-
What Is Kubernetes Backup and Restore?
-
Why Backup and Restore Matter in Kubernetes
-
Method 1. Manual Kubernetes Backup and Restore
-
Method 2. How to Perform Kubernetes Backup and Restore Using Velero?
-
Vinchin Backup & Recovery: Enterprise-Level Kubernetes Protection Made Simple
-
Kubernetes Backup And Restore FAQs
-
Conclusion
Imagine your business runs on Kubernetes—and then disaster strikes. What would you do if your cluster vanished overnight? Without a solid kubernetes backup and restore plan, even the most robust infrastructure can crumble fast. In this guide, we walk through everything you need to know about protecting your Kubernetes workloads—from manual basics to advanced enterprise solutions.
What Is Kubernetes Backup and Restore?
Kubernetes backup and restore means saving all critical data that makes up your cluster—then being able to bring it back when things go wrong. This includes application data stored in persistent volumes as well as the entire configuration of your cluster: deployments, services, secrets, custom resources—everything that keeps your apps running smoothly.
A good strategy covers both stateless resources (like Deployments or Services) and stateful data (like PersistentVolumeClaims). Backups should capture both types so you can recover quickly from any failure.
Why Backup and Restore Matter in Kubernetes
Kubernetes is powerful because it’s dynamic—resources scale up or down automatically across distributed nodes. But this flexibility comes with risk: accidental deletions, hardware failures, ransomware attacks—all can cause downtime or data loss if you’re not prepared. Backups are your insurance policy against these threats.
If an admin accidentally deletes a namespace or a node fails unexpectedly during an upgrade—how fast could you recover? Regular kubernetes backup and restore procedures help ensure business continuity no matter what happens behind the scenes.
Method 1. Manual Kubernetes Backup and Restore
Manual methods are often where teams start their journey with kubernetes backup and restore—but they require discipline and regular testing to work reliably at scale.
Manual Backup Prerequisites
Before starting manual backups:
Make sure you have direct access to a control plane node.
Confirm etcd is running locally or accessible via network.
Gather necessary certificates (
ca.crt,server.crt,server.key) for secure etcd access.Check storage provider documentation if backing up persistent volumes manually.
Remember: You need sufficient permissions (
cluster-admin) for all commands below.
Backing Up etcd (Cluster State)
etcd holds all core Kubernetes configurations—including secrets! To create a safe snapshot:
export ETCDCTL_API=3 etcdctl --endpoints=https://127.0.0.1:2379 \ --cacert=/etc/kubernetes/pki/etcd/ca.crt \ --cert=/etc/kubernetes/pki/etcd/server.crt \ --key=/etc/kubernetes/pki/etcd/server.key \ snapshot save /backup/snapshot.db
Store snapshots offsite for safety—and consider automating this process with cron jobs for regular protection!
Restoring etcd
To restore:
1. Stop all API servers on control plane nodes.
2. Run:
export ETCDCTL_API=3 etcdctl snapshot restore /backup/snapshot.db \ --name <etcd-member-name> \ --data-dir /var/lib/etcd-restored
3. Update etcd manifest files if needed to point at the restored data directory.
4. Restart etcd service followed by API servers.
5. Validate recovery by running kubectl get nodes—do all expected nodes appear?
Restoring etcd replaces all current cluster state with what was captured in the snapshot—including RBAC rules!
Backing Up Application Resources
Not everything lives in etcd alone! Use kubectl to export resource definitions:
kubectl get all --all-namespaces -o yaml > all-resources.yaml
But here’s a catch: kubectl get all does not include CustomResourceDefinitions (CRDs), StorageClasses, or some other objects vital for certain workloads! Export those separately:
kubectl get crds -o yaml > crds.yaml kubectl get storageclass -o yaml > storageclasses.yaml
For persistent volumes:
Use cloud provider snapshots if available (check CSI driver compatibility).
Or manually copy disk contents using tools like
rsync.
Restoring Application Resources
To bring resources back:
1. Apply CRDs first:
kubectl apply -f crds.yaml
2. Apply StorageClasses next:
kubectl apply -f storageclasses.yaml
3. Then apply main resource YAMLs:
kubectl apply -f all-resources.yaml
Restore persistent volume data using provider tools or manual file copies before re-attaching pods that depend on them.
Method 2. How to Perform Kubernetes Backup and Restore Using Velero?
When clusters grow—or uptime becomes mission-critical—it’s time for automation! Velero is an open-source tool designed specifically for kubernetes backup and restore tasks across cloud providers or on-premises environments.
Velero supports scheduled backups, granular selection of namespaces/resources/PVCs, retention policies—and even migration between clusters!
Velero Prerequisites & Setup Tips
Before installing Velero:
Ensure you have
cluster-adminprivileges on your target cluster.Prepare object storage credentials (AWS S3 bucket access key/secret key or compatible endpoint).
Install required CSI drivers if planning volume snapshots.
Install CLI locally—for macOS:
brew install velero
For Linux:
curl -L https://github.com/vmware-tanzu/velero/releases/download/v1.x.x/velero-v1.x.x-linux-amd64.tar.gz | tar xz && sudo mv velero-v*/velero /usr/local/bin/
Set up credentials file per provider instructions.
Install Velero into your cluster:
velero install \ --provider aws \ --plugins velero/velero-plugin-for-aws:v1.x.x \ --bucket <your-bucket> \ --backup-location-config region=<region> \ --snapshot-location-config region=<region> \ --secret-file ./velero-creds
Check installation status with:
kubectl get pods -n velero
Creating Backups With Velero
Want an immediate full-cluster backup?
velero backup create my-backup-all
Need just one namespace?
velero backup create my-backup-ns --include-namespaces mynamespace
Or only specific resources?
velero backup create my-backup-apps --include-resources deployments,pods
You can exclude items too using --exclude-namespaces or --exclude-resources.
Schedule daily automatic backups like this:
velero schedule create daily-sched --schedule="@every 24h"
Monitor progress anytime:
velero backup describe my-backup-all
Restoring From Velero Backups
To recover everything from a named backup:
velero restore create --from-backup my-backup-all
Restore just one namespace?
velero restore create --from-backup my-backup-ns --include-namespaces mynamespace ``}
Or only certain resources?
velero restore create --from-backup my-backup-apps --include-resources deployments,pods ``}
Always check logs after restores (kubectl logs deployment/velero -n velero)—and verify restored objects appear as expected using standard kubectl queries!
Vinchin Backup & Recovery: Enterprise-Level Kubernetes Protection Made Simple
For organizations seeking robust protection beyond open-source tooling, Vinchin Backup & Recovery delivers comprehensive enterprise-level capabilities tailored specifically for kubernetes backup and restore scenarios. As a professional solution designed for demanding environments, Vinchin Backup & Recovery offers features such as full/incremental backups, granular recovery options by namespace/application/PVC/resource, cross-cluster/cross-version restoration—including seamless migration between different Kubernetes versions—and advanced security measures like encrypted transmission and WORM protection. These capabilities ensure reliable business continuity while simplifying compliance management across complex infrastructures.
The intuitive web console streamlines operations into four straightforward steps tailored to Kubernetes workflows:
1. Select the backup source

2. Choose the backup storage location
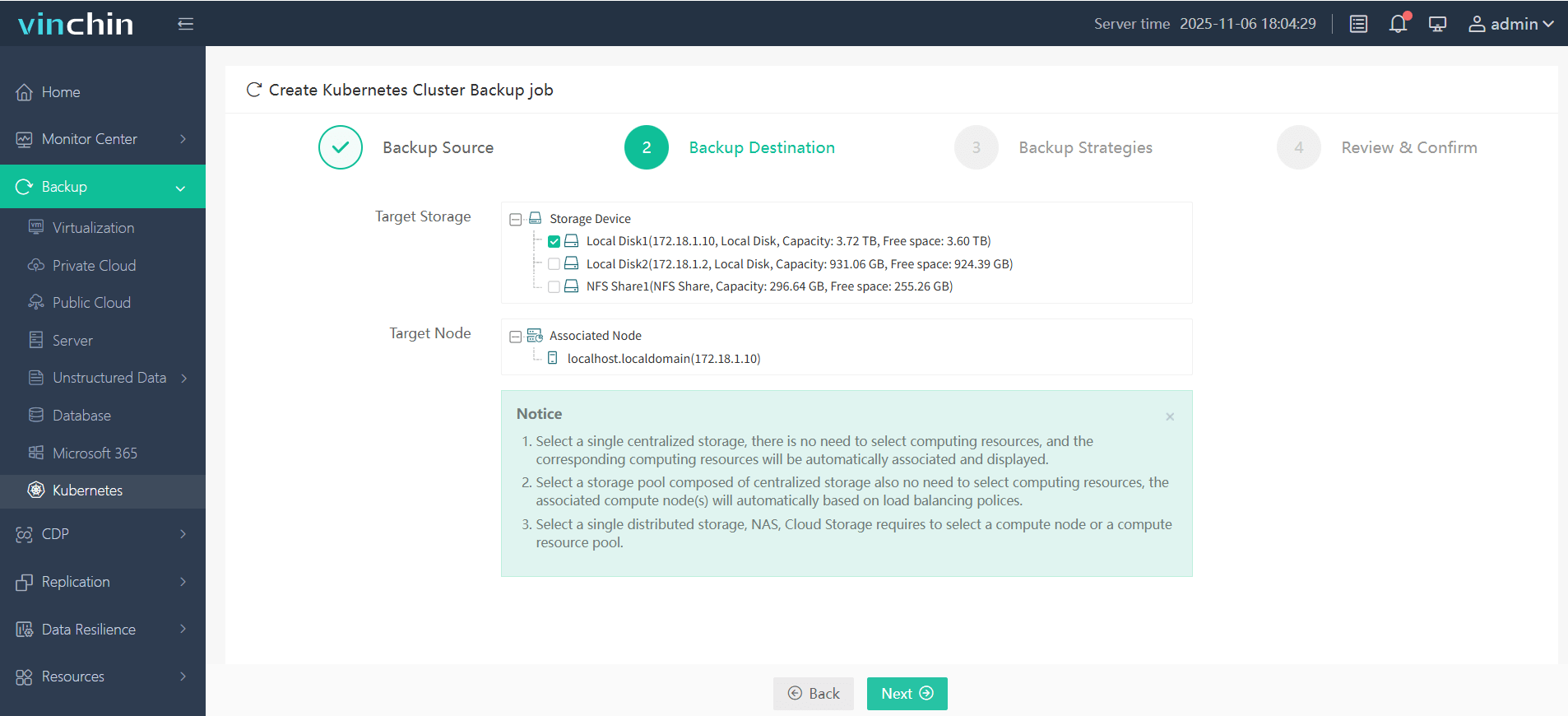
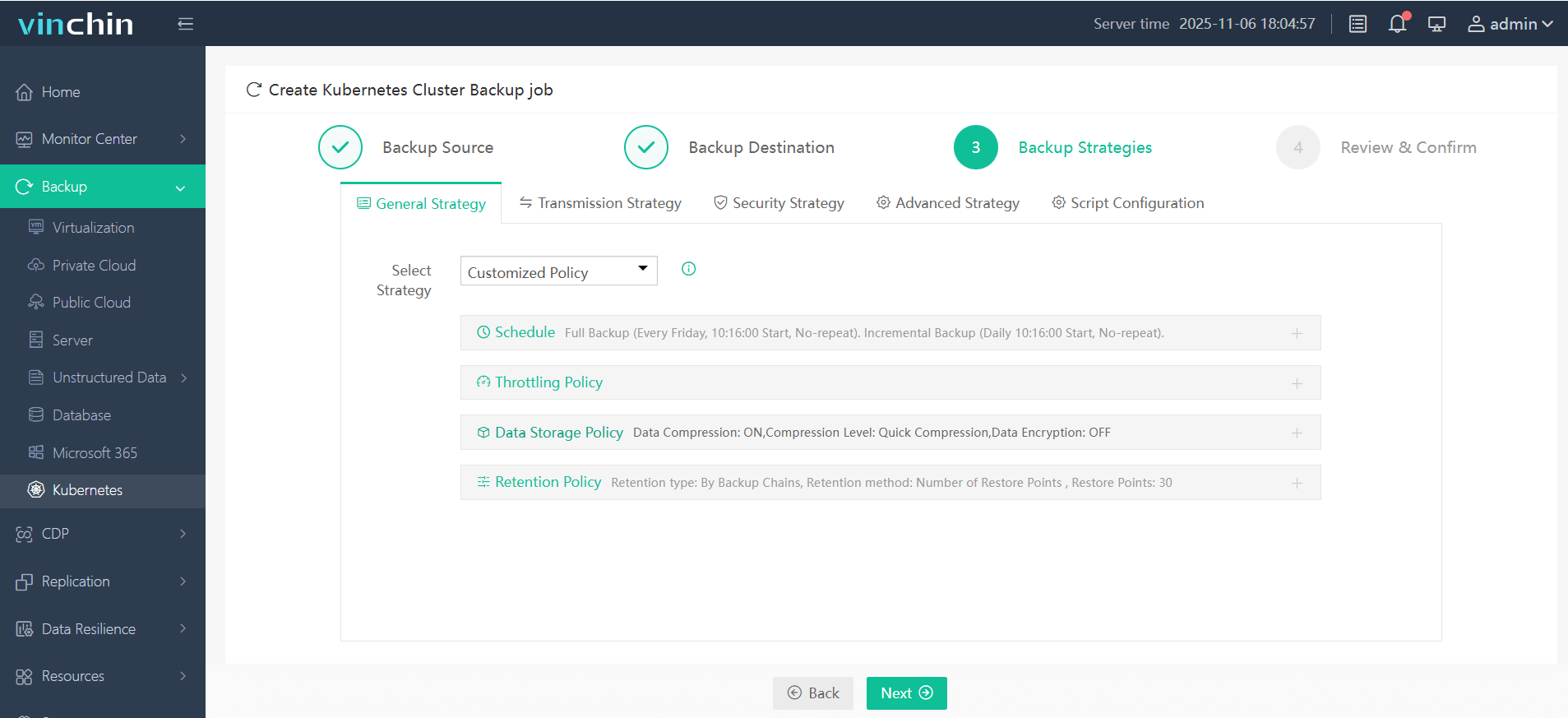
3. Define the backup strategy
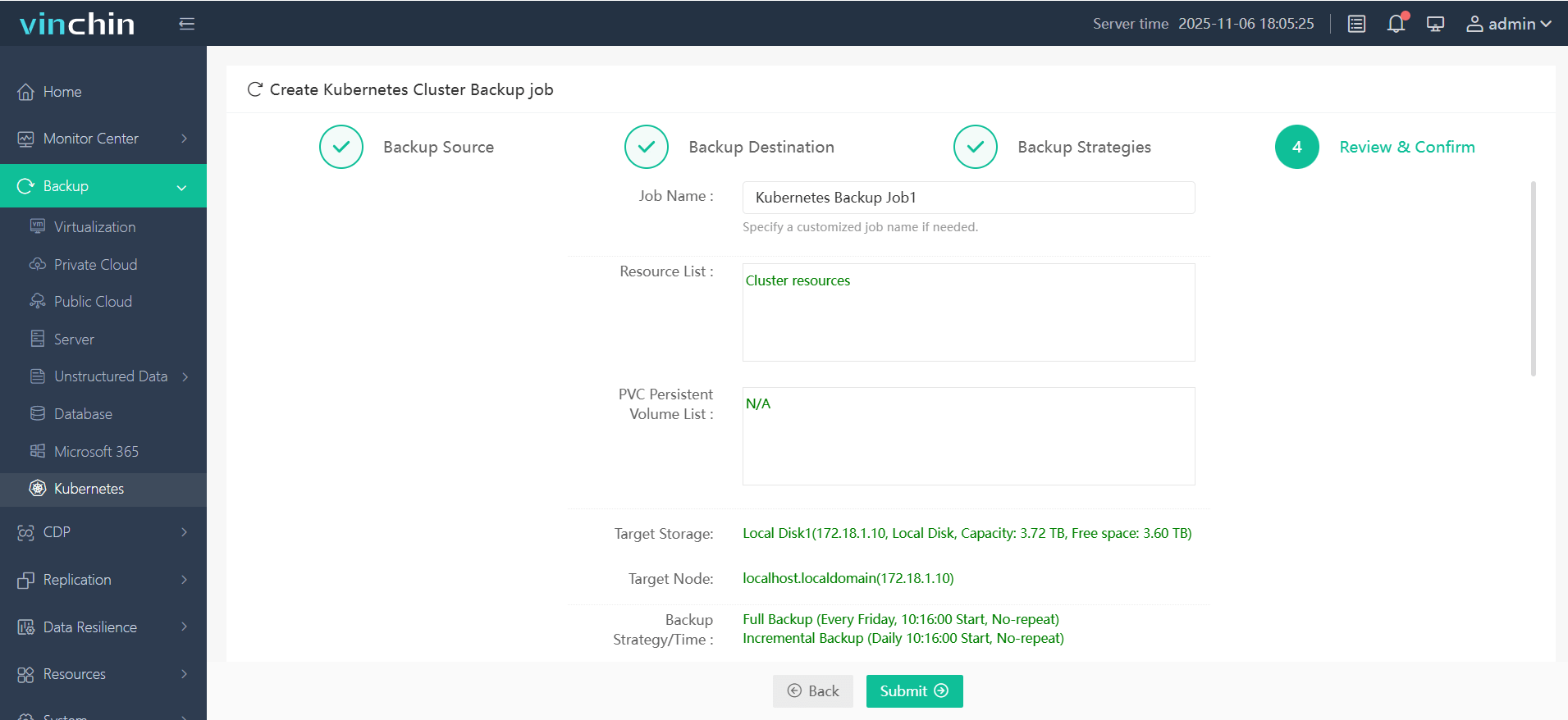
4. Submit the job
Recognized globally by thousands of enterprises for reliability and ease-of-use, Vinchin Backup & Recovery consistently earns top ratings from IT professionals worldwide. Experience every feature free for 60 days—click below to start your trial today!
Kubernetes Backup And Restore FAQs
Q1: How do I handle failed Velero backups caused by limited disk space?
A1: Increase object storage capacity used by BACKUP STORAGE LOCATION settings—or prune old/unneeded backups via VELERO DELETE BACKUP command before retrying jobs.
Q2: What's the safest way to back up stateful applications using PersistentVolumeClaims?
A2: Use solutions supporting consistent PVC snapshots alongside resource YAML exports—for example configure CSI-compatible drivers then run VELERO BACKUP CREATE including relevant namespaces/resources.
Q3: How can I monitor ongoing scheduled backups without logging into each node?
A3: Set up external monitoring tools that watch VELERO SCHEDULE STATUS output—or integrate alerts based on KUBECTL GET BACKUPS results sent via email/slack/webhooks.
Conclusion
Kubernetes backup and restore protects business continuity against unexpected disasters—from human error to hardware failure—with options ranging from simple scripts through automated tools like Velero up to enterprise-grade platforms such as Vinchin offering peace of mind at scale.
Share on:








