-
What Is psql in PostgreSQL?
-
How to Connect Locally to a PostgreSQL Database Using psql?
-
How to Remotely Connect to a PostgreSQL Database Using psql?
-
How to Use Password Authentication When Connecting with psql?
-
Protecting Your PostgreSQL Database With Vinchin Backup & Recovery
-
psql Connect to Database FAQs
-
Conclusion
Connecting to a PostgreSQL database is a basic but vital skill for any operations administrator. The psql command-line tool is the standard way to interact with PostgreSQL, whether you are working on a local server or managing remote systems. With psql, you can run queries, check system health, perform backups, or troubleshoot issues—all from your terminal window. In this guide, you’ll learn how to use psql to connect to databases in different scenarios: from simple local logins to secure remote access with password authentication and encryption. Ready to get started?
What Is psql in PostgreSQL?
psql is the official interactive terminal for PostgreSQL databases. It lets you run SQL queries directly against your database server and manage objects such as tables or users without leaving your shell environment. When you launch psql, you can connect to any accessible database instance—local or remote—and execute commands in real time.
This tool works across Linux, Windows, and macOS platforms and comes bundled with every standard PostgreSQL installation. Whether you're building scripts or performing ad-hoc maintenance tasks, psql gives you direct control over your data.
How to Connect Locally to a PostgreSQL Database Using psql?
Local connections are often the simplest way to access your PostgreSQL database—especially during development or when working on single-server deployments. By default, psql uses your operating system username as both the database username and the target database name unless told otherwise.
To connect as the default postgres user on most Linux systems:
1. Open your terminal.
2. Type sudo --login --user=postgres and press Enter.
3. At the new shell prompt (now as postgres), type psql and press Enter.
If you'd rather not open a new shell session just for this purpose:
sudo --login --user=postgres psql
On Windows systems:
1. Open Command Prompt.
2. Run:
psql -U postgres
You may be prompted for a password if required by server settings.
Once connected successfully, you'll see the familiar postgres=# prompt where you can issue SQL statements or meta-commands like \l (list databases) or \q (quit).
Using Connection Parameters for Flexibility
Sometimes you need more control than what defaults provide—for example if you're connecting as another user or targeting a different database instance running on an alternate port.
You can specify these options directly in your command line invocation:
To choose another user:
psql -U myuser
To select a specific database:
psql -d mydatabase
To set an alternative port (if not using default 5432):
psql -p 5433 -U myuser -d mydatabase
Combining these options gives full flexibility:
psql -U analyst -d salesdb -p 5434
This approach is handy when managing multiple projects or test environments that use non-default configurations.
How to Remotely Connect to a PostgreSQL Database Using psql?
Remote connections let administrators manage production servers or cloud-hosted instances from anywhere—but require careful setup for security reasons.
Before connecting remotely:
Ensure that
listen_addressesinpostgresql.confincludes either'localhost', specific IPs needed by clients, or' * 'if absolutely necessary (though this is less secure). After changing this setting, restart PostgreSQL so changes take effect.Confirm that firewalls allow inbound traffic on port 5432, unless you've configured another port.
Edit
pg_hba.confso it permits access from your client machine's IP address using appropriate authentication methods (md5,scram-sha-256, etc.).
The basic syntax for remote connection is:
psql -h <hostname> -p <port> -U <username> -d <database>
For example:
psql -h db.example.com -p 5432 -U dbuser -d mydatabase
After pressing Enter, you'll be prompted for your password if required by server policy.
Alternatively, use a connection string format:
psql "postgresql://dbuser:password@db.example.com:5432/mydatabase"
This method allows all parameters—including passwords—to be specified inline; it's especially useful in scripts but should be used carefully due to security concerns about exposing credentials in process lists or logs.
Before attempting connection via psql, it's wise to check network connectivity using tools like:
telnet db.example.com 5432 # Or nc db.example.com 5432
A successful response means network routing is correct; otherwise investigate firewall rules or hostnames further.
Leveraging SSL/TLS for Encrypted Connections
Security-conscious environments demand encrypted communication between clients and servers—especially over public networks like the internet.
PostgreSQL supports SSL/TLS natively; enabling it requires configuration changes on both server and client sides:
1. On the server side: Set up certificates (server.crt, server.key) in your data directory; enable SSL support by setting ssl = on in postgresql.conf.
2. On client side (psql): Add parameter
--set=sslmode=require
Or include it within connection strings:
psql "host=db.example.com port=5432 user=dbuser dbname=mydatabase sslmode=require"
Other valid values for sslmode:
"prefer"(default),"require","verify-ca","verify-full"
Using SSL ensures all data—including login credentials—is encrypted during transit between client and server nodes.
How to Use Password Authentication When Connecting with psql?
Password authentication protects sensitive data by ensuring only authorized users gain access—especially important when connecting remotely across potentially insecure networks.
There are several ways you can provide passwords securely when using psql:
By default—if no password is supplied—the tool prompts interactively after connection attempt fails due to missing credentials.
Force this prompt explicitly with option:
psql -h db.example.com -U dbuser -d mydatabase -W
Environment Variable Method
Set environment variable before launching session:
export PGPASSWORD='yourpassword' psql -h db.example.com -U dbuser -d mydatabase
While convenient for automation tasks such as cron jobs or CI/CD pipelines,
be aware that environment variables may leak into process listings visible via commands like ps aux. For better safety consider .pgpass.
.pgpass File Method
Store credentials securely inside .pgpass file located at $HOME/.pgpass (Linux/macOS)
or %APPDATA%\postgresql\pgpass.conf (Windows). Each line follows format:
hostname:port:database:username:password
Example entry:
db.example.com:5432:*:analyst:mypassword123!
Set permissions strictly so only owner has read/write rights (chmod 600 ~/.pgpass). If present,
psql reads this file automatically—no need for manual input during scripted operations.
Security Best Practices When Handling Passwords
Never share passwords openly—even within teams—and avoid embedding them directly into scripts checked into version control systems.
Always restrict .pgpass files’ permissions so only trusted users have access;
rotate passwords regularly according to organizational policy.
Protecting Your PostgreSQL Database With Vinchin Backup & Recovery
Beyond mastering connectivity techniques, robust backup strategies are essential for safeguarding critical data against loss and downtime. Vinchin Backup & Recovery stands out as an enterprise-grade solution supporting today’s leading databases—including first-class protection for PostgreSQL alongside Oracle, MySQL, SQL Server, MariaDB, PostgresPro, and MongoDB environments. For PostgreSQL users specifically, Vinchin Backup & Recovery delivers incremental backup capabilities, batch database backup management, data retention policies including GFS retention policy support, scheduled backups with ransomware protection built-in, plus seamless restore-to-new-server functionality—all designed around reliability and operational efficiency while minimizing storage costs through advanced compression options where applicable.
The intuitive web console makes protecting your PostgreSQL environment straightforward—just follow four steps:
1. Go to Database Backup> Backup, and select the data source from the licensed database list.
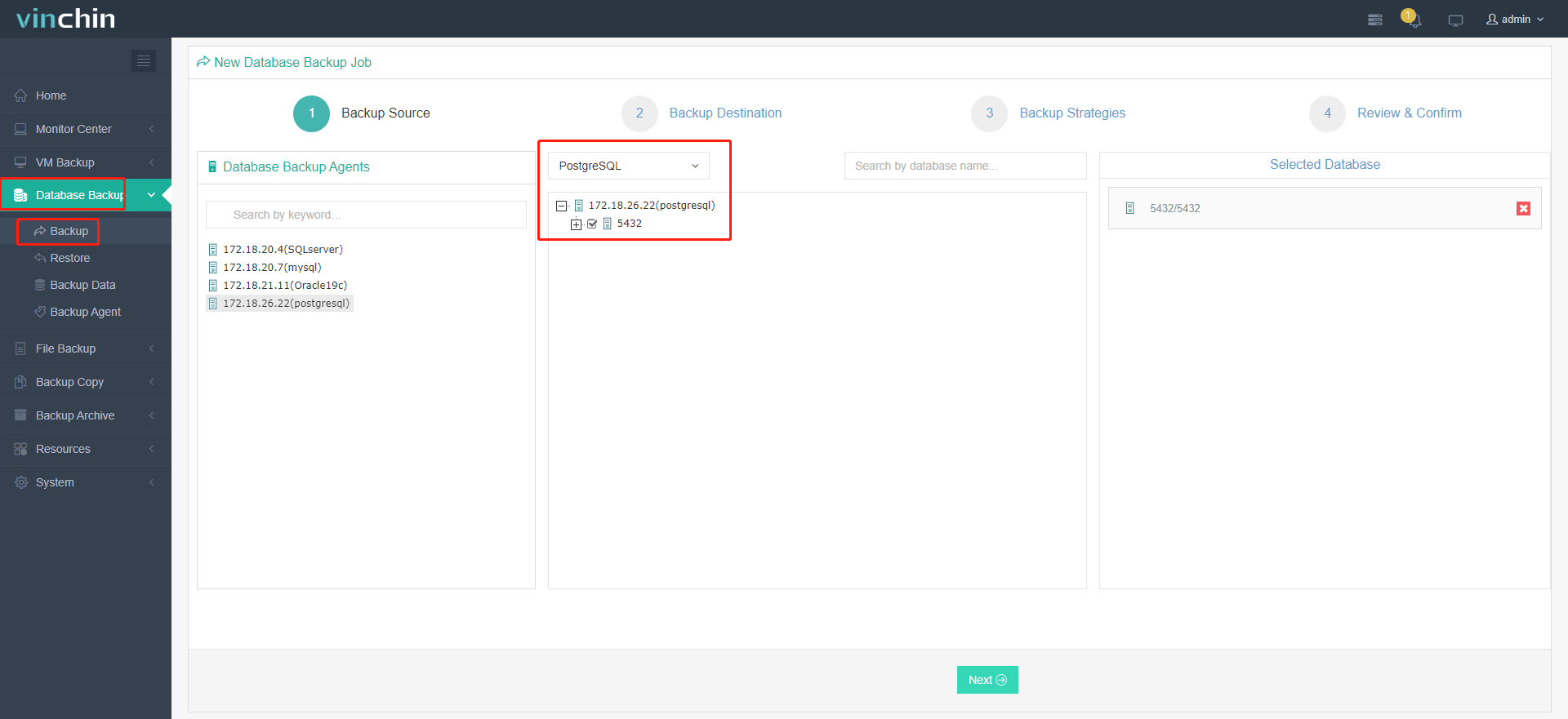
2. Select the target node and storage for the job.
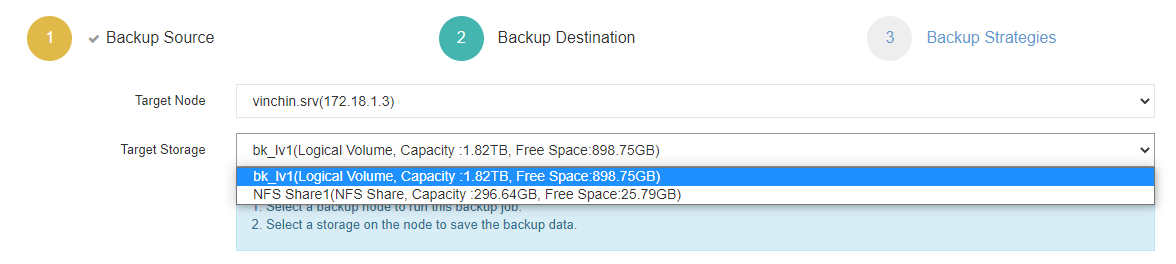
3. Set up desired backup strategies.
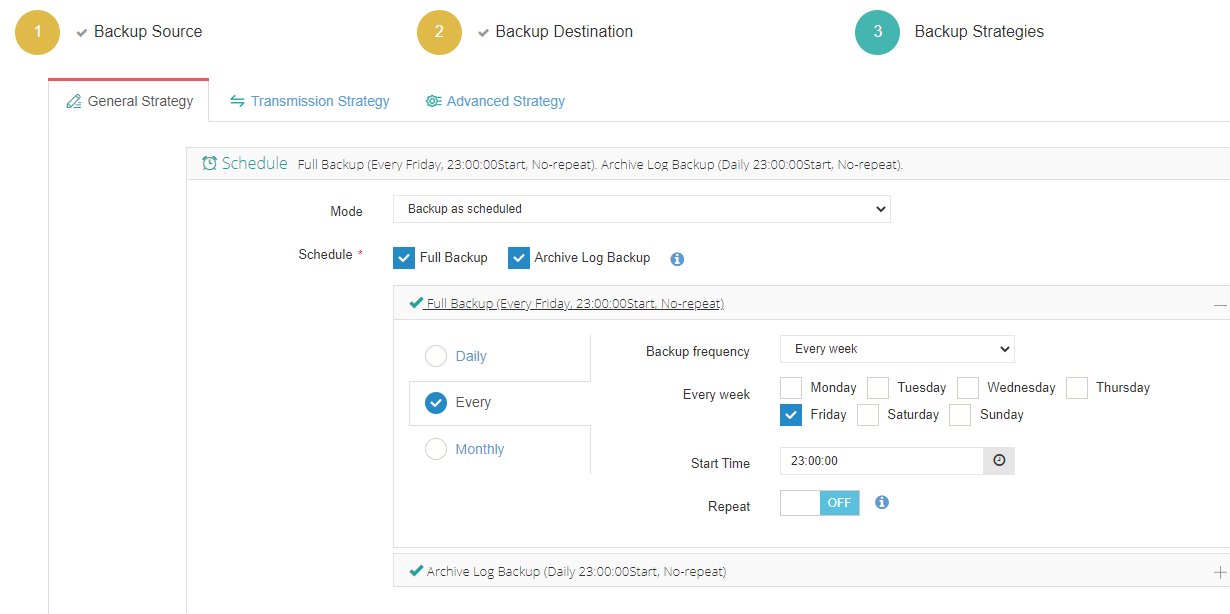
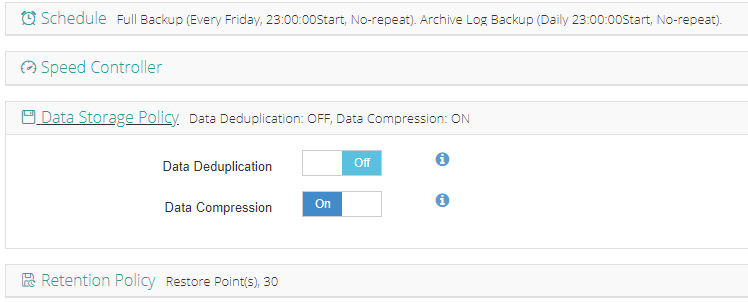
4. View settings and click Submit.
Join thousands of organizations worldwide who trust Vinchin Backup & Recovery’s proven performance—try it risk-free now with a full-featured 60-day free trial! Click below to download instantly and experience top-rated enterprise data protection firsthand.
psql Connect to Database FAQs
Q1: How do I switch users within an active psql session?
A1: Use the command \c <dbname> <username> at any time inside the prompt.
Q2: Can I force encrypted connections even if not required by default?
A2: Yes—add option --set=sslmode=require when invoking psql or include it in connection strings as shown above.
Q3: What’s safest way of automating batch jobs needing DB access?
A3: Store credentials securely inside .pgpass; set strict permissions; avoid passing plain-text passwords through environment variables whenever possible.
Conclusion
Mastering every aspect of “psql connect to database” empowers administrators at all levels—from beginners learning basics through experts securing production workloads—with robust tools tailored precisely for their needs. For comprehensive backup protection of critical databases consider Vinchin’s proven solutions today!
Share on:






