrity), and restores from various storage locations. In AWS setups, you may store RMAN backups on local disks attached to EC2 instances or leverage cloud storage like Amazon S3 or EFS depending on your compliance needs.
This flexibility helps meet different recovery objectives—from quick restores after accidental deletions to meeting regulatory requirements around long-term retention.
How to Use RMAN with Oracle on EC2?
Running Oracle on EC2 gives you maximum flexibility over backup strategies. You can use RMAN to back up your database to local storage volumes (such as EBS), network file systems like EFS, or directly into Amazon S3 buckets using integration modules.
Many organizations choose S3 due to its durability and cost-effectiveness compared to traditional disk-based storage. To enable direct S3 integration from an EC2-hosted database instance using RMAN requires installing the Oracle Secure Backup (OSB) Cloud Module.
Before starting:
Ensure Java 1.7 or higher is installed (
which java/java -version). If missing, install it using your package manager.Create a wallet directory where OSB credentials will be stored:
mkdir $ORACLE_HOME/osbws_wallet
Download the OSB Cloud Module installer zip file from Oracle’s official site. Place it inside your wallet directory then unzip it there.
Next comes installation:
Run this command within your wallet directory:
java -jar osbws_install.jar -AWSID <aws_user_id> -AWSKey <aws_user_key> -walletDir $ORACLE_HOME/osbws_wallet -libDir $ORACLE_HOME/lib -location <region> -awsEndPoint <endpoint>
If your instance lacks internet access to download dependencies during installation, add
-otnUser <oracle_user> -otnPass <oracle_password>parameters so it fetches required files using provided credentials instead.After installation completes successfully, rename any generated config file under
$ORACLE_HOME/dbsif needed for consistency across environments.
Now configure your backup job:
When allocating channels in RMAN scripts—for example,
RUN {
ALLOCATE CHANNEL c1 DEVICE TYPE sbt PARMS 'SBT_LIBRARY=libosbws.so ENV=(OSB_WS_PFILE=<$ORACLE_HOME>/dbs/osbwsCONFIG.ora)';
BACKUP DATABASE PLUS ARCHIVELOG;
}For larger databases or faster throughput during backup/restore operations consider allocating multiple channels—one per vCPU where possible—to maximize parallelism:
ALLOCATE CHANNEL c1 DEVICE TYPE sbt ...; ALLOCATE CHANNEL c2 DEVICE TYPE sbt ...; -- Repeat as needed based on available resources
The number of channels should match available CPU cores/network bandwidth but avoid exceeding limits set by either S3 API quotas or instance specs.
To restore a database from S3:
First ensure connectivity between your EC2 instance and target bucket; then pull necessary files locally if required before issuing standard RESTORE / RECOVER commands within an interactive RMAN session.
If errors occur during backup or restore—such as authentication failures due to expired credentials in the wallet directory—or network timeouts caused by unstable connections between EC2/S3 endpoints—review logs found under $ORACLE_BASE/diag/rdbms/.../trace/ along with any output written by OSB itself inside its wallet folder.
How to Use RMAN with Amazon RDS?
Amazon RDS for Oracle simplifies many aspects of administration but restricts direct operating system access—including native shell scripting around traditional tools like rman.exe itself. Instead administrators interact through SQL procedures exposed via packages such as rdsadmin.rdsadmin_rman_util which orchestrate underlying backup logic behind-the-scenes.
You can back up data onto local RDS storage volumes; if enabled via parameter groups/integration settings also onto external targets such as S3/EFS directories mapped within RDS context (“DATA_PUMP_DIR”, etc.).
Here’s how common tasks look:
1. To perform a full database backup run this block inside SQL*Plus (or another SQL client):
BEGIN rdsadmin.rdsadmin_rman_util.backup_database_full( p_owner => 'SYS', p_directory_name => 'DATA_PUMP_DIR', p_tag => 'FULL_DB_BACKUP', p_rman_to_dbms_output => FALSE ); END; /
The result is stored under specified logical directory; monitor space usage since costs accrue based on consumed IOPS/storage class chosen at creation time!
2. For incremental backups specify desired level:
BEGIN rdsadmin.rdsadmin_rman_util.backup_database_incremental( p_owner => 'SYS', p_directory_name => 'DATA_PUMP_DIR', p_level => 1, p_tag => 'INCR_BACKUP', p_rman_to_dbms_output => FALSE ); END; /
3. To archive logs first create a dedicated logical directory:
EXEC rdsadmin.rdsadmin_util.create_directory(p_directory_name => 'ARCHIVE_LOG_BACKUP');
Then initiate log backup:
BEGIN rdsadmin.rdsadmin_rman_util.backup_archivelog_all( p_owner => 'SYS', p_directory_name => 'ARCHIVE_LOG_BACKUP', p_tag => 'LOG_BACKUP', p_rman_to_dbms_output => FALSE ); END; /
4. Monitor progress/status by querying internal tables/logs:
SELECT * FROM TABLE(rdsadmin.rds_file_util.listdir('BDUMP')) WHERE filename LIKE '%rman%';For detailed error messages read contents using
SELECT text FROM TABLE(rdsadmin.rds_file_util.read_text_file('BDUMP','<filename>'));
Why Choose Advanced Protection Beyond Native Tools?
While native tools like RMAN offer powerful capabilities out-of-the-box they come with certain limitations especially within public cloud contexts:
On EC2, everything must be managed manually—from scripting/scheduling jobs securely handling credential rotation maintaining audit trails enforcing retention policies tracking compliance exceptions—all without centralized dashboard oversight unless additional tooling layers are introduced atop base platform itself!
On RDS, functionality remains tightly scoped around what’s exposed via supported stored procedures/APIs meaning advanced features such as cross-platform scheduling ransomware detection granular reporting automation often require third-party solutions anyway.
Do you need compliance support long-term retention automated recovery testing? Native tools alone may not suffice—which leads many enterprises toward enhanced platforms providing extra layers of automation security governance visibility above/beyond core engine capabilities.
Enterprise-Level Database Protection: Vinchin Backup & Recovery
For organizations seeking streamlined protection beyond native tools, Vinchin Backup & Recovery delivers comprehensive enterprise-grade solutions tailored for modern databases—including robust support for Oracle alongside MySQL, SQL Server, MariaDB, PostgreSQL, PostgresPro, and TiDB. When safeguarding critical workloads like Oracle databases on AWS infrastructure, Vinchin Backup & Recovery empowers users with batch database backup capabilities, flexible data retention policies management including GFS retention options, seamless cloud/tape archiving integration, reliable restore-to-new-server workflows, and thorough integrity checks—all designed to automate processes while ensuring regulatory compliance and operational resilience across diverse IT landscapes.
The intuitive web console makes managing protection effortless:
Step 1. Select the Oracle database to back up
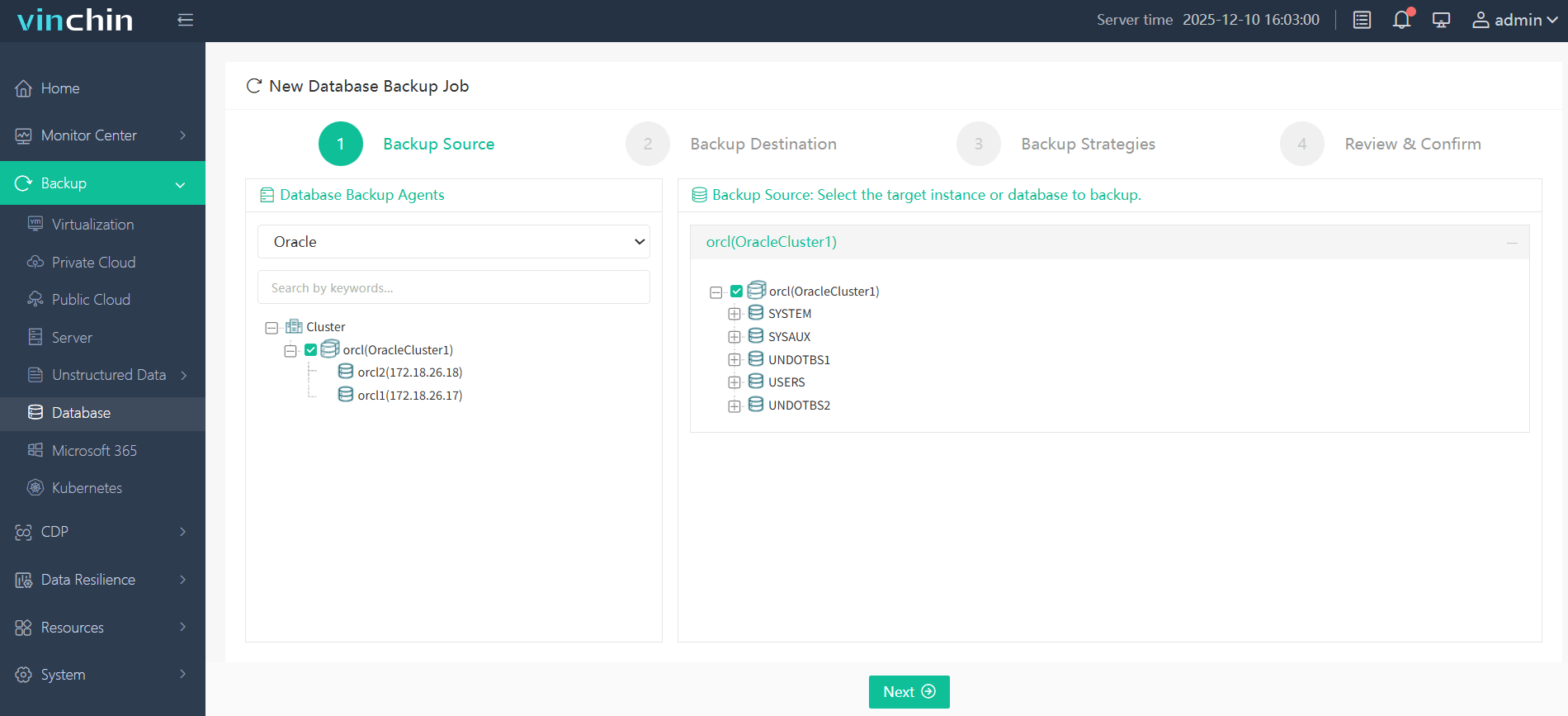
Step 2. Choose the backup storage
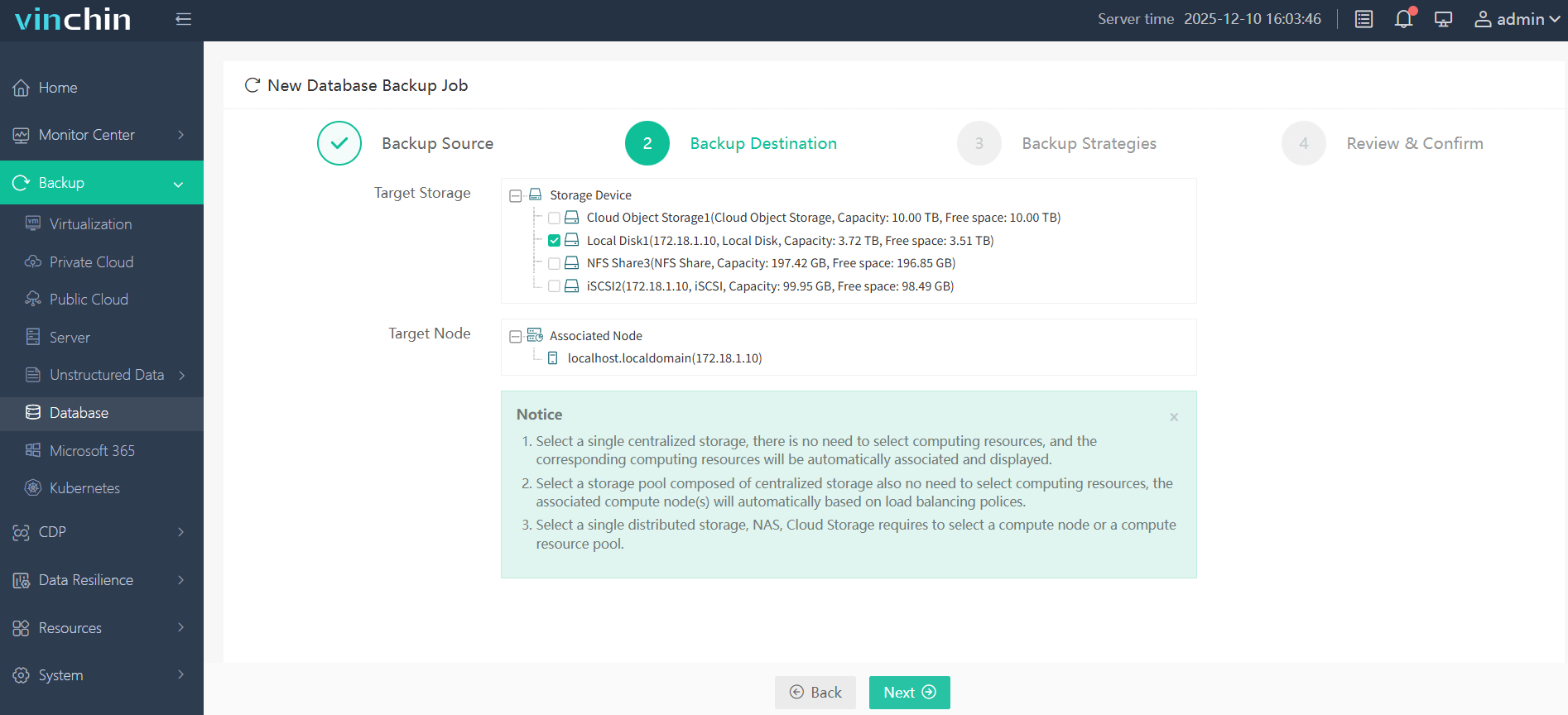
Step 3. Define the backup strategy
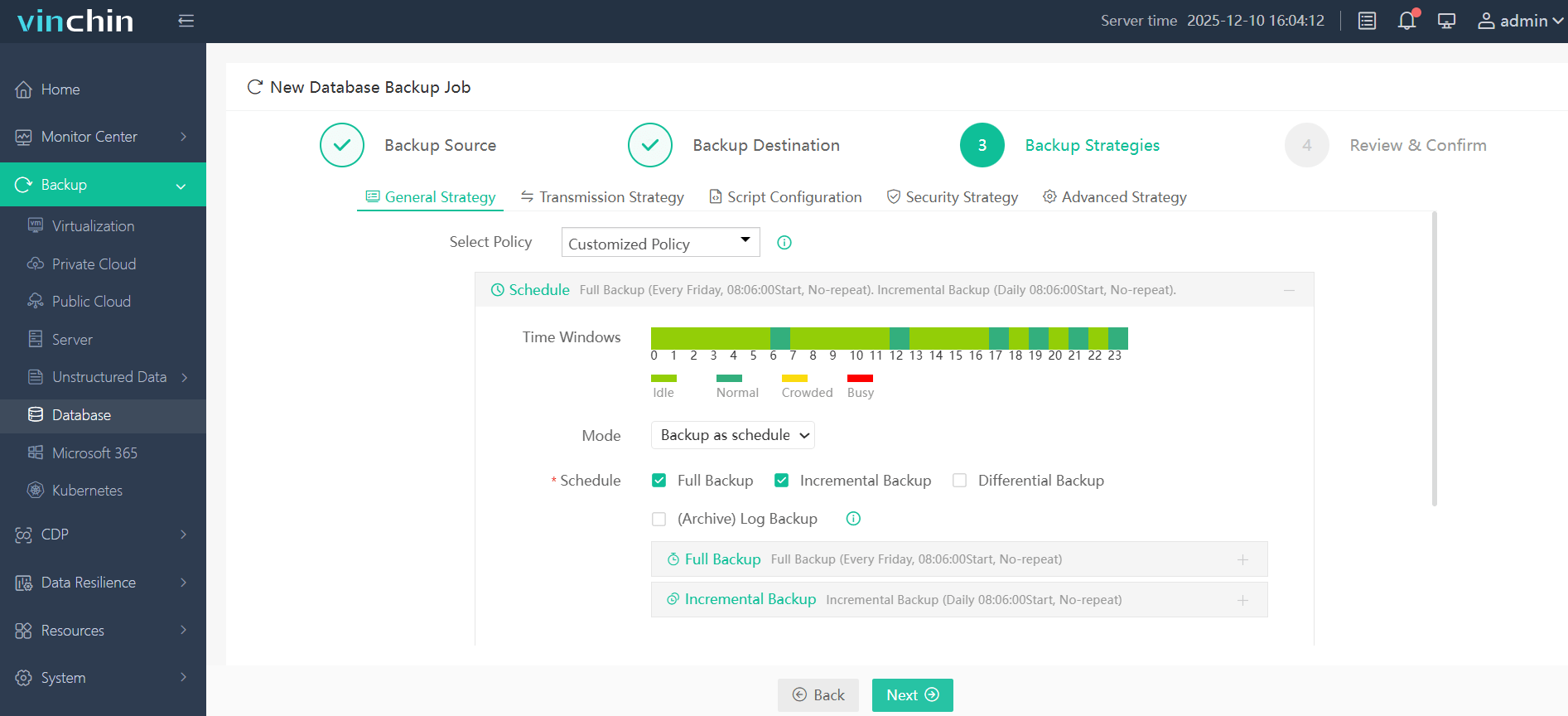
Step 4. Submit the job
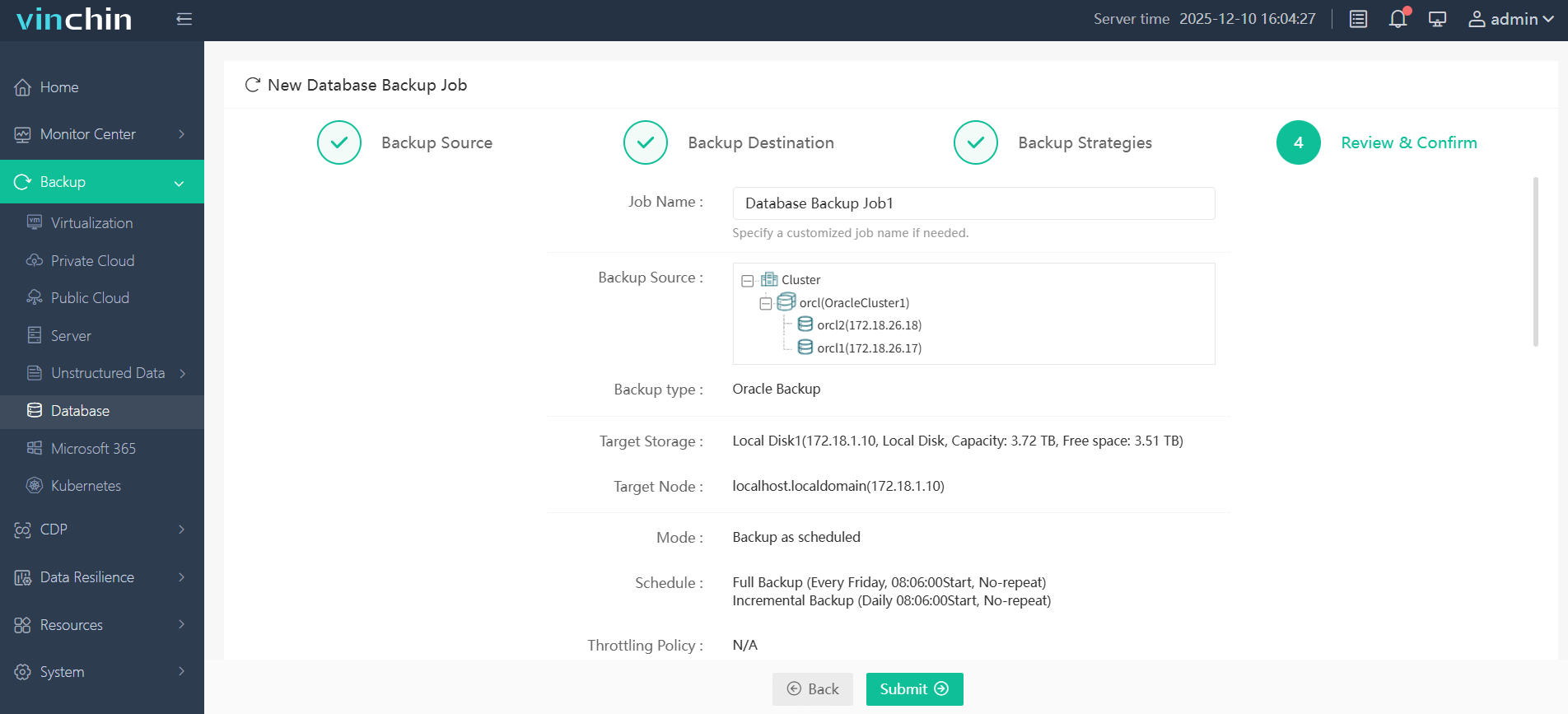
Vinchin Backup & Recovery is trusted worldwide by enterprises seeking top-rated data protection software—start today with a free 60-day trial packed with all features by clicking the download button below.
AWS RMAN FAQs
Q1: Can I use multiple channels in my EC2-based RMAN script for faster backups?
Yes; allocate several channels matching available CPU/network resources in your script's RUN block before starting BACKUP commands.
Q2: What should I do if my scheduled RDS full backup fails due to insufficient space?
Check allocated storage size increase quota if needed delete obsolete files/directories then rerun procedure via SQL client interface.
Q3: How do I validate that my latest S3-based EC2 backups are restorable?
Run RESTORE VALIDATE DATABASE command after uploading sets confirm no errors appear in resulting trace/log output.
Conclusion
RMAN delivers reliable protection options across both EC2/RDS deployments—but advanced needs call for more automation security oversight than native tools alone provide today! Vinchin brings centralized management flexible policy enforcement integrity checks making enterprise-grade data protection easy even at scale—try our free trial now!
Share on:






