-
What Securing a Virtual Machine Means
-
Why Virtual Machine Security Matters
-
Method 1: Network Isolation for Virtual Machines
-
Method 2: Patch Management and Updates
-
Method 3: Access Control and Authentication
-
Method 4: Implementing Monitoring and Logging
-
Method 5: Encrypting VM Data and Storage
-
How to Backup Virtual Machine with Vinchin Backup & Recovery?
-
How to Secure a Virtual Machine FAQs
-
Conclusion
Virtual machines (VMs) have become essential in IT environments worldwide. They support development, testing, and production workloads across industries. But with their flexibility comes risk—if you don’t secure your VMs properly, attackers can exploit them, steal data, or disrupt business operations. So how do you secure a virtual machine? Let’s break it down step by step using proven strategies that build upon each other for maximum protection.
What Securing a Virtual Machine Means
Securing a virtual machine means defending it against threats both inside and outside your network perimeter. This involves isolating VMs from unnecessary connections, keeping software up to date, controlling who can access resources, monitoring activity closely, encrypting sensitive data at rest and in transit, and ensuring reliable backups exist if disaster strikes. Each layer adds strength—think of it as building several walls around your digital assets instead of just one.
Why Virtual Machine Security Matters
Why should you care about VM security? Because even one weak VM can open the door for attackers to move laterally across your environment or escalate privileges to compromise more systems—including hosts or storage arrays that hold sensitive information. Data loss, downtime, regulatory fines—all are possible outcomes of poor VM security practices Defense-in-depth isn’t just theory; it’s essential for safe virtualization at any scale.
Before we dive into specific methods: remember that no single technique is enough on its own—a layered approach works best.
Method 1: Network Isolation for Virtual Machines
Network isolation forms your first line of defense when securing virtual machines. By separating VMs from each other—and from untrusted networks—you limit an attacker’s ability to move laterally if they breach one system.
Start by configuring each VM to use its own dedicated virtual network segment or VLAN within your hypervisor platform (such as VMware vSwitches or Hyper-V Virtual Switch Manager). For example: assign production VMs to VLAN 10 while test/dev VMs use VLAN 20—this keeps traffic separate unless explicitly allowed through firewall rules.
On Linux hosts running KVM/QEMU or similar platforms, use iptables commands like:
iptables -A FORWARD -i vnet0 -o vnet1 -j DROP
This blocks direct traffic between two virtual interfaces unless you create exceptions.
Avoid enabling promiscuous mode unless absolutely necessary—it allows VMs to see all network traffic on their segment which increases risk.
Always deploy firewalls at both host level (using tools like firewalld or Windows Defender Firewall) and guest OS level.
For sensitive workloads such as databases or domain controllers:
Place these VMs on isolated subnets
Restrict communication using access control lists (ACLs)
If you manage cloud-based VMs or large enterprise clusters:
Leverage built-in segmentation features such as security groups or microsegmentation policies.
Regularly review your network topology—ensure no VM has unintended exposure either internally or externally.
Remember: VLANs alone aren’t enough if not paired with strict firewall controls!
Method 2: Patch Management and Updates
Keeping every layer updated is critical when learning how to secure a virtual machine effectively.
Attackers often target known vulnerabilities in outdated operating systems (OS), applications—or even hypervisors themselves.
Begin by updating the hypervisor platform regularly; check vendor advisories frequently.
Next update guest OSes—Linux users can automate this with package managers like yum, dnf, apt, while Windows admins should enable automatic updates via Windows Update settings.
Don’t forget third-party applications installed inside each VM—they’re common attack vectors too!
Whenever possible:
Test patches in non-production environments first
Schedule maintenance windows during off-hours
Use automation tools like Ansible (for Linux) or WSUS (for Windows) if managing many systems
After applying updates:
Verify services start correctly
Monitor logs for errors
Update management agents/tools running inside guests—they also need regular patching!
Staying current reduces risk dramatically—but only if done consistently across all components.
Method 3: Access Control and Authentication
Implement access control measures so only authorized users can interact with your virtual machines—and only as much as needed for their job roles.
Start by enforcing least privilege everywhere:
Avoid daily use of administrator/root accounts—instead create standard user accounts with limited permissions wherever possible.
Assign granular roles such as “VM Operator” (can start/stop/reboot), “Backup Admin” (can run backups/restores), etc., using built-in RBAC features found in most modern hypervisors.
Require strong unique passwords per account—and rotate them regularly!
Enable multi-factor authentication (MFA) on all management interfaces including web consoles like vCenter Server Appliance or Hyper-V Manager—not just remote desktop sessions.
For remote administration:
Use secure protocols such as SSH with key-based authentication for Linux guests,
Or enable RDP with Network Level Authentication plus IP allow-listing/VPN tunneling for Windows guests,
Limit management interface access strictly by source IP address ranges whenever feasible,
Regularly audit user accounts—remove stale entries promptly,
Review permission assignments periodically; adjust based on changing responsibilities,
Check audit logs often for signs of unauthorized attempts.
Strong identity controls stop many attacks before they start!
Method 4: Implementing Monitoring and Logging
Even well-secured systems need constant oversight because threats evolve quickly—and mistakes happen despite best intentions.
Set up logging at both hypervisor level (e.g., ESXi syslog configuration) AND inside each guest OS,
Forward logs centrally using SIEM solutions so you can correlate events across multiple sources,
Configure alerts for suspicious activities such as repeated failed login attempts—or unexpected changes in resource usage patterns,
Monitor file integrity within critical directories using tools like AIDE (Advanced Intrusion Detection Environment) on Linux guests,
Establish baseline performance metrics then watch closely for deviations that could signal compromise,
Review logs daily—even automated reports help catch issues early before damage spreads.
Proactive monitoring turns raw data into actionable intelligence!
Method 5: Encrypting VM Data and Storage
Encryption protects sensitive information even if someone gains physical access—or manages to bypass other defenses entirely.
Encrypt disks used by important VMs; Linux admins might choose LUKS/dm-crypt while Windows users rely on BitLocker Drive Encryption,
Many enterprise hypervisors now offer native encryption options—for example VMware vSphere supports full VM disk encryption managed via Key Management Servers (KMS),
Always store encryption keys securely—never hard-code them inside scripts nor leave them accessible within shared folders,
Consider encrypting backup files too so recovery points remain protected offsite/in transit,
Apply TLS encryption wherever possible when transmitting data between hosts/storage arrays/cloud endpoints,
Encryption doesn’t replace other controls—but adds another vital layer especially where compliance matters!
How to Backup Virtual Machine with Vinchin Backup & Recovery?
To ensure comprehensive protection after implementing security best practices, robust backup is indispensable. Vinchin Backup & Recovery is an enterprise-level solution supporting over 15 mainstream virtualization platforms—including VMware, Hyper-V, Proxmox VE, oVirt/RHV, OLVM, XCP-ng/XenServer, OpenStack, ZStack and more—which makes it suitable for diverse IT infrastructures. For VMware environments specifically, Vinchin Backup & Recovery delivers advanced integration alongside broad compatibility across hybrid deployments.
Among its extensive capabilities are forever incremental backup technology for efficient storage usage; granular restore allowing targeted file recovery; LAN-free backup options; CBT-based fast incremental backups where supported; and instant recovery functionality except on Hyper-V. These features collectively enhance operational resilience while minimizing downtime and optimizing resource consumption.
The intuitive web console makes protecting your environment straightforward:
Step 1: Select the VMware VM to back up
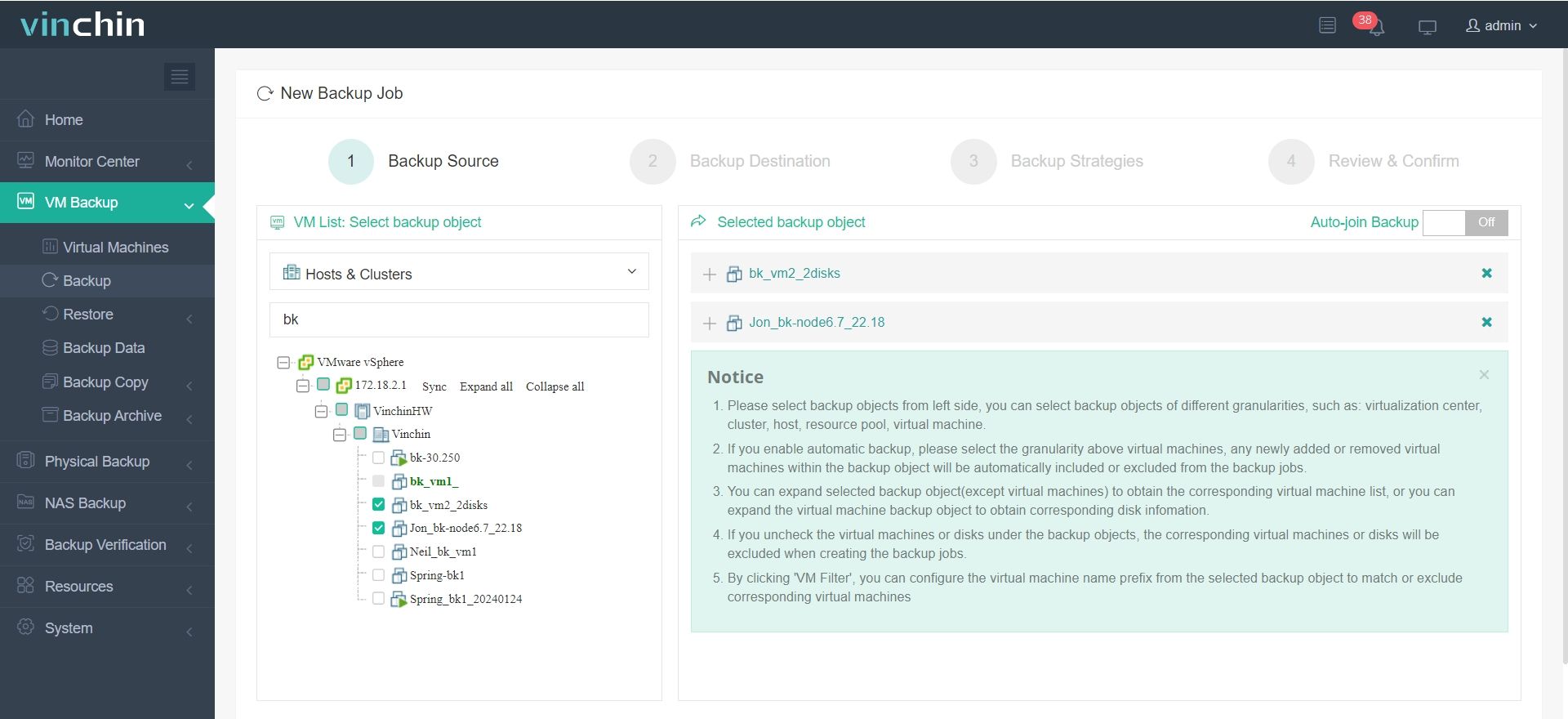
Step 2: Choose the backup storage
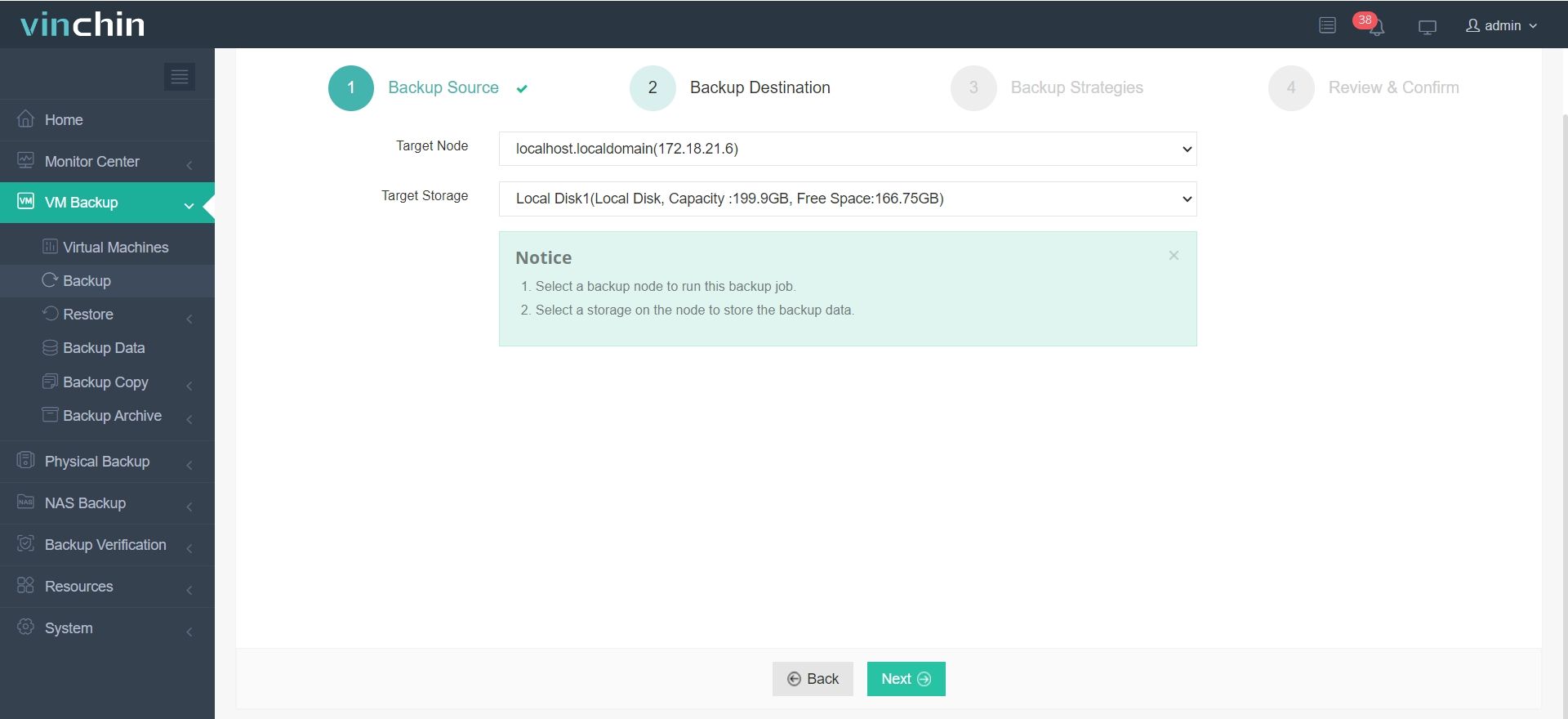
Step 3: Configure the backup strategy
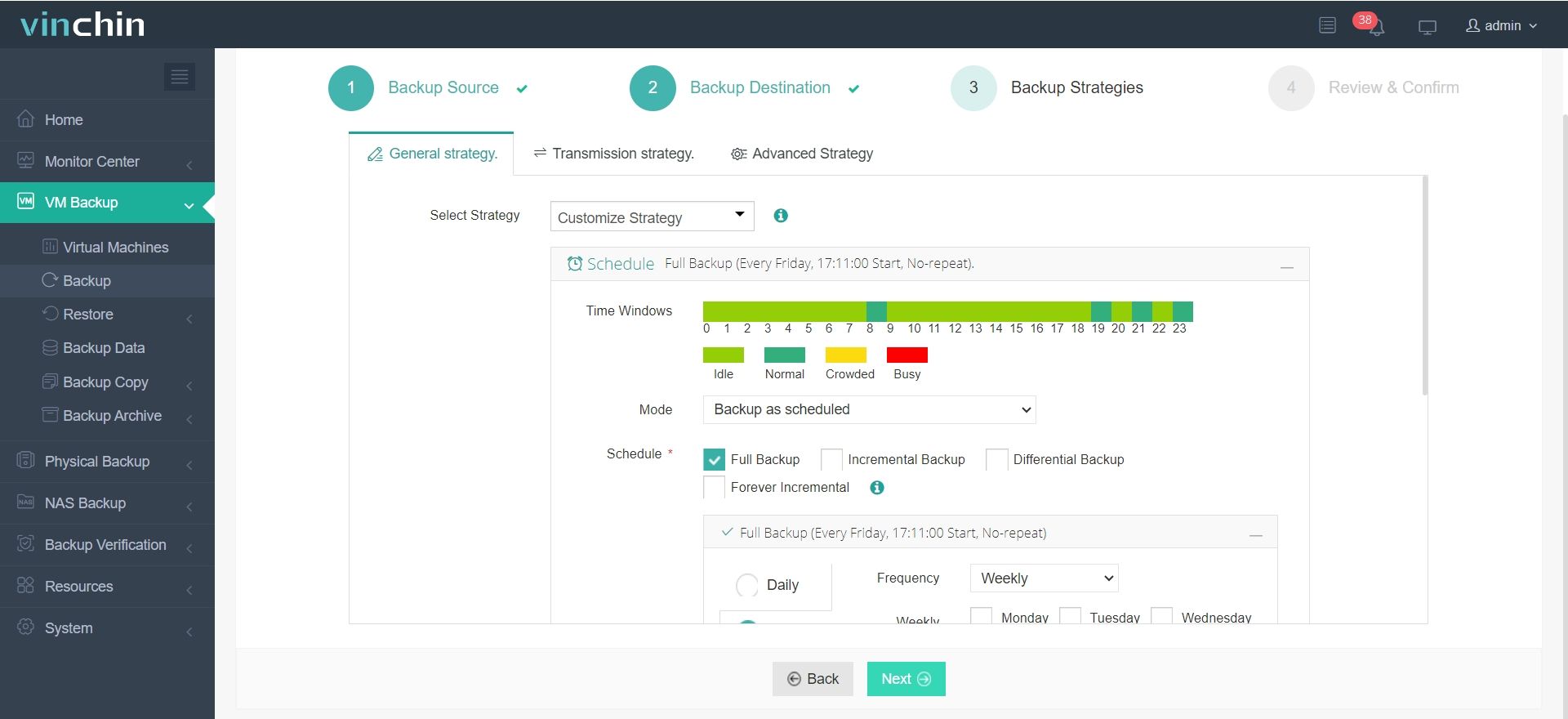
Step 4: Submit the job
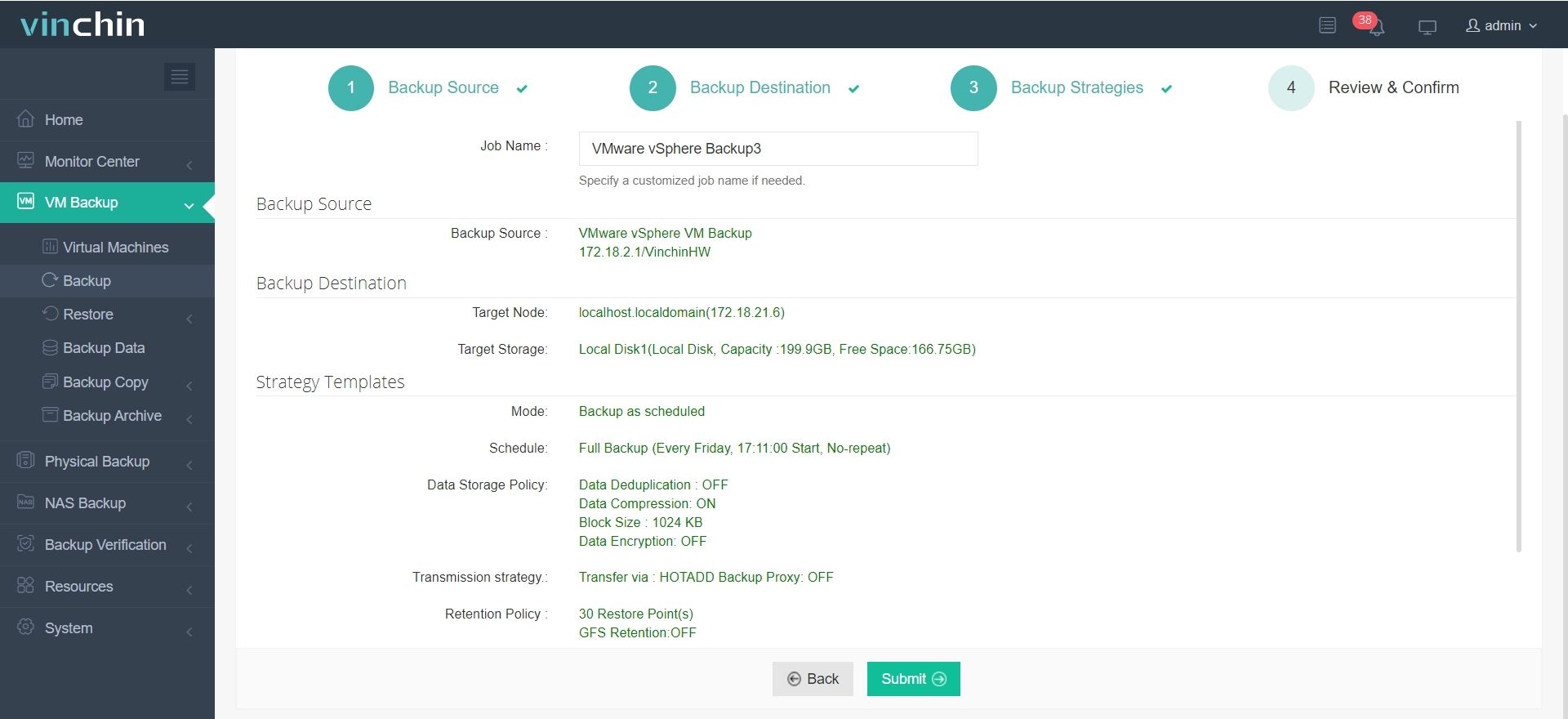
Trusted globally by thousands of organizations—with top ratings among enterprise data-protection solutions—Vinchin Backup & Recovery offers a fully featured 60-day free trial. Click below to experience its power firsthand.
How to Secure a Virtual Machine FAQs
Q1: What’s the safest way to connect remotely when managing Linux-based VMs?
A1: Use SSH key-based authentication over VPN/bastion host gateways—and never expose SSH port directly onto public internet-facing addresses.
Q2: How do I prevent excessive unused (“sprawl”) VMs becoming hidden risks?
A2: Audit inventory regularly decommission obsolete instances enforce approval workflow before provisioning new ones keep documentation current always!
Q3: How do I secure my hypervisor itself against attack?
A3: Install only required components apply patches promptly restrict management interfaces behind dedicated admin networks enable MFA/logging everywhere possible.
Conclusion
Securing virtual machines requires careful planning at every stage—from isolating networks through patch management/access controls—to ongoing monitoring/logging plus strong encryption practices layered throughout infrastructure design! Reliable backups provide peace-of-mind should anything slip through cracks along way—and Vinchin makes protecting those backups easier than ever before! Stay vigilant…your environment depends on it.
Share on:








