-
What Is Oracle RMAN Backup Encryption?
-
Why Encrypt Oracle Backups?
-
Method 1: Transparent Encryption in RMAN
-
Method 2: Password-Based Encryption in RMAN
-
Method 3: Dual-Mode Encryption in RMAN
-
Choosing the Right Encryption Mode
-
Verifying Your Backup Encryption
-
Centralized Protection for Oracle Backups with Vinchin Backup & Recovery
-
Oracle RMAN Backup Encryption FAQs
-
Conclusion
Protecting your Oracle database backups is more critical than ever. Data breaches can lead to regulatory fines, reputational damage, or even direct data loss. If someone gains access to your backup files, they could steal sensitive information—unless those backups are encrypted. Oracle Recovery Manager (RMAN) includes built-in backup encryption that helps keep your data safe during storage or transfer. But how does Oracle RMAN backup encryption work? What options do you have? Let’s break it down step by step so you can make informed decisions for your environment.
What Is Oracle RMAN Backup Encryption?
Oracle RMAN backup encryption lets you encrypt database backup sets at creation. When enabled, RMAN writes backup data in an encrypted format that only authorized users—with the right keys or password—can restore and read. This protects your data if backups are lost or stolen.
RMAN supports three main encryption modes: transparent encryption (using an Oracle keystore), password-based encryption (using a user-supplied password), and dual-mode encryption (combining both methods). Each mode offers different levels of convenience and security depending on your needs.
Transparent encryption uses a software keystore managed by Oracle. Password-based encryption relies on a session-specific password. Dual-mode allows either method to decrypt the same backup set. Choosing wisely ensures strong protection against unauthorized access.
Why Encrypt Oracle Backups?
Encrypting your Oracle backups goes beyond compliance—it addresses real threats facing modern IT operations teams. Backups often reside offsite, on tape, or in cloud storage where physical control is limited. Unencrypted files are easy targets for attackers or malicious insiders.
Encryption ensures only authorized users can restore backups—even if someone steals the files themselves. It also helps meet strict regulatory requirements like GDPR or HIPAA and aligns with internal security policies common in enterprise environments. Without proper encryption, any robust backup strategy has a glaring vulnerability.
Why risk exposing sensitive business data when secure options exist?
Method 1: Transparent Encryption in RMAN
Transparent encryption is often preferred for its simplicity and automation within trusted environments. It uses an Oracle software keystore—sometimes called a wallet—to store master keys securely outside of regular database files.
Before using transparent encryption with RMAN:
First, configure the keystore for your database:
1. Set up ENCRYPTION_WALLET_LOCATION or WALLET_ROOT in your initialization parameter file to specify where the keystore will be stored.
2. Use SQL*Plus to run:
ADMINISTER KEY MANAGEMENT CREATE KEYSTORE '/path/to/keystore' IDENTIFIED BY 'keystore_password'; ADMINISTER KEY MANAGEMENT OPEN KEYSTORE IDENTIFIED BY 'keystore_password'; ADMINISTER KEY MANAGEMENT SET KEY IDENTIFIED BY 'keystore_password' WITH BACKUP;
Replace /path/to/keystore and 'keystore_password' as needed for your environment.
Once configured:
3. In RMAN, enable default database-wide backup encryption:
CONFIGURE ENCRYPTION FOR DATABASE ON;
4. To specify an algorithm other than default (AES256 for recent versions), use:
CONFIGURE ENCRYPTION ALGORITHM 'AES256';
5. Run standard backup commands such as:
BACKUP DATABASE;
With this setup, all new backups will be encrypted automatically using keys from the open keystore—no need to enter passwords each time.
When restoring encrypted backups:
If you use an auto-login keystore (cwallet.sso), decryption happens seamlessly when the keystore is available and open during restore operations. For password-protected wallets (ewallet.p12), ensure you open them before starting any restore process.
Remember: Losing access to your keystore means losing access to all encrypted backups created with it! Always back up your wallet separately from regular database files—and never store wallet copies alongside encrypted backups themselves.
Method 2: Password-Based Encryption in RMAN
Password-based encryption works well when sharing or moving backups between sites that do not share a common keystore infrastructure—for example, shipping tapes offsite or transferring archives across domains.
To create a password-encrypted backup:
1. Start RMAN and connect to your target database
2. Set session-level password-based encryption:
SET ENCRYPTION ON IDENTIFIED BY 'your_password' ONLY;
Replace 'your_password' with something strong; ONLY means no other decryption method applies
3. Run standard commands such as:
BACKUP DATABASE;
Restoring requires supplying that same password:
1. Start RMAN again
2. Enter decryption command:
SET DECRYPTION IDENTIFIED BY 'your_password';
3. Restore as usual:
RESTORE DATABASE;
A few cautions apply here too:
If you forget or lose this password—even years later—the associated encrypted backups become unrecoverable! Unlike transparent mode, there’s no persistent configuration; passwords must be set every session before running relevant commands.
No special wallet setup is needed for this approach—but always document passwords securely using approved enterprise procedures!
Method 3: Dual-Mode Encryption in RMAN
Dual-mode combines both approaches above into one flexible solution—a smart choice if you want maximum portability without sacrificing automation inside trusted environments.
To create a dual-mode encrypted backup:
1. Connect via RMAN
2. Use this command (note absence of ONLY):
SET ENCRYPTION ON IDENTIFIED BY 'your_password'; BACKUP DATABASE;
This creates a single encrypted set restorable either by opening the original keystore or providing 'your_password'. That way DR restores work even if one authentication factor becomes unavailable—a valuable safeguard against operational surprises!
Dual-mode does require careful coordination between teams managing wallets versus those handling passwords—but it delivers resilience many enterprises demand today.
Choosing the Right Encryption Mode
Selecting which mode fits best depends on how you operate day-to-day—and what risks matter most to you.
Transparent Encryption suits automated daily jobs within datacenters where wallet management is routine practice; restores happen quickly since no manual input is needed unless disaster strikes both primary site and wallet location simultaneously.
Password-Based Encryption shines when sending archives offsite—or sharing them across organizations lacking shared infrastructure—since only knowledge of that specific password enables recovery anywhere else worldwide (assuming compatible hardware/software).
Dual-mode gives flexibility: local admins enjoy seamless restores via wallet while remote DR teams retain fallback access through documented passwords should central systems fail entirely—a rare but critical scenario worth planning for!
Ask yourself: How portable must my backups be? Who manages my keys? Am I prepared if one layer fails unexpectedly? The answers guide which mode makes sense now—and what changes might help tomorrow as regulations evolve further still!
Verifying Your Backup Encryption
After configuring everything above—you’ll want proof things work as expected! Luckily checking status takes just moments using built-in tools:
In RMAN, list recent jobs showing their algorithms used:
LIST BACKUP OF DATABASE;
Encrypted sets display algorithm details directly beside each entry (“AES256”, etc.).
For deeper checks inside SQL*Plus try querying system views like V$BACKUP_SET_DETAILS, looking at columns such as ENCRYPTED, ENCRYPTION_ALGORITHM, etc., e.g.,
SELECT SESSION_KEY,BACKUP_TYPE,BACKUP_SET_ID, ENCRYPTED, ENCRYPTION_ALGORITHM FROM V$BACKUP_SET_DETAILS WHERE COMPLETION_TIME > SYSDATE - 7;
This confirms whether recent jobs truly used intended settings—giving peace of mind before audits arrive!
Always verify after changing configurations—or periodically per policy—to catch silent misconfigurations early rather than after disaster strikes!
Centralized Protection for Oracle Backups with Vinchin Backup & Recovery
To further streamline secure management of encrypted Oracle databases, consider Vinchin Backup & Recovery—a professional enterprise-level solution supporting leading platforms including Oracle, MySQL, SQL Server, MariaDB, PostgreSQL, PostgresPro, and TiDB databases (with full support for advanced features on each). Key capabilities include incremental backup for efficient storage usage; advanced source-side compression; batch database backup; robust retention policies including GFS; and comprehensive storage protection against ransomware threats—all designed to maximize reliability while minimizing administrative effort.
The intuitive web console makes safeguarding encrypted Oracle databases straightforward:
Step 1: Select the Oracle database to back up
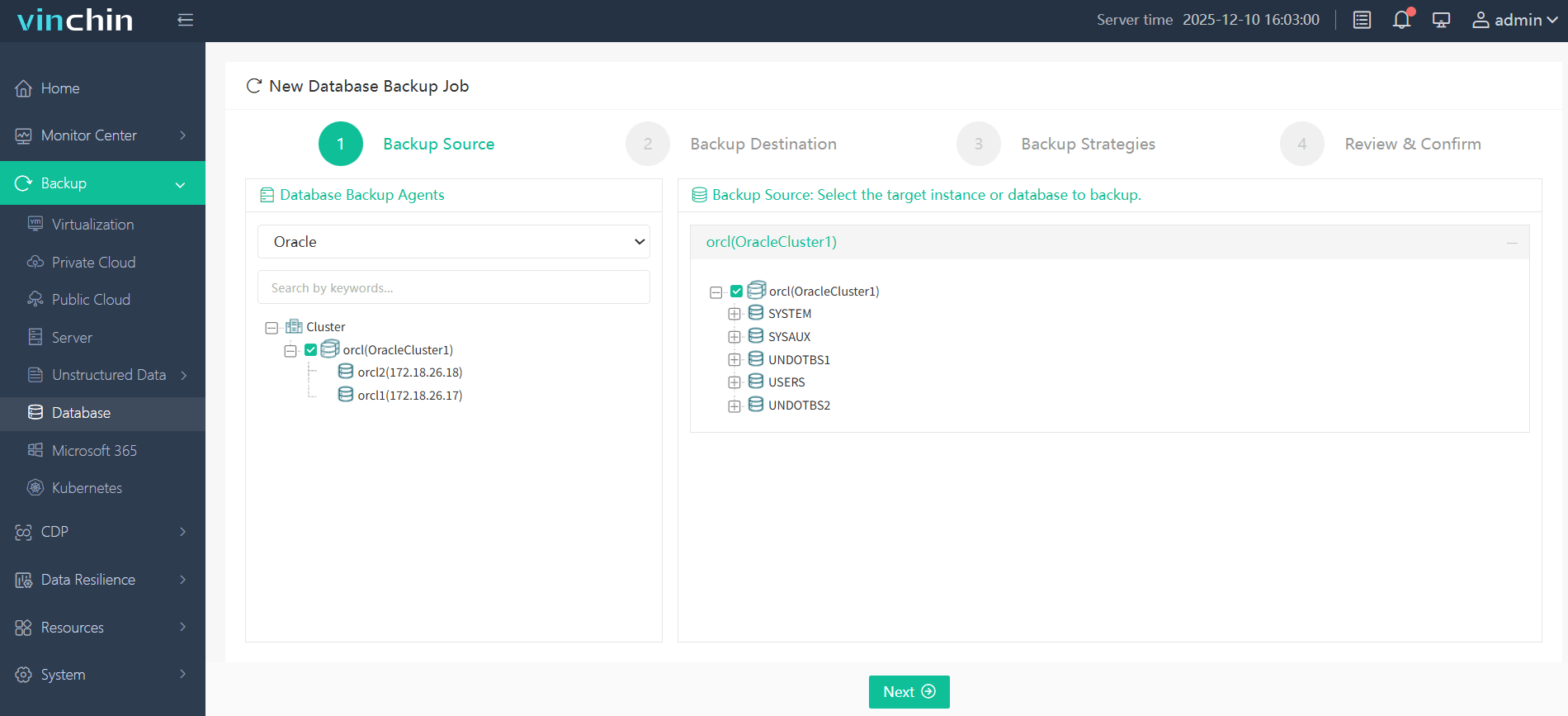
Step 2: Choose the backup storage
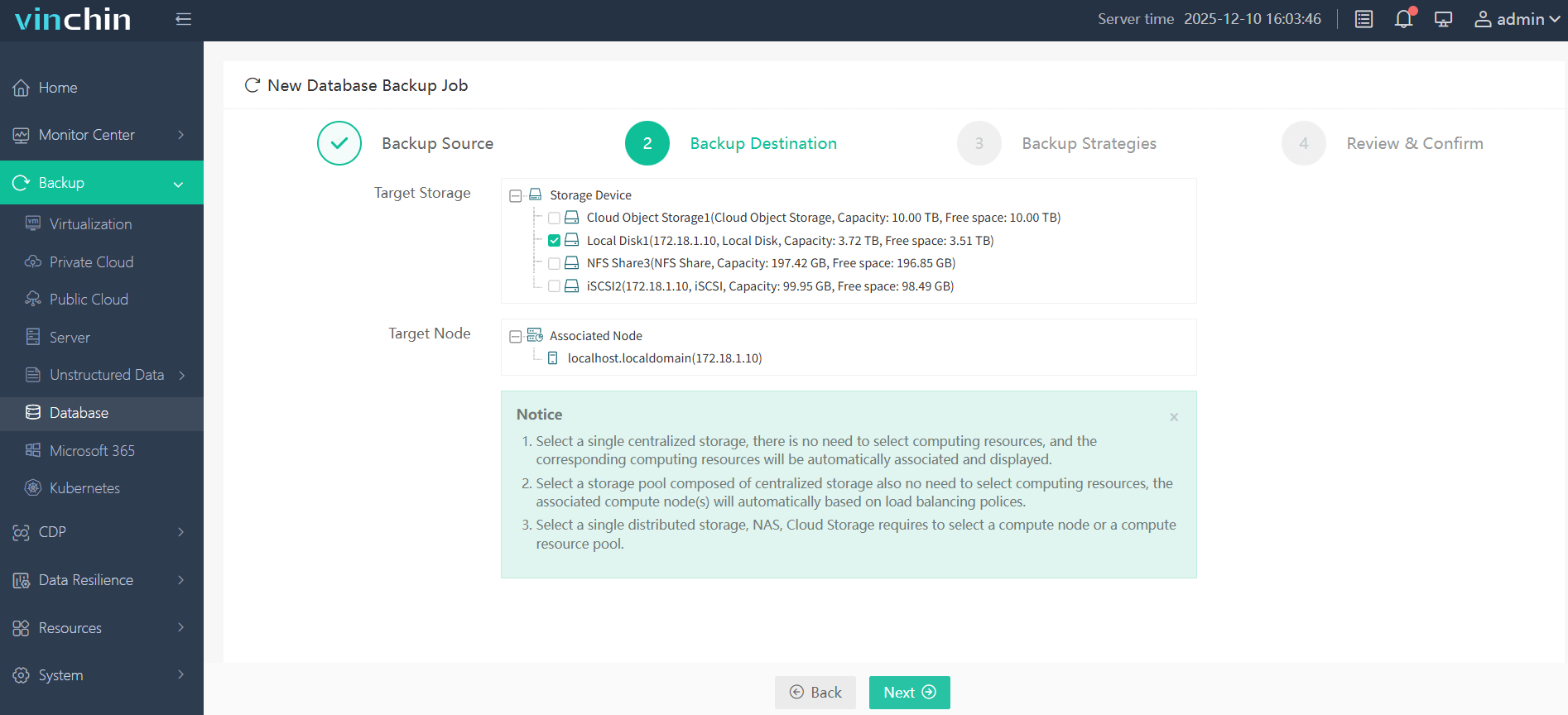
Step 3: Define the backup strategy
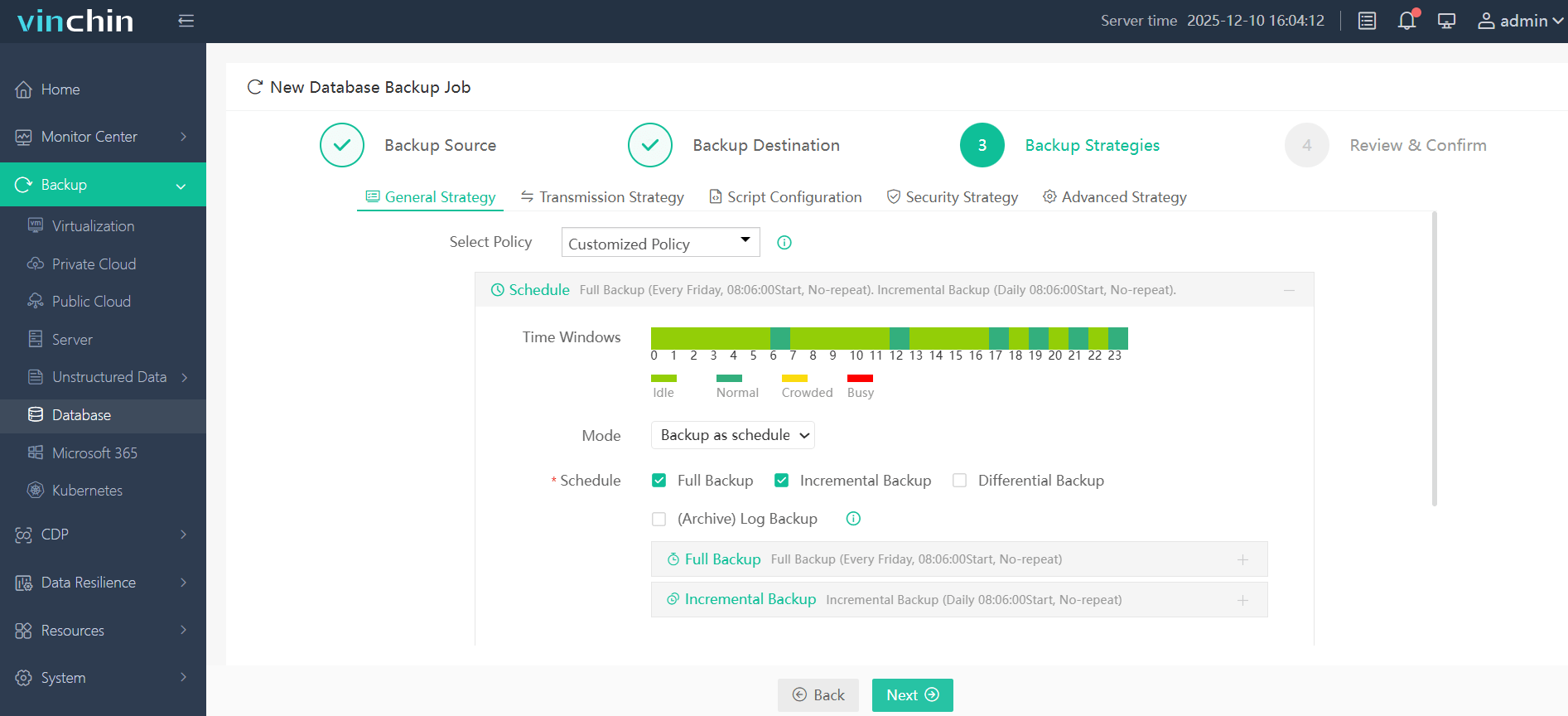
Step 4: Submit the job
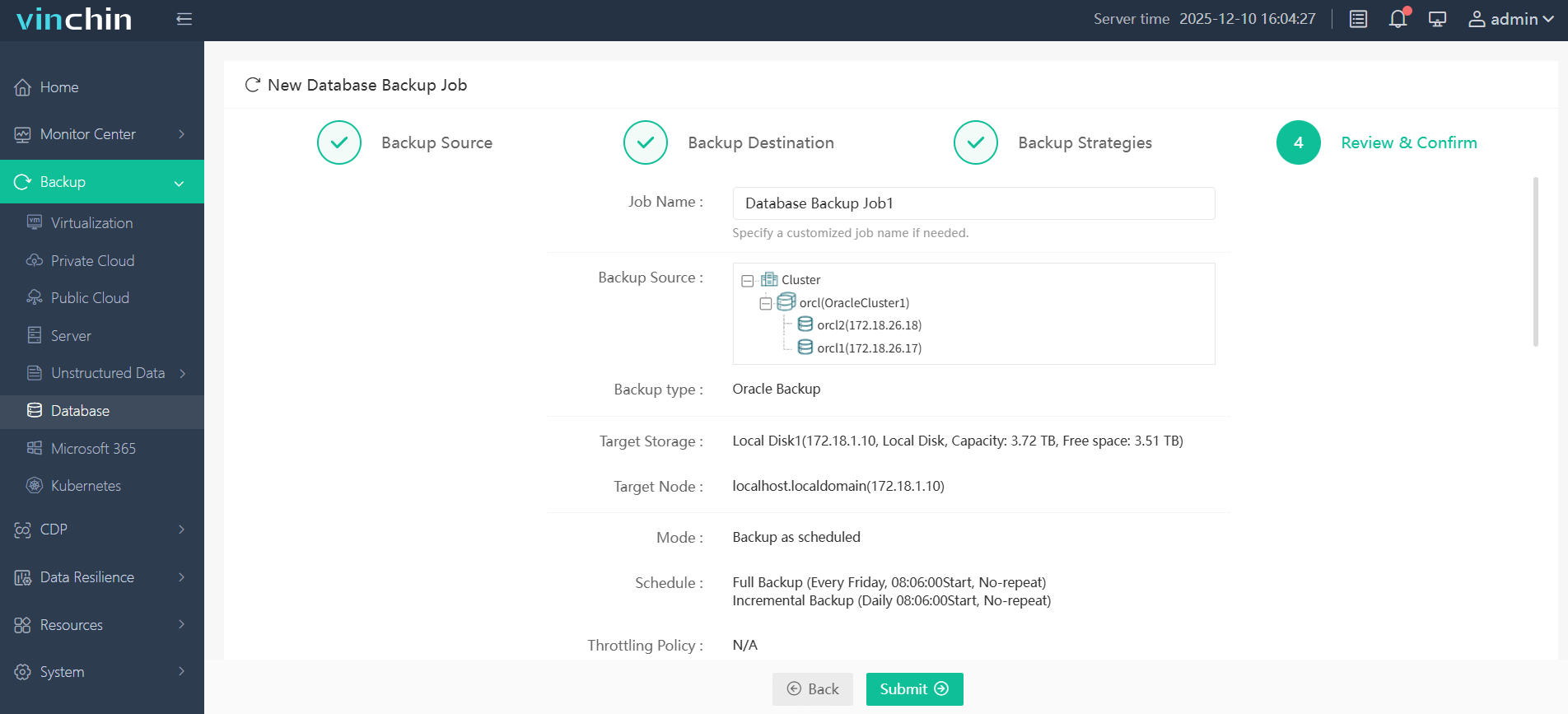
Vinchin Backup & Recovery enjoys global recognition among enterprises seeking reliable data protection solutions—try every feature free for 60 days and see why customers rate it so highly worldwide by clicking below to download now!
Oracle RMAN Backup Encryption FAQs
Q1: Can I change my chosen algorithm later without affecting old backups?
A1: Yes; new settings affect future jobs only—old sets remain tied to their original algorithms until replaced or deleted.
Q2: Does enabling RMAN encryption slow down my nightly jobs significantly?
A2: There may be some CPU overhead depending on hardware; test performance impacts before deploying widely but most modern servers handle AES128/AES256 efficiently today.
Q3: How do I confirm my latest full DB dump was actually encrypted last night?
A3: In RMAN, run LIST BACKUP OF DATABASE then check output shows "Encrypted" plus desired algorithm next to each entry.
Conclusion
Encrypting Oracle RMAN backups protects vital business information from theft or misuse while helping meet compliance goals easily over time—all without major workflow disruption once configured properly! Vinchin makes managing these secure processes straightforward so every admin stays confident about recovery readiness every day.
Share on:









