-
Why Ransomware Protection Matters in Enterprise Environments
-
How To Choose The Best Red Hat Virtualization Backup Solution for Ransomware Protection?
-
Vinchin Backup & Recovery: Enterprise-Grade Protection for Red Hat Virtualization
-
Best Red Hat Virtualization Backup Software FAQs
-
Conclusion
Which Red Hat Virtualization Backup Tool Best Protects Against Ransomware?
Vinchin Backup & Recovery is the ideal choice for defending against ransomware due to its powerful blend of immutable backups and air-gapped storage options, ensuring backup data remains untouchable by attackers. Its rapid restore capabilities further minimize costly downtime, while intuitive management and scalability provide strong, adaptive protection as your needs evolve.
Written by Vinchin Solution Team
Ransomware attacks have become one of the most serious threats facing enterprise IT. The right Red Hat Virtualization backup tool can make all the difference when it comes to protecting your business from these attacks. A solution that combines immutable backups, air-gapped storage, and fast recovery helps ensure your data stays safe—even if ransomware gets into your network. These features let you restore clean data quickly so you can get back to work with minimal downtime.
Ransomware resilience matters because it protects business continuity and compliance. If your backups are secure and easy to recover, you lower financial risk and avoid extended outages. This is why choosing a strong backup solution is essential for any organization running Red Hat Virtualization.
Why Ransomware Protection Matters in Enterprise Environments
Ransomware can cripple organizations by encrypting or deleting critical data. The impact goes far beyond lost files—it often means days or weeks of downtime, lost revenue, regulatory fines, and long-term damage to reputation. According to IBM’s Cost of a Data Breach Report 2023, average breach costs now exceed $4 million per incident worldwide. For ransomware specifically, Sophos found that average recovery costs reached $1.85 million in 2021.
● Attackers target backups first
Cybercriminals know that destroying backups leaves victims with no choice but to pay ransom demands. They often look for backup servers on the network before launching an attack on production systems. If they succeed in wiping out your recovery options, restoring operations becomes nearly impossible without paying up.
● Downtime leads to massive losses
Extended outages hurt productivity across every department. When critical applications go offline due to ransomware—and there are no clean backups—businesses face direct revenue loss plus indirect costs like missed deadlines or lost customer trust.
● Legal and compliance risks increase
Many industries must meet strict regulations around data protection (such as GDPR or HIPAA). Losing access to sensitive information can trigger audits or fines from regulators—sometimes even lawsuits from customers whose data was compromised.
● Repeat attacks become more likely
If attackers see that an organization paid a ransom once—or failed to improve defenses—they may strike again later using similar tactics.
These facts show why robust ransomware protection is not just “nice-to-have.” It’s a core requirement for modern IT operations running Red Hat Virtualization environments.
How To Choose The Best Red Hat Virtualization Backup Solution for Ransomware Protection?
Selecting a backup tool for Red Hat Virtualization requires careful attention to anti-ransomware capabilities. Each feature plays a unique role in defending against threats while supporting rapid recovery when needed most.
● Immutable storage stops tampering
Immutability means that once a backup is written, nobody—not even administrators—can change or delete it until its retention period ends. This prevents ransomware from erasing or corrupting your last line of defense. Many solutions implement immutability using WORM (Write Once Read Many) technology on local disks or S3 Object Lock on cloud storage. With immutable storage enabled through UI settings like Enable Immutability, you gain peace of mind knowing backups cannot be altered during their lock window.
● Air-gap options isolate critical copies
Air-gapped backups are stored separately from production networks—either physically (on removable drives) or logically (in isolated repositories). This makes it much harder for malware spreading through your environment to reach these protected copies. For example, scheduling regular offsite transfers using buttons like Create Offsite Copy Job ensures at least one set of clean data survives even if primary systems are breached.
● Rapid restore capabilities minimize downtime
When disaster strikes, every minute counts. Solutions offering instant VM recovery let you boot virtual machines directly from backup images using actions such as Instant Restore, reducing downtime from hours to minutes. Granular file-level restores allow quick retrieval of individual documents without waiting for full system rebuilds—a lifesaver during urgent incidents.
● Comprehensive reporting detects early warning signs
Backup anomalies—like sudden job failures or unexpected deletions—often signal active threats inside your environment. Real-time monitoring dashboards with alerts triggered by events such as “Backup Job Failed” help administrators spot trouble before it spreads further.
● Scalability supports growing environments
As infrastructure expands across more hosts and VMs, your backup solution must scale smoothly without introducing new risks or management headaches. Features like centralized policy management under tabs such as Policy Settings, along with flexible licensing models based on VM count rather than hardware limits, keep protection strong as needs evolve over time.
Choosing tools that combine these elements ensures both security today and adaptability tomorrow—all while keeping operations simple enough for busy IT teams managing Red Hat Virtualization deployments at scale.
Vinchin Backup & Recovery: Enterprise-Grade Protection for Red Hat Virtualization
For organizations seeking robust protection for Red Hat Virtualization environments, Vinchin Backup & Recovery stands out as an enterprise-level virtual machine backup solution supporting over 15 mainstream virtualization platforms—including RHV/oVirt first and foremost alongside VMware, Hyper-V, Proxmox, XCP-ng, XenServer, OpenStack, ZStack and more diverse infrastructures found in modern datacenters.
Vinchin Backup & Recovery offers agentless VM protection across supported hypervisors; advanced features such as CBT tracking accelerate incremental jobs; LAN-free backup boosts performance by bypassing production LAN; instant recovery enables near-zero-downtime restoration; granular restore allows precise file-level retrieval—all contributing toward efficient operations and minimized risk exposure.
The intuitive web console streamlines workflow:
Step 1: Select the RHV VM(s) you wish to protect;
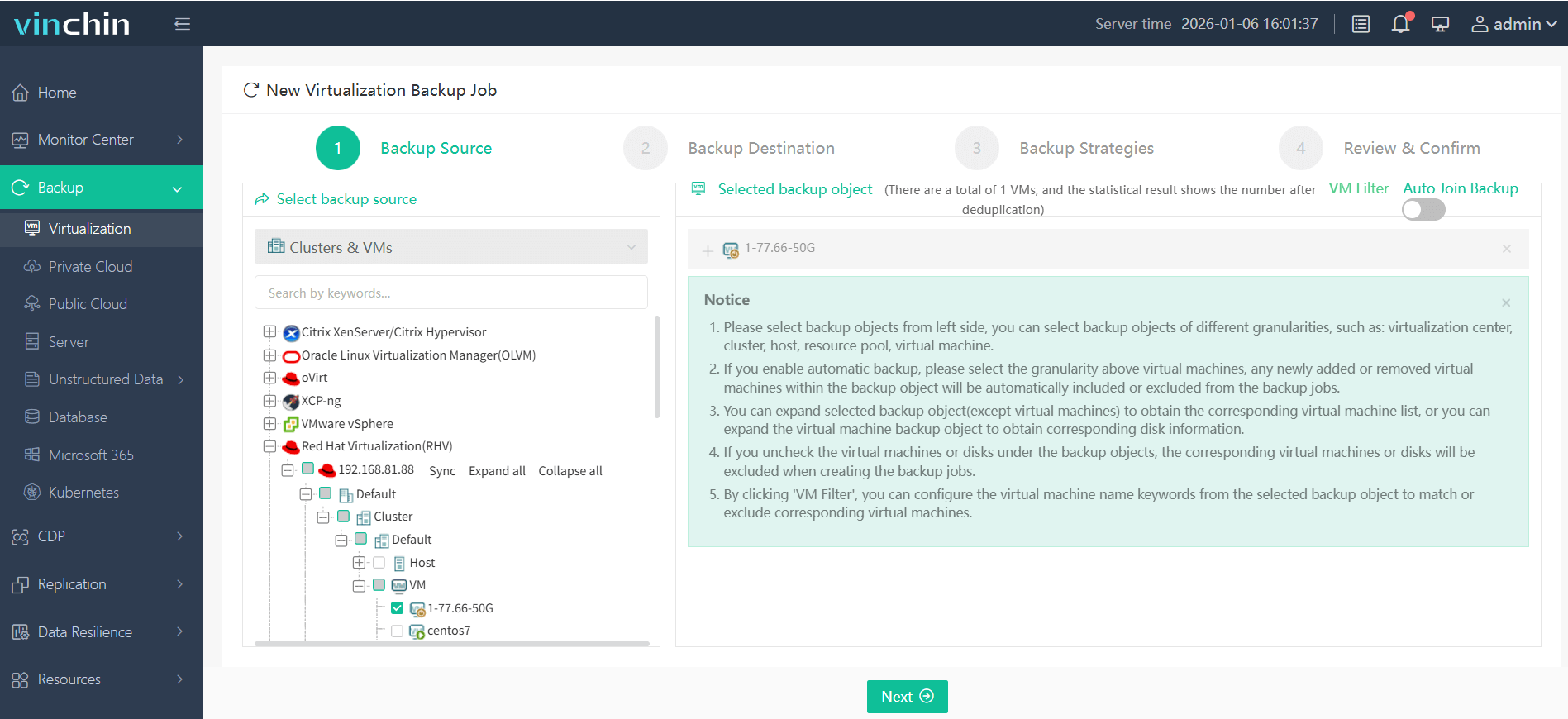
Step 2: Choose appropriate backup storage;
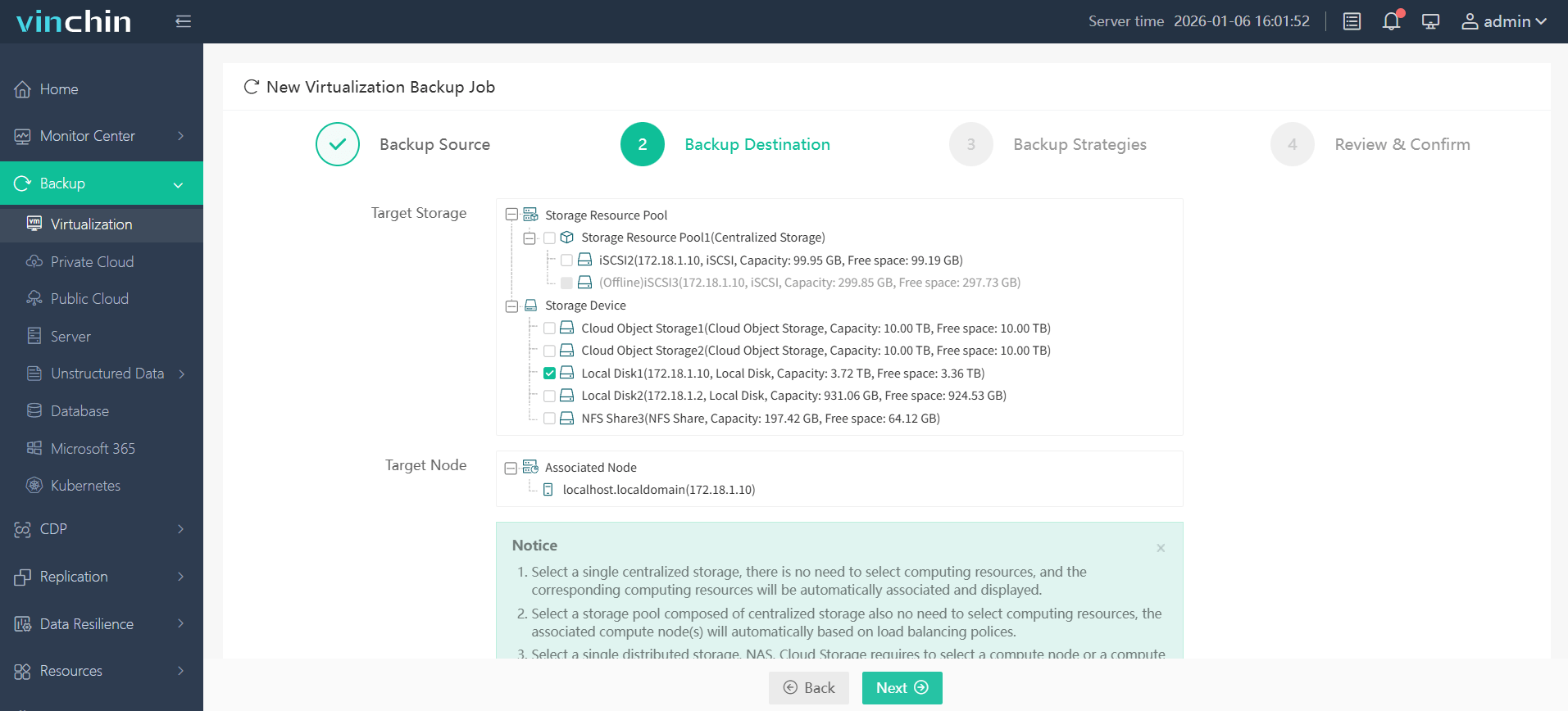
Step 3: Configure strategy including schedule and retention policies;
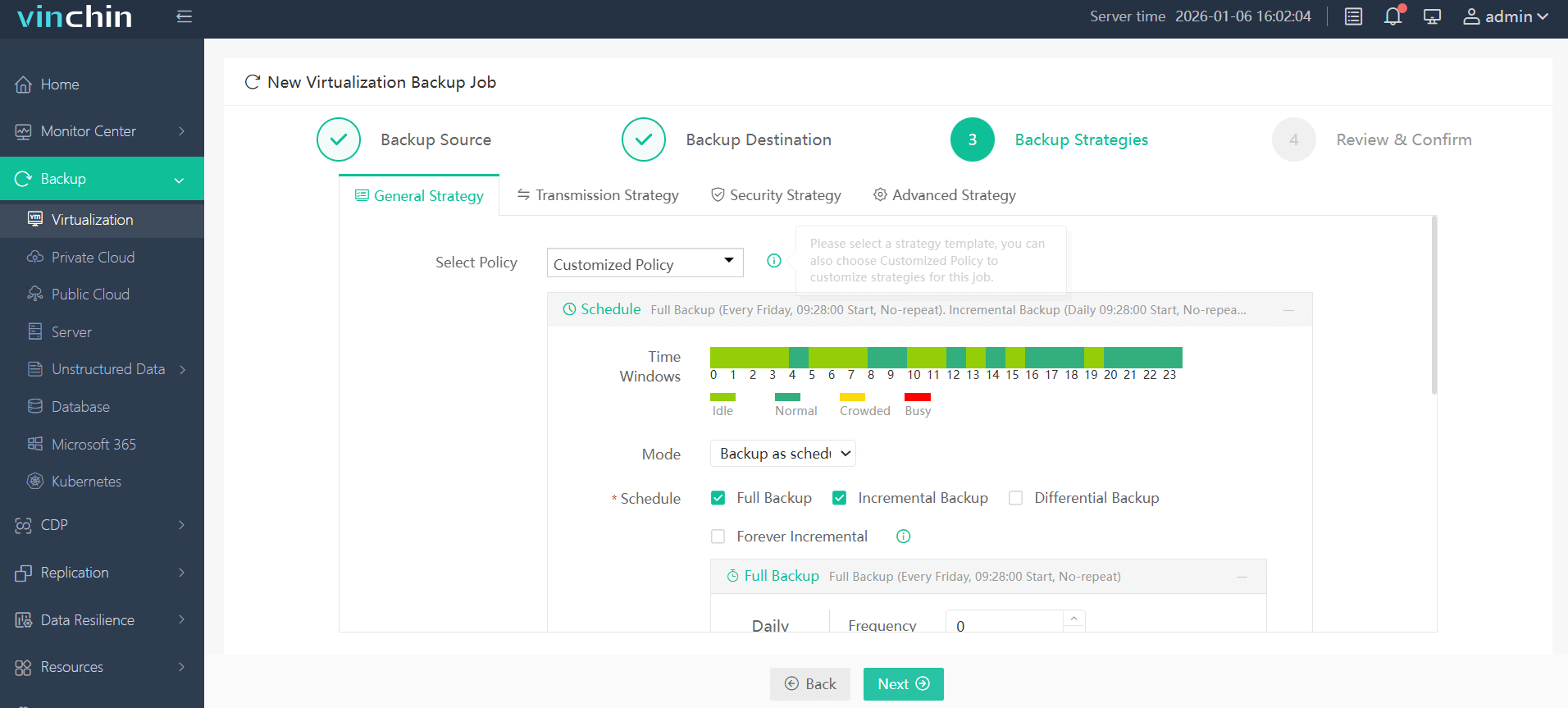
Step 4: Submit the job with just a few clicks.
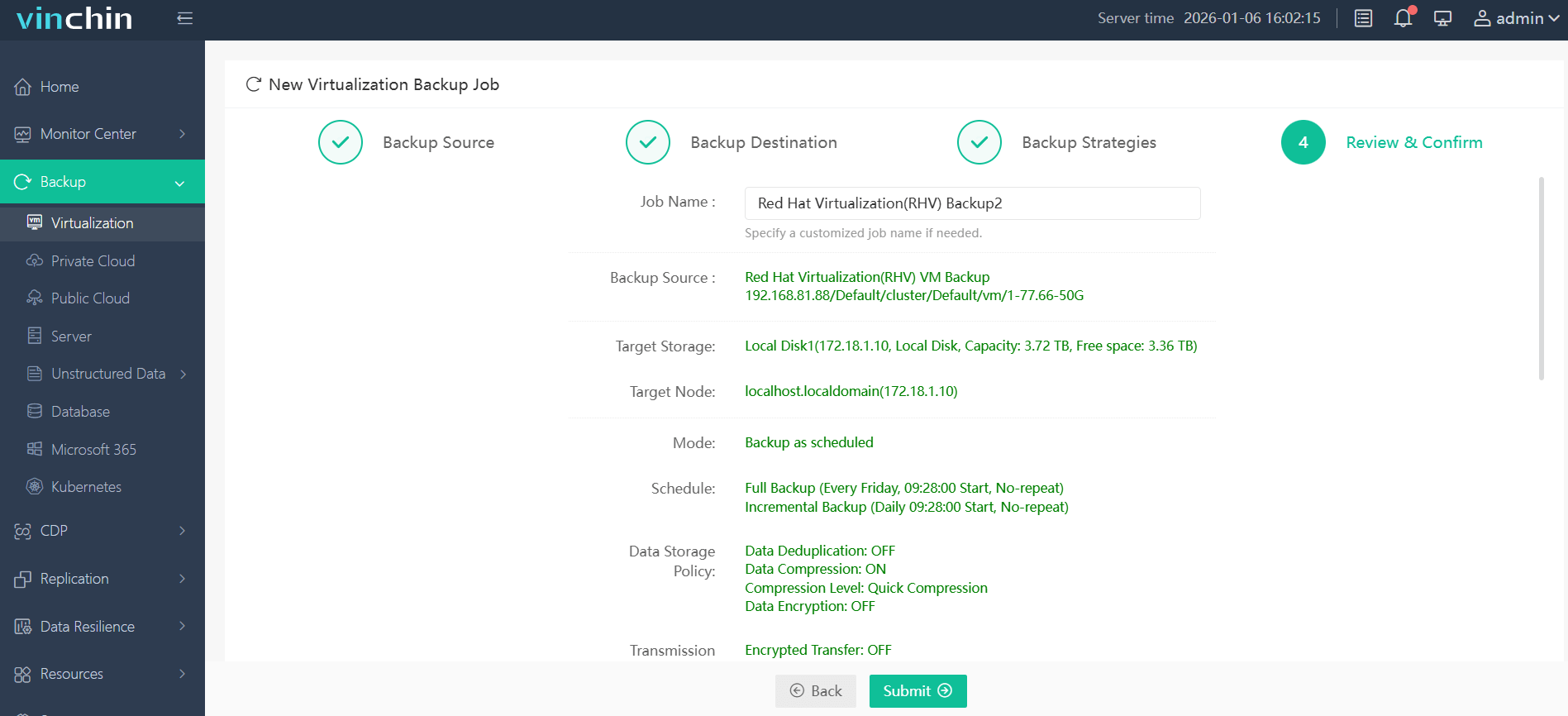
With global recognition among enterprise users and top industry ratings, Vinchin Backup & Recovery delivers proven reliability—try its full-featured 60-day free trial today by clicking below!
Best Red Hat Virtualization Backup Software FAQs
Q1: How does a backup solution protect against ransomware?
A1: By storing immutable copies that cannot be changed—even by admins—during their retention period using write-protection mechanisms like WORM disks/object locks. Air-gapped repositories add another layer since malware cannot reach them over normal network paths even if production systems fall victim first!
Q2: Is air-gapped backup necessary?
A2: Yes! Air-gapping significantly lowers risk because isolated repositories remain untouched even when attackers breach main networks; this isolation blocks lateral movement typical in modern multi-stage attacks according to CISA guidance!
Q3: What role does rapid recovery play in ransomware defense?
A3: Rapid restore lets businesses recover clean VMs/files almost instantly after infection—minimizing costly downtime/disruption compared with slow manual rebuilds! Fast action also helps limit spread/damage since infected nodes can be replaced quickly before malware jumps elsewhere!
Q4: Can scalable solutions improve long-term ransomware resilience?
A4: Absolutely! Scalable tools adapt easily as infrastructure grows/shrinks; centralized controls/policy templates mean consistent security everywhere without extra admin burden—a key factor cited by NIST best practices!
Conclusion
Immutability, air-gapping, rapid restore—all matter most when fighting ransomware in Red Hat Virtualization setups. Vinchin delivers these essentials so you stay resilient while meeting business goals securely every day.
Share on:









