-
What Is Oracle Database Firewall?
-
Why Use an Oracle Database Firewall?
-
Main Features of Oracle Database Firewall
-
How to Set Up Oracle Database Firewall
-
Introducing Vinchin Backup & Recovery for Enterprise-Level Protection
-
Oracle Database Firewall FAQs
-
Conclusion
Databases are at the core of every modern business. They hold sensitive information that powers everything from online stores to patient records. But as cyber threats grow—ransomware attacks, insider misuse, or simple human error—the risk to your data rises too. How do you keep your Oracle databases safe from these dangers? One answer is an extra layer of protection: the Oracle Database Firewall.
In this guide, we’ll break down what makes Oracle Database Firewall unique, why it’s essential today, its main features, how to deploy it step by step—including practical scenarios—and how Vinchin can further secure your Oracle workloads.
What Is Oracle Database Firewall?
Oracle Database Firewall is a network-based security solution built specifically for database environments. It stands between users or applications and your database server itself—watching every SQL statement that tries to get through.
Unlike traditional firewalls that only look at network packets or rely on pattern matching (which can miss sophisticated attacks), Oracle Database Firewall understands SQL grammar and context within the database session itself. This means it can spot dangerous queries—even if they’re disguised—and block them before they ever reach your data.
The firewall inspects each SQL command against policies you set up: allowing safe statements while blocking or alerting on anything suspicious or unauthorized.
Why Use an Oracle Database Firewall?
Why do organizations invest in this technology? Because databases face constant threats—from outside hackers using SQL injection techniques to insiders misusing their privileges or even accidental mistakes by trusted staff.
Oracle Database Firewall helps reduce these risks by:
Blocking unauthorized SQL statements before they touch your data
Monitoring all access attempts—including those by privileged users or automated apps
Alerting administrators when something looks out of place
Helping meet compliance standards like PCI DSS, HIPAA, or SOX
By acting as a gatekeeper at the SQL level—not just at the network—it lets you “trust but verify” every interaction with your critical databases.
Main Features of Oracle Database Firewall
At its heart is a grammar-based analysis engine that reviews SQL traffic in real time. Here’s what sets it apart:
White List and Black List Policies: You decide which types of SQL are allowed (white list) or blocked (black list). Exception lists let you fine-tune access when needed.
Multiple Deployment Modes: Choose between blocking (proxy), monitoring (out-of-band), or host-based modes depending on your architecture.
Real-Time Alerts & Reporting: Get instant notifications about policy violations; generate detailed reports for audits.
Session Context Analysis: Enforce rules based on user identity, IP address, application name, or even time of day—giving you granular control over who does what and when.
High Availability Support: Set up resilient pairs so protection continues even if one device fails.
Integration Capabilities: Connect with SIEM systems and other security tools for centralized oversight.
These features work together to provide both preventive controls (blocking bad actions) and detective controls (alerting you when something unusual happens).
How to Set Up Oracle Database Firewall
Deploying Oracle Database Firewall involves several steps—from initial planning through advanced configuration—to ensure robust protection without disrupting normal operations.
1. Plan Your Deployment
Start by deciding which deployment mode fits best:
Monitoring/Blocking (Proxy Mode) places the firewall directly between clients/applications and your database server so it can inspect—and optionally block—all traffic passing through.
Monitoring (Out-of-Band Mode) uses a network tap or SPAN port so the firewall sees copies of traffic but doesn’t sit inline; this is useful if you want visibility without affecting performance.
Monitoring (Host Monitor Mode) runs an agent directly on each database server that forwards activity logs back to the firewall appliance for review.
Choose proxy mode if you need active blocking; choose out-of-band or host monitor modes if passive monitoring suffices—or combine them across different environments as needed.
2. Install and Configure the Appliance
Install Oracle Database Firewall as a hardened software appliance either on dedicated hardware or supported virtual infrastructure:
Assign at least one network interface card (NIC) for management tasks such as updates/configuration changes via web console access; two additional NICs may be required in proxy deployments—for client-side connections versus backend database links—to keep traffic separated securely.
Set static IP addresses during installation along with subnet masks/gateways appropriate for each interface; configure NTP servers so system clocks stay synchronized—a must-have for accurate logging/reporting later on!
3. Register With Audit Vault Server
Policy management requires integration with an Audit Vault Server—which acts as central command/control hub:
Log into your newly installed firewall appliance via SSH using root credentials
Run:
/opt/avdf/config-utils/bin/config-avs set avs=primary address=<IP address> certificate=<Path>
to register primary Audit Vault Server
For high availability setups:
/opt/avdf/config-utils/bin/config-avs set avs=secondary address=<Standby IP> certificate=<Path>
Check registration status anytime:
/opt/avdf/config-utils/bin/config-avs show
This connection enables remote policy updates plus consolidated alert/report delivery across multiple firewalls/databases under management—a key advantage over standalone solutions!
4. Configure Network Settings & Access Controls
Fine-tune networking using either web console dialogs (Network Settings) inside Audit Vault Server UI—or CLI commands where needed:
Assign correct IP/subnet/gateway values per interface
Add DNS servers if external name resolution is required
Control SSH/SNMP access tightly:
To allow SSH only from specific admin workstations:
/opt/avdf/config-utils/bin/config-ssh set access=192.0.2.x
To permit SSH universally:
/opt/avdf/config-utils/bin/config-ssh set access=all
To disable SSH entirely:
/opt/avdf/config-utils/bin/config-ssh set access=disabled
Always restrict remote admin protocols wherever possible!
5. Define Traffic Sources & Monitoring Points
Within Audit Vault Server console:
Navigate to Database Firewalls, select your deployed device
Add new entries under Monitoring Points specifying which production/test databases require coverage
For proxy deployments specify listening IP address + port combination used by clients/apps going forward—they must connect through this endpoint now!
For out-of-band setups configure which NIC receives mirrored packets via switch tap/SPAN configuration upstream
Test connectivity thoroughly after making changes—ideally start in non-production environments first!
6. Set Up Security Policies
Policies determine exactly what gets allowed versus blocked/warned about:
From within console's Policies area create white list entries covering all known-safe application queries/routines
Add black list rules targeting common attack signatures/patterns seen historically
Define exception lists where temporary overrides are justified—for example during planned maintenance windows
Leverage session context filters so only certain users/IP ranges/applications/times have elevated rights
Review/update policies regularly based on audit findings/new threat intelligence!
7. Enable Alerts & Reporting Functions
Configure alert thresholds so admins receive immediate notification whenever violations occur—via email/SMS/syslog feeds integrated into broader SIEM platforms if desired
Schedule recurring compliance reports tailored around regulatory requirements relevant in your industry
Centralized reporting not only aids audits but also helps spot trends before they become incidents!
Introducing Vinchin Backup & Recovery for Enterprise-Level Protection
Beyond perimeter defenses like firewalls, robust backup strategies remain crucial for safeguarding critical data against ransomware and operational mishaps alike. Vinchin Backup & Recovery stands out as a professional enterprise-level solution supporting today’s mainstream databases—including full compatibility with Oracle alongside MySQL, SQL Server, MariaDB, PostgreSQL/PostgresPro, and MongoDB environments. For organizations running mission-critical workloads such as those found in large-scale Oracle deployments, Vinchin Backup & Recovery offers powerful features including incremental backup capabilities tailored specifically for Oracle databases; batch backup operations across multiple instances; multi-level data compression options; comprehensive retention policy management including GFS retention schemes; and seamless cloud backup/tape archiving integration—all designed to maximize efficiency while minimizing risk exposure across hybrid infrastructures.
The intuitive web console streamlines complex tasks into four straightforward steps:
Step 1 — Select the Oracle database to back up;
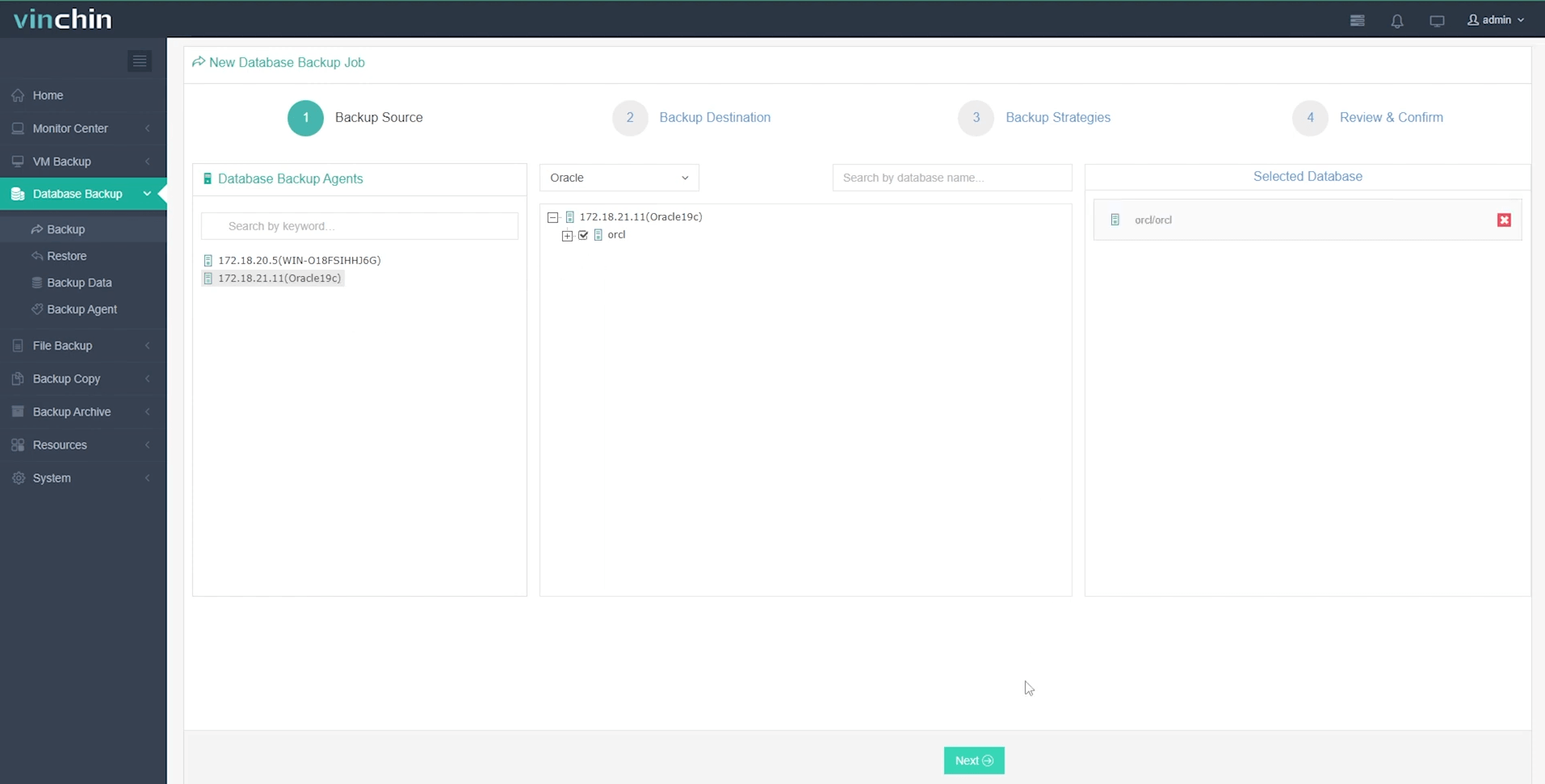
Step 2 — Choose backup storage location;
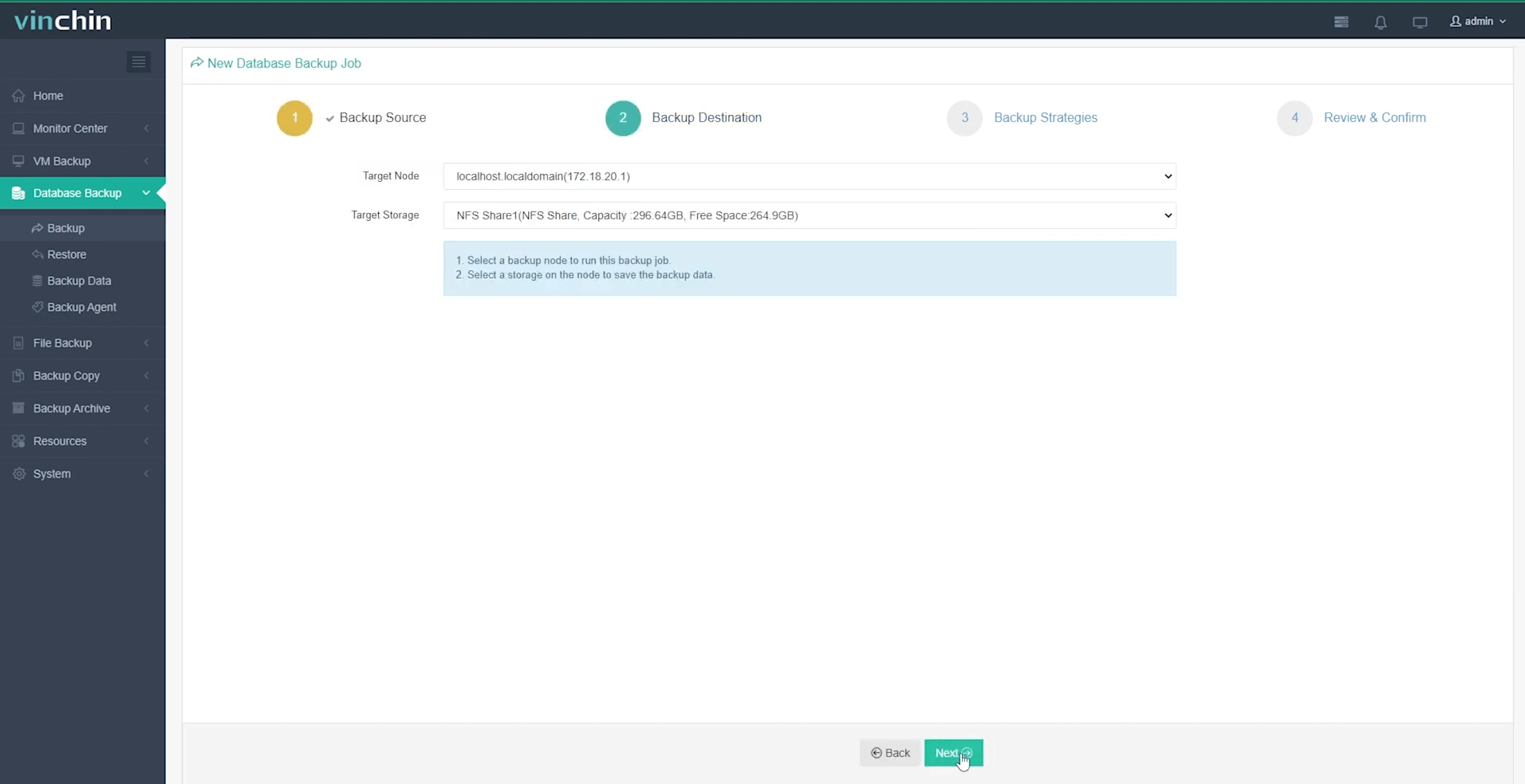
Step 3 — Define backup strategy parameters such as scheduling and retention policies;
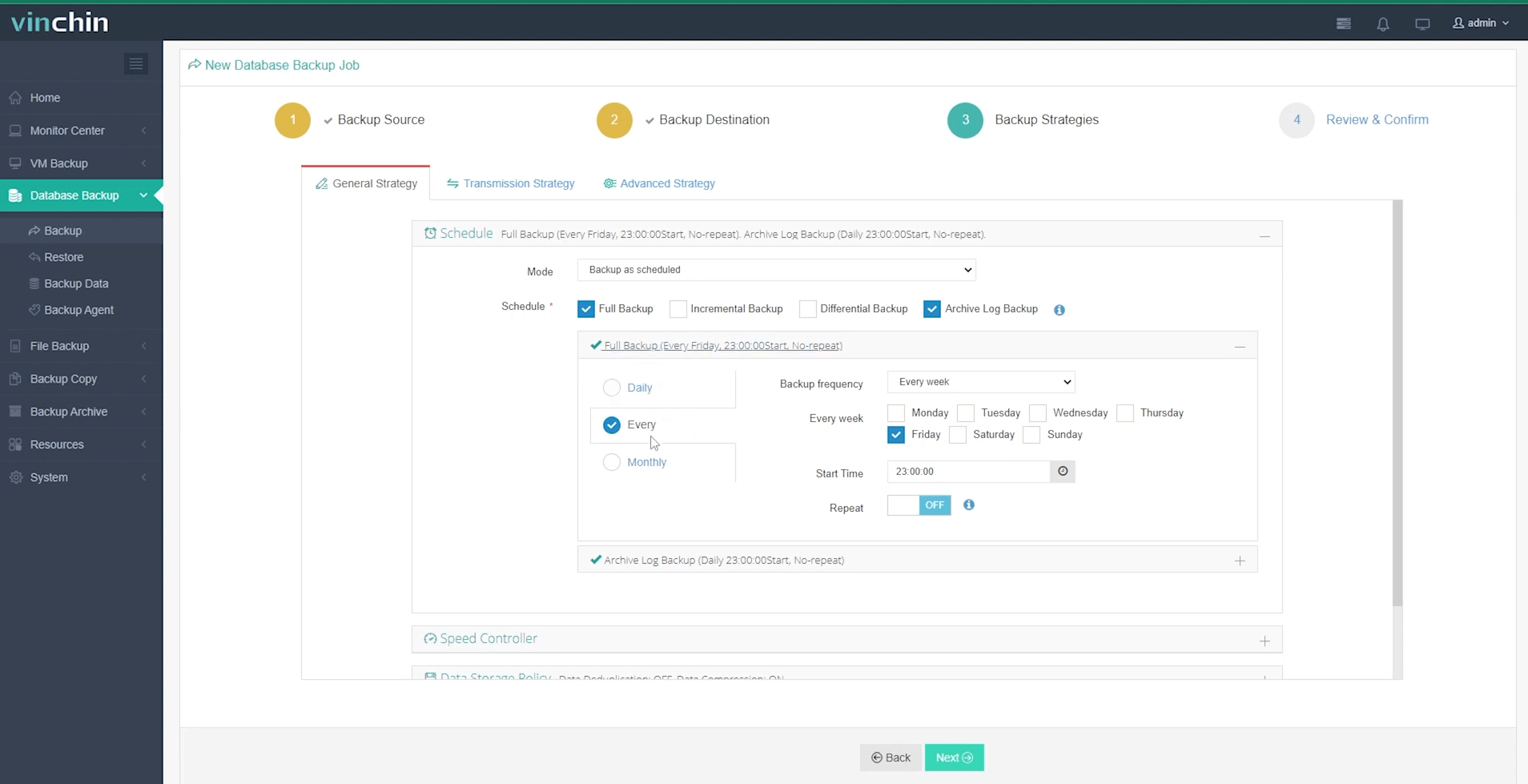
Step 4 — Submit the job with just a click.
Trusted globally by thousands of enterprises—with top ratings from industry analysts—Vinchin Backup & Recovery delivers proven reliability backed by responsive support teams worldwide. Experience all features free for 60 days—click below to download now!
Oracle Database Firewall FAQs
Q1: Can I deploy Oracle Database Firewall alongside clustered RAC instances?
Yes—you can protect clustered configurations but must define separate monitoring points per node/IP participating within cluster topology
Q2: Does enabling deep packet inspection slow down my busiest OLTP workloads?
Some latency increase is typical especially under heavy loads—but proper sizing/testing keeps impact minimal (<5% overhead reported in most cases)
Q3: How does the firewall handle encrypted client connections?
It supports SSL/TLS interception provided certificates are imported correctly during setup—allowing full inspection while maintaining end-to-end encryption integrity
Conclusion
Oracle Database Firewall gives you powerful tools to monitor and control every interaction with your critical data assets—blocking threats long before they cause harm while supporting compliance efforts too For total protection pair it with Vinchin backup solutions ensuring fast recovery no matter what happens next
Share on:








