-
What Is Kubernetes Disaster Recovery?
-
Why Disaster Recovery Matters in Kubernetes
-
Method 1: How to Use Velero for Backup and Restore in Kubernetes Disaster Recovery?
-
Method 2: How to Implement Replication Strategies in Kubernetes Disaster Recovery?
-
Method 3: How to Use GitOps Tools for Kubernetes Disaster Recovery?
-
Enterprise-Level Protection with Vinchin Backup & Recovery
-
Kubernetes Disaster Recovery FAQs
-
Conclusion
Kubernetes powers modern applications across industries—but what happens when disaster strikes? Downtime can cost money, customers, or even your reputation. According to industry research, 90% of businesses face unplanned downtime; nearly 40% lose customers as a result. Kubernetes disaster recovery keeps workloads safe so your business stays online.
What Is Kubernetes Disaster Recovery?
Kubernetes disaster recovery means restoring clusters and applications after major failures—like node crashes, data corruption, or region-wide outages. The goal is simple: minimize downtime and data loss so services bounce back fast. This process covers both stateless apps (which don’t store data) and stateful ones (which do), including persistent volume claims (PVCs), configurations, secrets, and cluster state.
Why Disaster Recovery Matters in Kubernetes
Kubernetes is resilient by design but not immune to failure or human error. A single mistake can ripple through your cluster—taking down critical services or exposing sensitive data. Without a plan for kubernetes disaster recovery you risk losing compliance status or customer trust.
Cloud providers offer some protection but follow a shared responsibility model: you must back up application data and configurations yourself—even if using managed Kubernetes like EKS or AKS.
Regular backups plus tested restore procedures are essential for business continuity. Automated failover reduces manual work during emergencies—and gives peace of mind knowing you’re ready for anything.
Method 1: How to Use Velero for Backup and Restore in Kubernetes Disaster Recovery?
Velero is an open-source tool that backs up both resources (like deployments) and persistent volume claims (PVCs). It’s widely used because it supports many cloud storage options such as AWS S3 or Azure Blob Storage.
Before running backups with Velero:
Install Velero in your cluster
Configure credentials for your chosen cloud storage provider using the official documentation
To back up a namespace:
velero backup create my-backup --include-namespaces my-namespace
This command saves all resources—including PVCs—in that namespace to remote storage.
To restore from backup:
velero restore create --from-backup my-backup
Note: The backup must exist in the same Velero instance unless you migrate metadata manually.
You can automate protection with scheduled backups:
velero schedule create daily-backup --schedule "0 2 * * *" --include-namespaces my-namespace
This runs every day at 2 AM server time.
Velero works well for most workloads—but has limits:
Some databases need extra plugins/scripts for application-consistent backups
Restores may require manual steps if custom resources have changed since backup
For advanced scenarios:
Back up entire clusters or migrate workloads between clusters/regions
Always test restores in staging before trusting them in production
Method 2: How to Implement Replication Strategies in Kubernetes Disaster Recovery?
Replication means keeping copies of critical data ready elsewhere—so if one site fails another takes over quickly.
In Kubernetes this often involves active/passive setups:
1. Your primary cluster runs workloads; a secondary cluster stands by idle but ready.
2. Backups are sent continuously to shared cloud storage like S3 buckets—or replicated at the storage layer using tools such as DRBD or built-in SAN/NAS features.
3. For stateful apps needing low-latency failover consider synchronous replication between sites; otherwise asynchronous backup may suffice.
When disaster hits—say the primary goes offline—a management platform such as Rancher or OpenShift detects failure via monitoring tools like Prometheus alerts or custom controllers:
1. Detect outage automatically with alerting rules set on key metrics (e.g., node health)
2. Query latest backup from shared object storage
3. Select target cluster based on available CPU/memory resources; advanced users may experiment with machine learning models (such as LSTM) to predict stability—but this remains experimental
4. Run restore commands (velero restore create ...) on target cluster
Automate these steps using scripts/operators so response time stays low—even overnight!
Remember: cross-cluster networking may require solutions like Submariner if workloads span multiple clouds or regions.
Method 3: How to Use GitOps Tools for Kubernetes Disaster Recovery?
GitOps uses version control systems like Git to manage all cluster configuration—from deployments to network policies—in code form (“manifests”). Tools such as ArgoCD or Flux sync these manifests into live clusters automatically.
Here’s how it works:
1. Store all manifests—including Deployments, Services, ConfigMaps—in a Git repository
2. Set up ArgoCD or Flux inside each target cluster; connect it securely to the repo using sealed secrets/external secret operators when handling sensitive values
3. If disaster strikes build a fresh cluster then install ArgoCD/Flux again; point it at the same repo—the tool applies everything automatically restoring desired state fast
Example ArgoCD Application manifest:
apiVersion: argoproj.io/v1alpha1 kind: Application metadata: name: demo-app spec: project: default source: repoURL: 'https://github.com/example/repo' path: 'k8s-manifests' targetRevision: HEAD destination: server: 'https://kubernetes.default.svc' namespace: demo-app-ns
But remember—GitOps only restores configuration/stateful app definitions—not actual user data! For full kubernetes disaster recovery always combine GitOps with regular PVC backups via tools like Velero—or enterprise solutions such as Vinchin—for persistent volumes/data stores (ComputerWeekly).
GitOps also makes rollbacks easy—you just revert changes in Git—and helps audit who changed what across environments.
Enterprise-Level Protection with Vinchin Backup & Recovery
For organizations seeking streamlined yet robust kubernetes disaster recovery beyond open-source tooling, an enterprise-grade solution becomes essential. Vinchin Backup & Recovery delivers professional protection tailored specifically for containerized environments at scale, offering features such as full/incremental/fine-grained backups by resource type, policy-based automation and scheduling, encrypted transmission and storage, cross-cluster/cross-version restoration capabilities—including heterogeneous multi-cluster support—and intelligent automation options that accelerate throughput while ensuring compliance needs are met efficiently overall benefits include simplified operations, faster recoveries across complex topologies, reduced risk of human error, and seamless integration into hybrid cloud workflows.
The intuitive web console makes safeguarding your Kubernetes environment straightforward—just follow four steps:
Step 1. Select the backup source

Step 2. Choose the backup storage
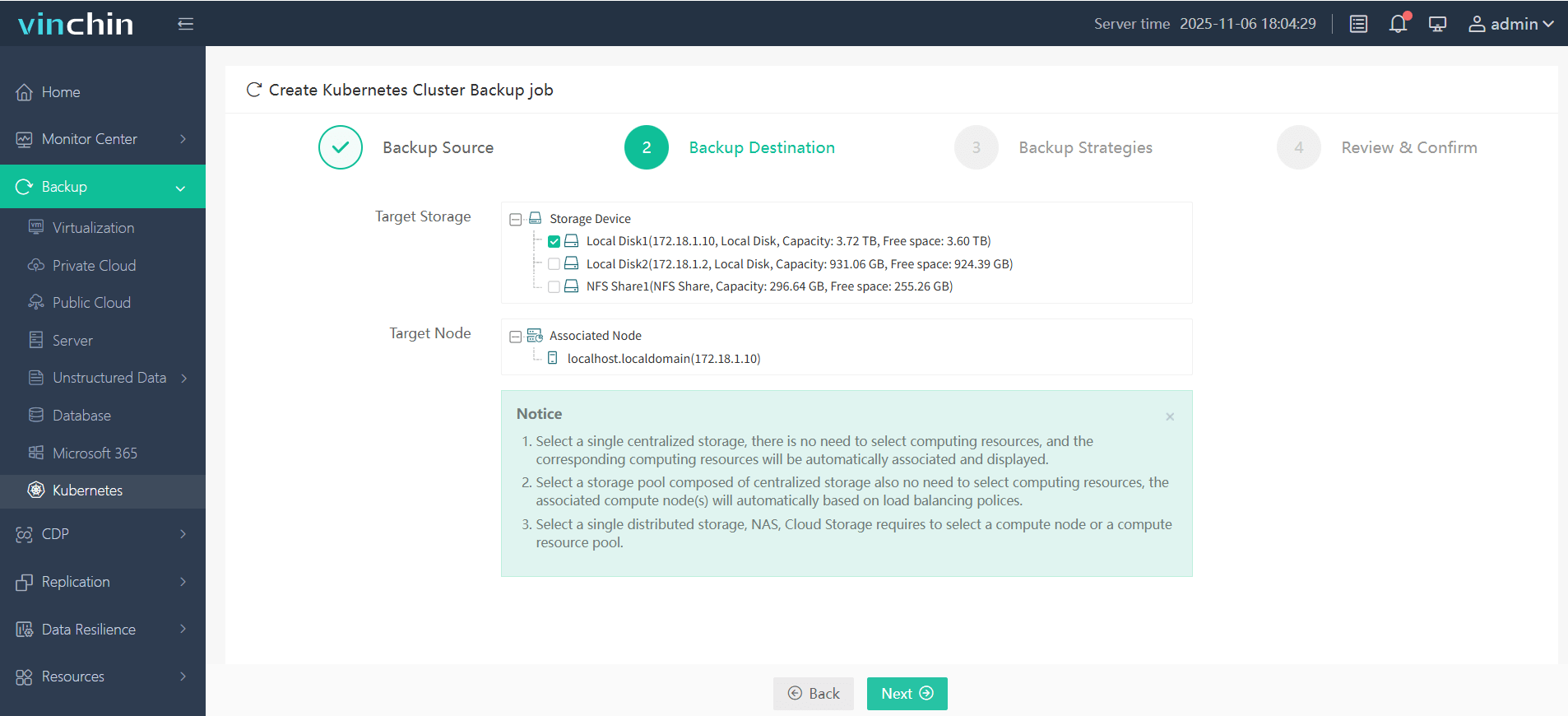
Step 3. Define the backup strategy
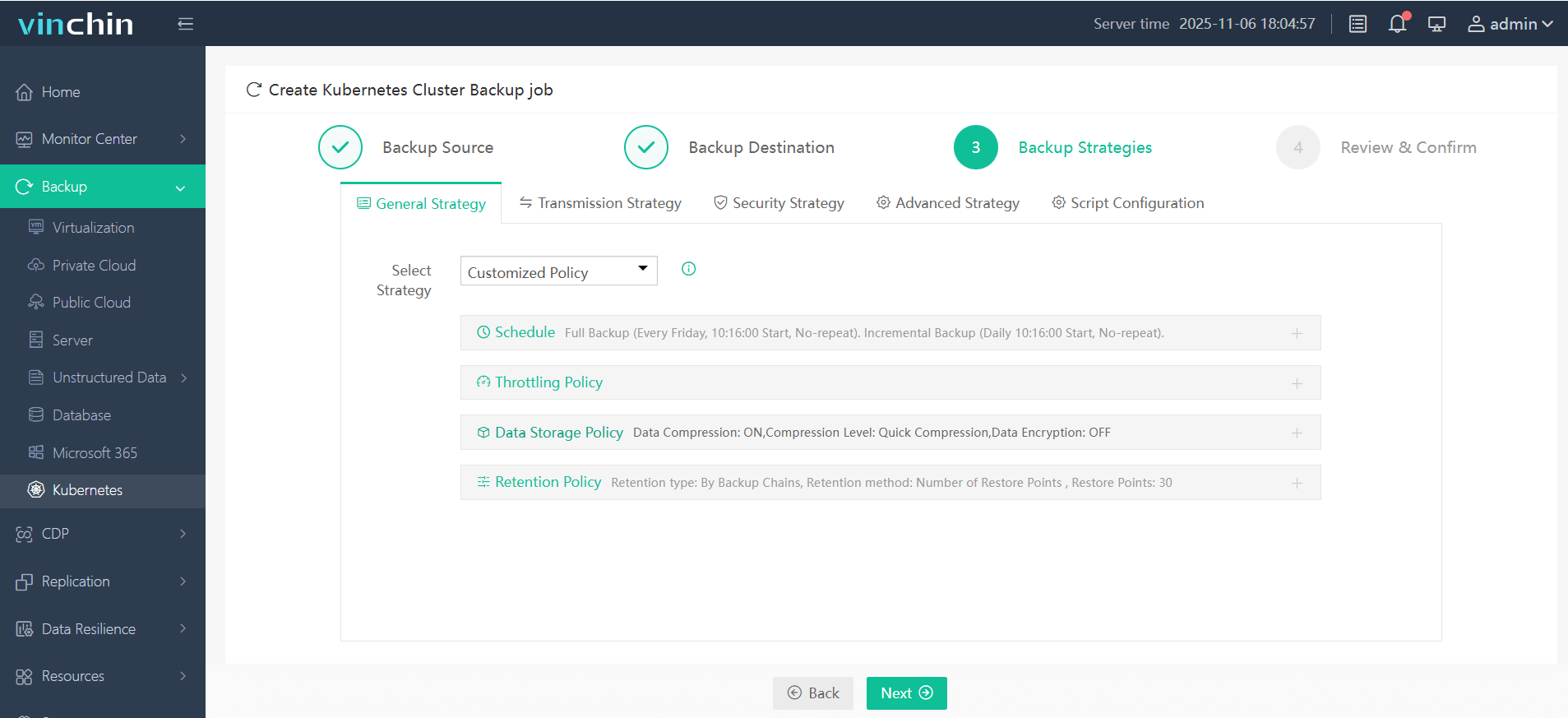
Step 4. Submit the job
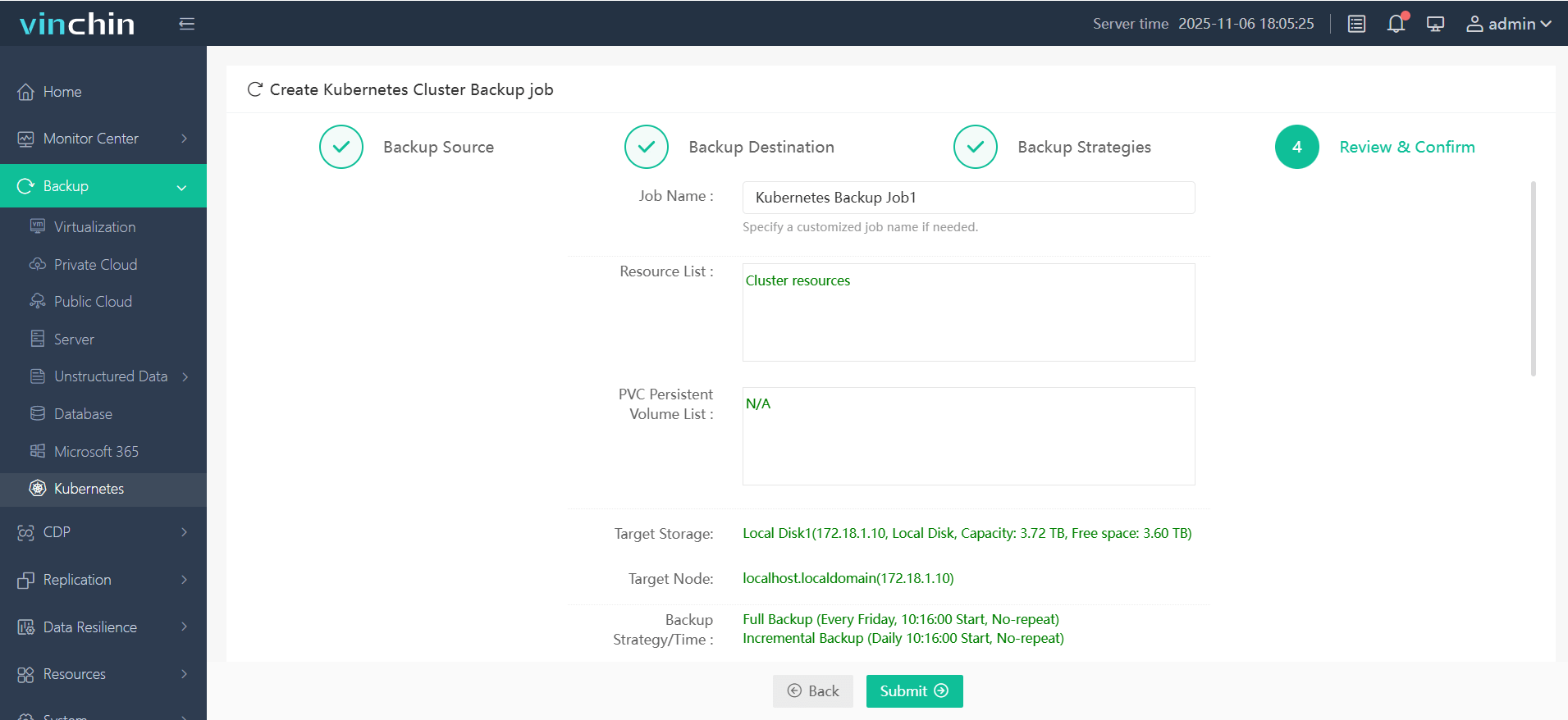
With its global reputation among thousands of enterprises and consistently high ratings from industry analysts, Vinchin Backup & Recovery offers a fully featured free trial valid for sixty days—experience leading-edge protection firsthand by downloading now!
Kubernetes Disaster Recovery FAQs
Q1: How do I simulate multi-region failure without risking production?
A1: Build identical test clusters in separate regions then trigger simulated outages using Chaos Mesh while monitoring failover behavior end-to-end.
Q2: What tools help automate cross-cloud failover between managed K8s platforms?
A2: Combine Cluster API operators with custom scripts plus event-driven triggers from monitoring platforms like Prometheus Alertmanager for seamless migration/restoration flows across clouds/providers/services.
Q3: How often should we update our kubernetes disaster recovery plan?
A3: Review/update plans after any major infrastructure/app change—or at least every six months—to ensure accuracy against current risks/workloads/tools.
Conclusion
Kubernetes disaster recovery protects business continuity even when things go wrong—from hardware failures to cyberattacks or operator mistakes! With proven methods plus regular testing you stay prepared—and Vinchin makes robust protection simple no matter how complex your environment grows.
Share on:







