-
What Are SQL Server Database Roles?
-
Types of SQL Server Database Roles
-
Method 1. Assigning Database Roles in SSMS
-
Method 2. Assigning Database Roles Using T-SQL
-
How to Create User-Defined Roles in SSMS?
-
How to Protect SQL Server Database with Vinchin Backup & Recovery
-
SQL Server Database Roles FAQs
-
Conclusion
Managing access in SQL Server is not just about convenience—it’s about security, compliance, and smooth operations. Database roles help you control who can do what inside your databases. This keeps sensitive data safe from unauthorized access while making it easier for teams to work efficiently. Many organizations must also meet strict regulations like GDPR or HIPAA. Using roles helps you meet these requirements by simplifying audits and tracking who has access.
But how do SQL Server database roles actually work? How can you assign them correctly? In this guide, we’ll walk through everything from basic concepts to advanced techniques. By the end, you’ll be ready to manage SQL Server database roles confidently—no matter your environment’s size or complexity.
What Are SQL Server Database Roles?
SQL Server database roles are groups of permissions that you assign within a specific database. Instead of giving each user individual rights—which gets messy fast—you add users or groups to a role. The permissions assigned to that role then apply automatically to every member.
This approach enforces the principle of least privilege. That means users only get the minimum permissions they need for their job—nothing more. It reduces risk if an account is compromised or misused. Roles also make it easy to update permissions across many users at once.
It’s important not to confuse database roles with server-level roles. Database roles control access inside one database; server-level roles manage permissions across the entire SQL Server instance. Keeping these separate helps prevent accidental over-permissioning.
Types of SQL Server Database Roles
Understanding different types of database roles helps you choose wisely for your environment.
Fixed Database Roles come built into every SQL Server database. Their permissions are set by Microsoft and cannot be changed directly. Some common fixed roles include:
db_owner: Has full control over all aspects of the database—use sparingly!
db_datareader: Can read all data in every table or view but cannot change anything.
db_datawriter: Can insert, update, or delete data in any table but cannot alter structure.
db_securityadmin: Manages role membership and permissions but does not own data itself.
db_backupoperator: Can back up the database but cannot restore it without extra rights.
Be careful with powerful fixed roles like db_owner, as they grant broad authority that could lead to mistakes or security breaches if misused.
User-Defined Database Roles let you create custom sets of permissions tailored for your organization’s needs. For example, you might create a “HR_ReadOnly” role that allows HR staffers only to view employee records—not edit them—or a “Finance_Editor” role with broader rights over financial tables.
Customizing user-defined roles makes it easier to match business processes without granting unnecessary power.
Application Roles are special-purpose accounts used by applications rather than people. When an app connects using an application role password, it assumes that role’s permissions until it disconnects—even if individual users have fewer rights normally. This is useful when apps need temporary elevated privileges without exposing those rights permanently.
If you use application roles, always secure connection strings carefully so attackers can’t hijack those credentials.
Each type serves its own purpose—choose based on whether you want broad control (fixed), fine-tuned customization (user-defined), or app-specific behavior (application).
Method 1. Assigning Database Roles in SSMS
Assigning users or groups to database roles using SQL Server Management Studio (SSMS) is straightforward—even if you’re new to administration tools.
First open SQL Server Management Studio, then connect to your target instance using your credentials. In Object Explorer, expand your chosen database node until you see Security, then expand Roles, followed by Database Roles.
Right-click on the desired role name—for example, db_datareader—and select Properties from the context menu.
In the Database Role Properties window that appears, switch over to the Members page using its tab on the left side. Click Add, then select one or more users or Windows groups from your directory list; click OK when finished.
Double-check your selections before confirming changes—accidental assignments happen! Once satisfied, click OK again in the main window; new members now inherit all permissions granted by that role immediately.
Want proof? Double-click any existing role under Database Roles, then review its current members listed under Members—a handy way to audit assignments visually at any time.
If troubleshooting permission issues later on, try right-clicking a user account under Security > Users, choosing Properties, then reviewing effective access via the Securables > Effective Permissions tab—a great way to spot gaps or overlaps quickly (note: some tabs may look slightly different depending on whether you're using SSMS 18 or 19).
Method 2. Assigning Database Roles Using T-SQL
For automation-minded admins—or anyone managing lots of accounts at once—T-SQL scripting offers speed and repeatability beyond point-and-click tools.
To add a single user named “App_User” into the built-in reader group:
ALTER ROLE db_datareader ADD MEMBER App_User;
Need bulk assignments? Loop through multiple names using dynamic T-SQL:
DECLARE @UserList TABLE(UserName NVARCHAR(128));
INSERT INTO @UserList VALUES ('Alice'), ('Bob'), ('Charlie');
DECLARE @UserName NVARCHAR(128);
DECLARE cur CURSOR FOR SELECT UserName FROM @UserList;
OPEN cur;
FETCH NEXT FROM cur INTO @UserName;
WHILE @@FETCH_STATUS = 0
BEGIN
BEGIN TRY
EXEC sp_executesql N'ALTER ROLE db_datareader ADD MEMBER [' + @UserName + ']';
END TRY
BEGIN CATCH
PRINT 'Failed adding ' + @UserName + ': ' + ERROR_MESSAGE();
END CATCH;
FETCH NEXT FROM cur INTO @UserName;
END
CLOSE cur;
DEALLOCATE cur;To remove someone from a role:
ALTER ROLE db_datareader DROP MEMBER App_User;
Want an instant report showing which users belong where? Run this query:
SELECT r.name AS RoleName, m.name AS MemberName FROM sys.database_role_members rm JOIN sys.database_principals r ON rm.role_principal_id = r.principal_id JOIN sys.database_principals m ON rm.member_principal_id = m.principal_id;
How to Create User-Defined Roles in SSMS?
Built-in options don’t always fit complex organizations—that’s where custom user-defined database roles shine.
Start by connecting through SQL Server Management Studio, expanding your chosen database node under Object Explorer, then drilling down into Security > Roles > Database Roles as before.
Right-click on Database Roles, select New Database Role
In the dialog box that appears:
1. Enter a clear name in the Role name: field—for example “udr_HR_ReadOnly” (prefixes like “udr_” help distinguish custom creations).
2. Under Owner: pick which existing login will own this new role; default choices usually suffice unless special delegation is needed.
3. Click Add beneath Members if you want initial users included now; otherwise leave blank for later assignment via T-SQL or UI steps above.
4. Switch over to the Securables page; click Add, pick objects such as tables/views/procedures needing protection; check boxes beside desired actions (“Select”, “Insert”, etc.).
5. Click OK when finished—the new role now exists!
How to Protect SQL Server Database with Vinchin Backup & Recovery
Beyond strong permission management, reliable backups are essential for safeguarding critical data in any SQL Server environment against loss and disasters alike. Vinchin Backup & Recovery stands out as an enterprise-grade solution supporting most mainstream databases—including robust support for Microsoft SQL Server alongside Oracle, MySQL, MariaDB, PostgreSQL/PostgresPro, and MongoDB environments worldwide.
Vinchin Backup & Recovery delivers features such as incremental backup tailored for SQL Server workloads, batch backup management across multiple databases simultaneously, flexible data retention policies including GFS retention policies, ransomware protectionmechanisms built-in throughout backup cycles, and seamless cloud/tape archiving integration—all designed for comprehensive business continuity and regulatory compliance.
The web console is simple yet powerful:
1. Select source SQL Server database(s),
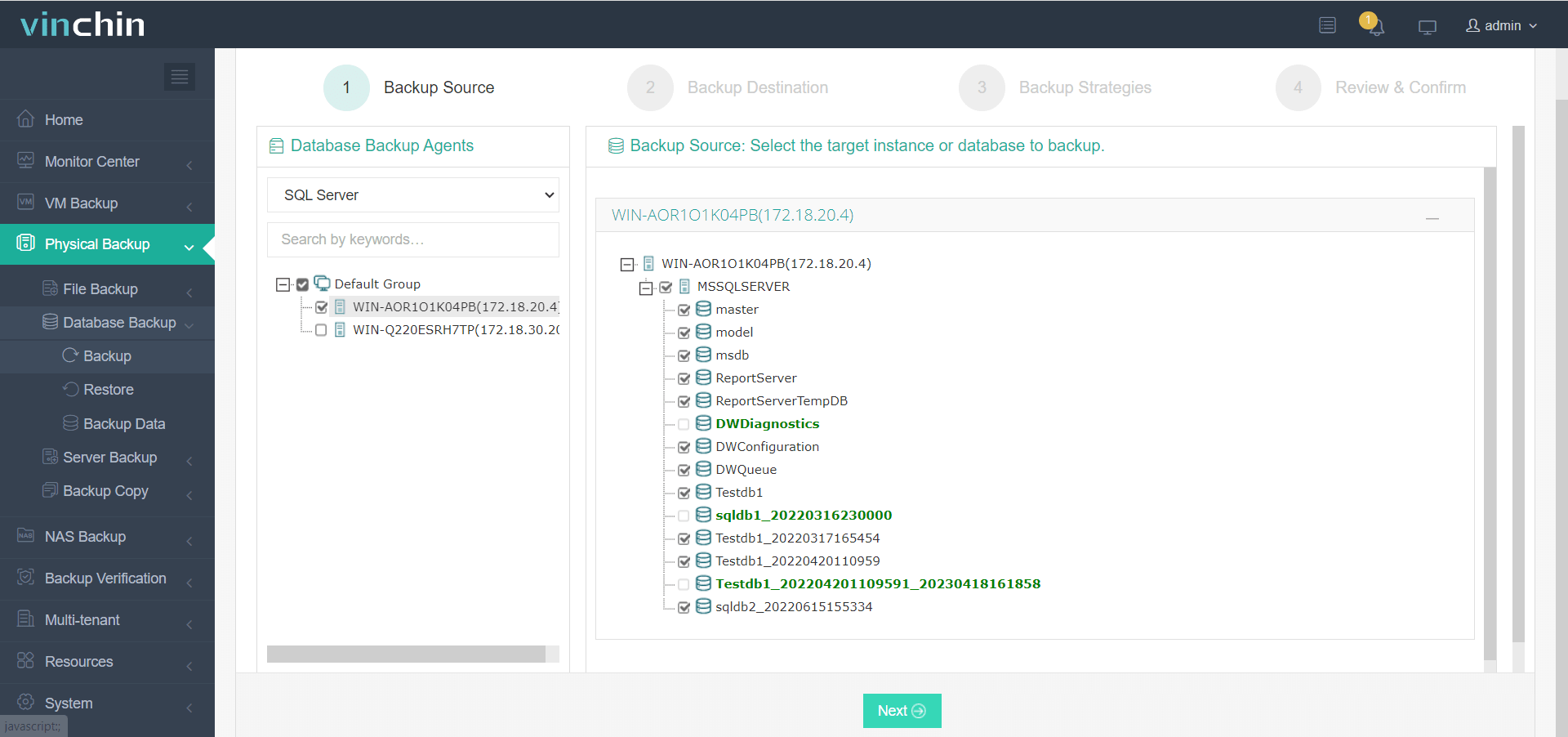
2. Choose target storage location(s),
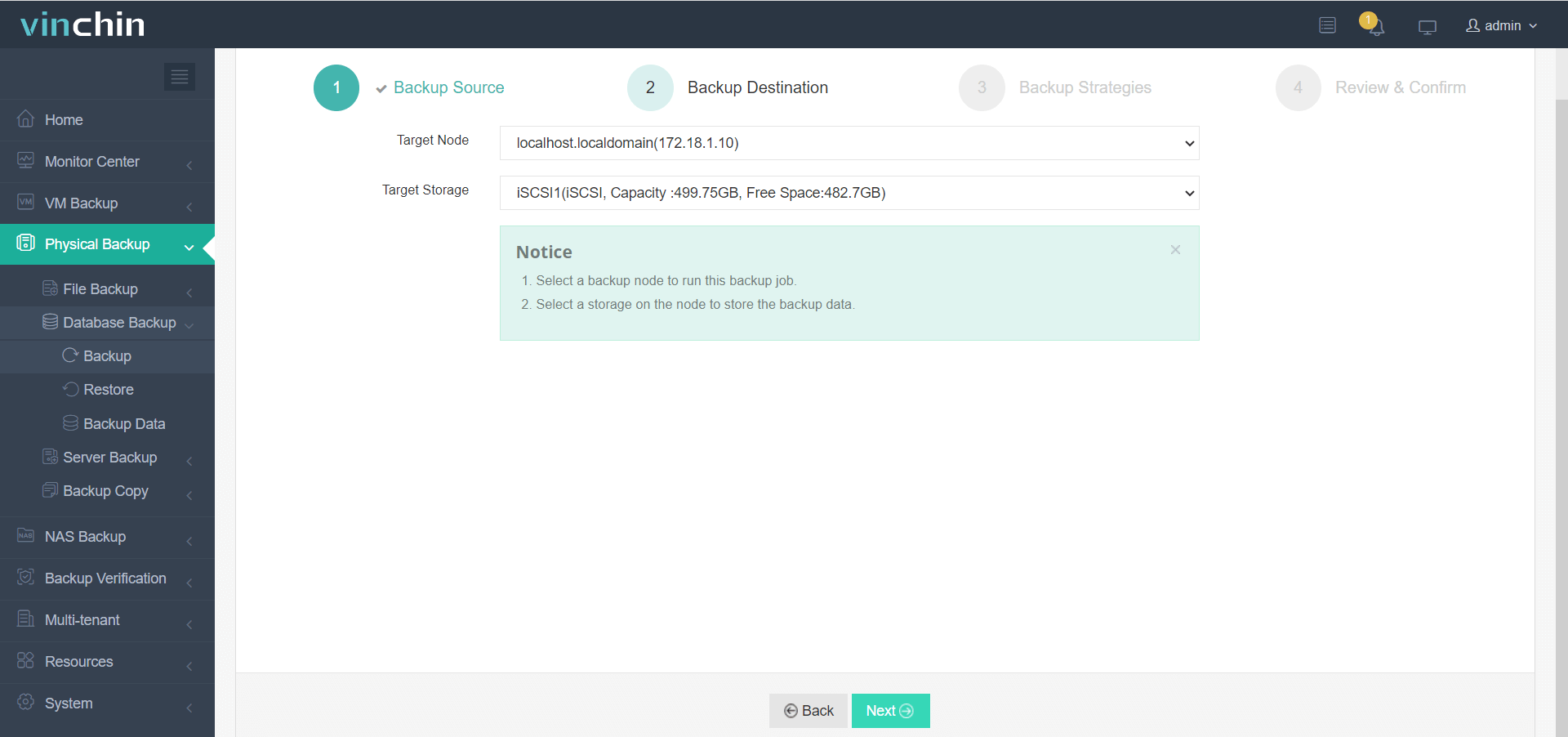
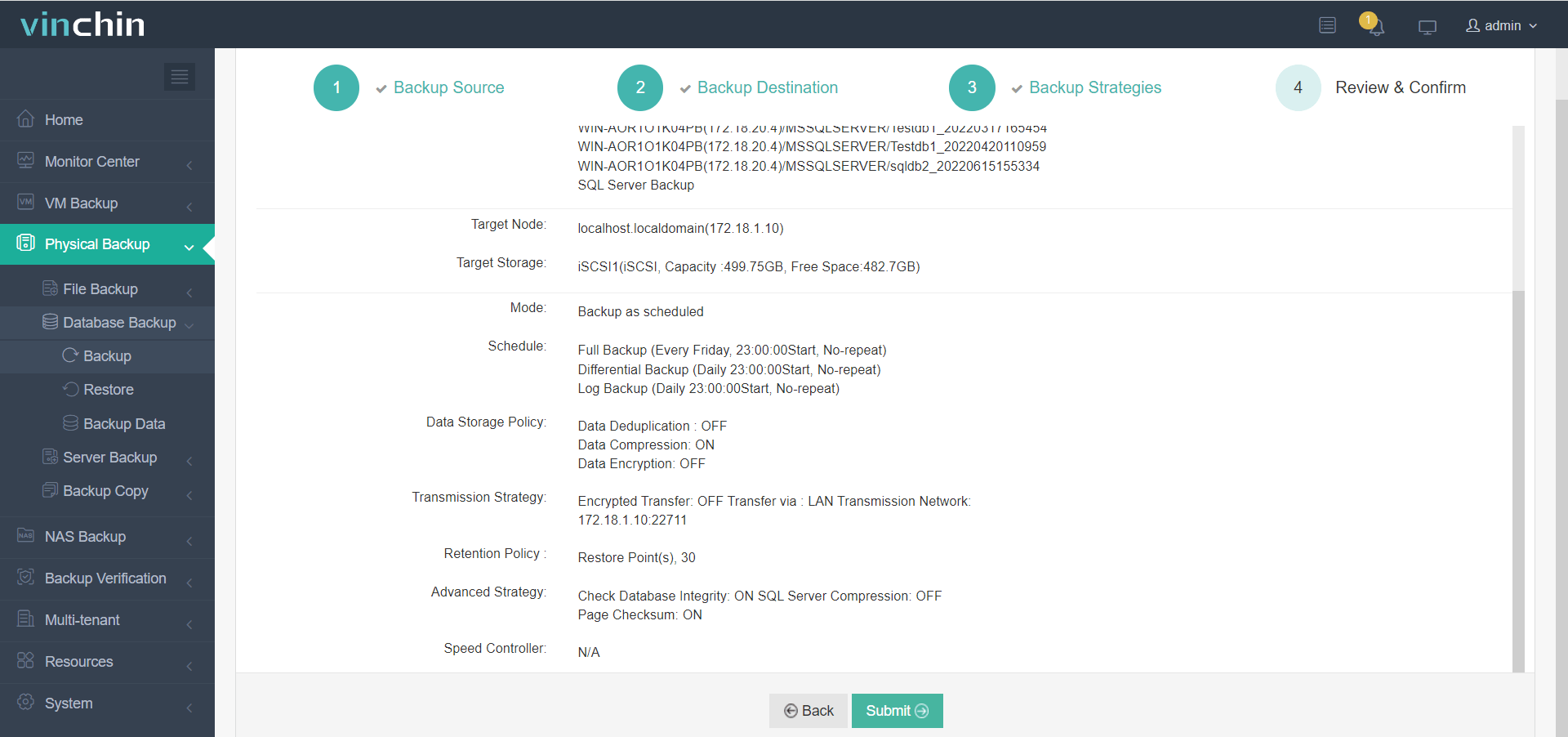
3. Configure backup strategies,

4. Submit the job.
Join thousands globally who trust Vinchin Backup & Recovery's proven reliability and top-rated support! Try all features free for 60 days—click below and start protecting your critical databases today.
SQL Server Database Roles FAQs
Q1: How do I audit which users have excessive privileges?
A1: Query sys.database_role_members joined with sys.database_principals, then compare results against documented policies; flag any unexpected memberships for review.
Q2: What should I do if my application fails due to missing permissions after assigning an application role?
A2: Check that required object-level grants exist for that application role using SSMS Securables tab; adjust as needed before retrying connection attempts.
Q3: How can I synchronize user-role assignments across Always On availability group replicas?
A3: Script out all login/user/role mappings from primary replica using T-SQL; run same scripts manually on secondary replicas since assignments are not replicated automatically.
Conclusion
SQL Server database roles form a solid foundation for secure access management at every level—from daily tasks up through regulatory audits and disaster recovery planning alike. Use SSMS or T-SQL confidently knowing best practices keep risks low—and remember Vinchin delivers backup peace-of-mind alongside robust security controls!
Share on:






