-
What Is Enterprise Database Security?
-
Why Enterprise Database Security Matters?
-
Main Threats to Enterprise Databases
-
Method 1: Implementing Encryption for Enterprise Database Security
-
Method 2: Enforcing Access Control and Authentication in Enterprise Databases
-
Method 3: Monitoring and Auditing Database Activity for Enhanced Security
-
Method 4: Applying Regular Patching and Vulnerability Management in Databases
-
How Vinchin Backup & Recovery Secures Your Enterprise Databases?
-
Enterprise Database Security FAQs
-
Conclusion
Enterprise database security is a top concern for organizations of all sizes. With data breaches making headlines and regulations tightening worldwide, protecting sensitive information is no longer optional—it’s essential for survival. In recent years, high-profile incidents have shown how costly a single breach can be in terms of money and reputation. But what does enterprise database security really mean? How do you build a strong defense that keeps your business safe? Let’s break it down step by step—from beginner basics to advanced strategies.
What Is Enterprise Database Security?
Enterprise database security is the set of policies, processes, and technologies that protect an organization’s databases from unauthorized access, misuse, or loss. It covers everything from who can log in to how data is encrypted to how activity is monitored and audited. The goal: keep data confidential, accurate, and available—no matter where it lives or who tries to access it.
Today’s enterprises often use hybrid environments that combine on-premises databases with cloud-based systems or even multi-cloud setups. That means security must extend across all platforms—physical servers in your own data center as well as virtual machines hosted by cloud providers. Good enterprise database security protects not just the data itself but also the management system software (DBMS), applications that connect to it, APIs used for integration with other tools—and even the underlying hardware infrastructure.
Why Enterprise Database Security Matters?
Why should you care about enterprise database security? The answer is simple: the stakes are high—and getting higher every year. A single breach can expose trade secrets or customer records and lead directly to lost trust with clients or partners. Legal penalties are also severe; regulations like GDPR in Europe or HIPAA in healthcare require strict controls over personal information.
According to IBM’s 2023 Cost of a Data Breach Report, the average global cost reached $4.45 million—a 15% increase over three years! Failing audits can result in fines running into millions of dollars—not counting indirect costs like downtime or damage control after an incident.
But compliance isn’t everything; strong security keeps your business running smoothly day-to-day by preventing disruptions caused by cyberattacks or accidental mistakes inside your team. In today’s world where data drives decisions at every level of business operations—databases are both key assets and prime targets.
Main Threats to Enterprise Databases
Enterprise databases face a wide range of threats—from outside attackers as well as insiders who already have some level of access:
Insider threats: Employees or contractors with too much access can steal or leak data—sometimes by accident but sometimes on purpose.
Human error: Weak passwords, misconfigurations during setup changes—or accidental deletions—all open doors for attackers or cause direct data loss.
Malware and ransomware: Malicious software can corrupt files outright—or lock them until you pay up.
SQL injection & other attacks: Hackers exploit vulnerabilities in web apps connected to your DBMS so they can run unauthorized commands.
Unpatched software: Outdated operating systems or DBMS versions are easy targets because their flaws are public knowledge among hackers.
Physical threats: Theft/damage of servers leads directly to loss if physical protections are weak.
Supply chain attacks: Compromised third-party tools (like plugins) provide backdoor access without touching your core systems directly.
Each threat carries serious consequences—from regulatory fines through operational downtime all the way up to permanent loss of critical business information. That’s why layered defenses matter so much—you never want one mistake (or one clever attacker) taking down your entire operation.
Method 1: Implementing Encryption for Enterprise Database Security
Encryption forms one of the strongest lines of defense against unauthorized access—even if someone gets past other barriers like firewalls or login screens! When done right, encryption makes stolen files unreadable without special keys known only inside your organization.
Start by enabling encryption “at rest”—which means encrypting files/tables/databases stored on disk using built-in features offered by most modern DBMS platforms (like Transparent Data Encryption). Next comes “in transit” protection: always use secure protocols such as TLS when sending information between applications/users/cloud endpoints so nothing gets intercepted along its journey across networks.
Don’t forget about backup copies! Encrypt those too since backups often get overlooked during routine audits but contain just as much sensitive info as live production systems do.
Managing encryption keys securely matters just as much as turning encryption on:
1. Store keys separately from encrypted databases
2. Rotate keys regularly according to policy
3. Limit who has permission/access rights over key management tools
For extra safety around highly sensitive fields (credit card numbers/social security IDs/etc.), consider column-level encryption within tables themselves—even if whole-database encryption is already active.
Step-by-Step: Enabling Transparent Data Encryption (TDE) in SQL Server
Let’s walk through enabling TDE—a popular choice—in Microsoft SQL Server:
1. Open SQL Server Management Studio
2. Connect using an account with sysadmin privileges
3. Run CREATE MASTER KEY ENCRYPTION BY PASSWORD = 'yourStrongPassword'
4. Generate certificate: CREATE CERTIFICATE MyServerCert WITH SUBJECT = 'TDE Cert'
5. Back up certificate/key immediately (BACKUP CERTIFICATE ... TO FILE ...)
6. Enable TDE on target DB: ALTER DATABASE YourDatabase SET ENCRYPTION ON
Always test these steps first on non-production systems before rolling out company-wide!
Method 2: Enforcing Access Control and Authentication in Enterprise Databases
Access control ensures only authorized users reach sensitive information—the fewer people with broad permissions…the safer you stay! This principle (“least privilege”) means giving everyone exactly what they need—and nothing more—to do their jobs effectively without exposing unnecessary risk points elsewhere.
Begin by defining user roles clearly inside your DBMS:
1. Assign minimum rights needed per job function
2. Use strong unique passwords everywhere—not just admin accounts!
3. Require multi-factor authentication (MFA) especially for privileged users
4. Regularly review/update permissions whenever staff change roles—or leave entirely
5. Lock/remove unused accounts ASAP; never rely on default credentials left behind after installation
6. For critical actions (like schema changes), require dual approval workflows if possible
Implementing Role-Based Access Control (RBAC)
Role-Based Access Control helps enforce least privilege efficiently:
1. Create custom roles such as ReadOnlyUser/DataEditor/Admin using CREATE ROLE statements
2. Grant specific permissions via GRANT SELECT, GRANT INSERT, etc., only where needed
3. Assign users/groups into these roles rather than granting direct table-level rights individually
This approach simplifies audits later since you see at-a-glance which groups have which powers—and makes onboarding/offboarding faster too!
Method 3: Monitoring and Auditing Database Activity for Enhanced Security
You cannot protect what you cannot see—which makes real-time monitoring/auditing vital parts of any mature enterprise database security plan! These tools help spot suspicious behavior early…before small problems turn into major incidents.
Set up logging/audit trails covering:
Successful & failed login attempts
Changes made against sensitive tables/schemas/configuration settings
Large/bulk exports/downloads performed outside normal hours/patterns
Store logs somewhere tamper-proof—ideally offsite/cloud-based storage separate from production servers themselves—for forensic analysis later if needed!
Review logs regularly looking for red flags such as repeated failed logins/unusual IP addresses/new user creation events/etc.—and configure alerts so admins know instantly when something risky happens instead of finding out days/weeks later during routine checks!
Advanced teams may integrate User & Entity Behavior Analytics (UEBA) solutions alongside native audit logs—these tools analyze patterns over time so anomalies stand out quickly even when attackers try blending into normal traffic flows.
Method 4: Applying Regular Patching and Vulnerability Management in Databases
Attackers love unpatched systems because published exploits make breaking in almost trivial once flaws become public knowledge! Keeping both OS-level patches and DBMS updates current blocks many common attack vectors before they ever reach production environments.
First step? Subscribe directly to vendor bulletins/newsletters announcing new patches/security advisories relevant for every platform you operate—including plugins/extensions commonly installed alongside core products!
When updates arrive:
1.Test thoroughly inside isolated staging/test environments first
2.Apply patches promptly across all affected production nodes
3.Verify successful deployment via version checks/log reviews afterward
Automate patch management wherever possible using configuration management tools/scripts—but always double-check results manually at intervals since automation errors happen too!
Regular vulnerability scans help catch missed updates/misconfigurations early; schedule these monthly at minimum—or weekly if resources allow—for best results long-term!
How Vinchin Backup & Recovery Secures Your Enterprise Databases?
To further strengthen enterprise database protection beyond native controls, organizations increasingly rely on robust backup solutions tailored for complex environments such as Oracle, MySQL, SQL Server, MariaDB, PostgreSQL/PostgresPro, and MongoDB—all supported natively by Vinchin Backup & Recovery's professional platform designed specifically for large-scale IT operations administrators managing diverse infrastructures.
Vinchin Backup & Recovery delivers comprehensive features including incremental backup options for Oracle/MySQL/MariaDB/PostgreSQL/PostgresPro databases; batch backup scheduling; flexible retention policies such as GFS retention; advanced source-side compression optimized for Oracle and SQL Server workloads; plus ransomware protection integrated throughout every workflow layer—ensuring rapid recovery while minimizing storage consumption and administrative overhead across hybrid deployments.
The intuitive web console streamlines backup operations regardless of scale:
Step 1: Select the target database type—for example, select Oracle when protecting mission-critical Oracle workloads
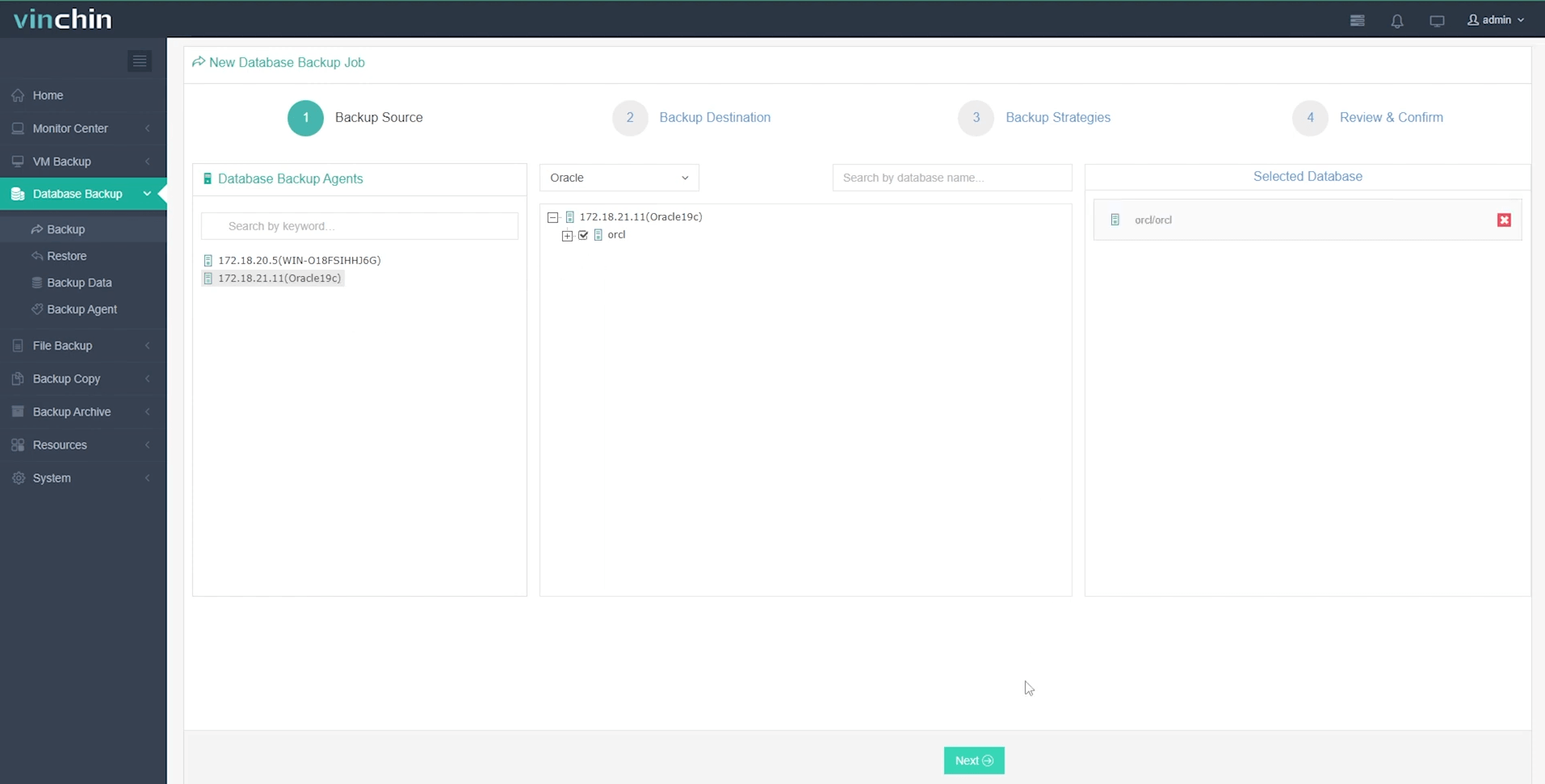
Step 2: Choose designated backup storage
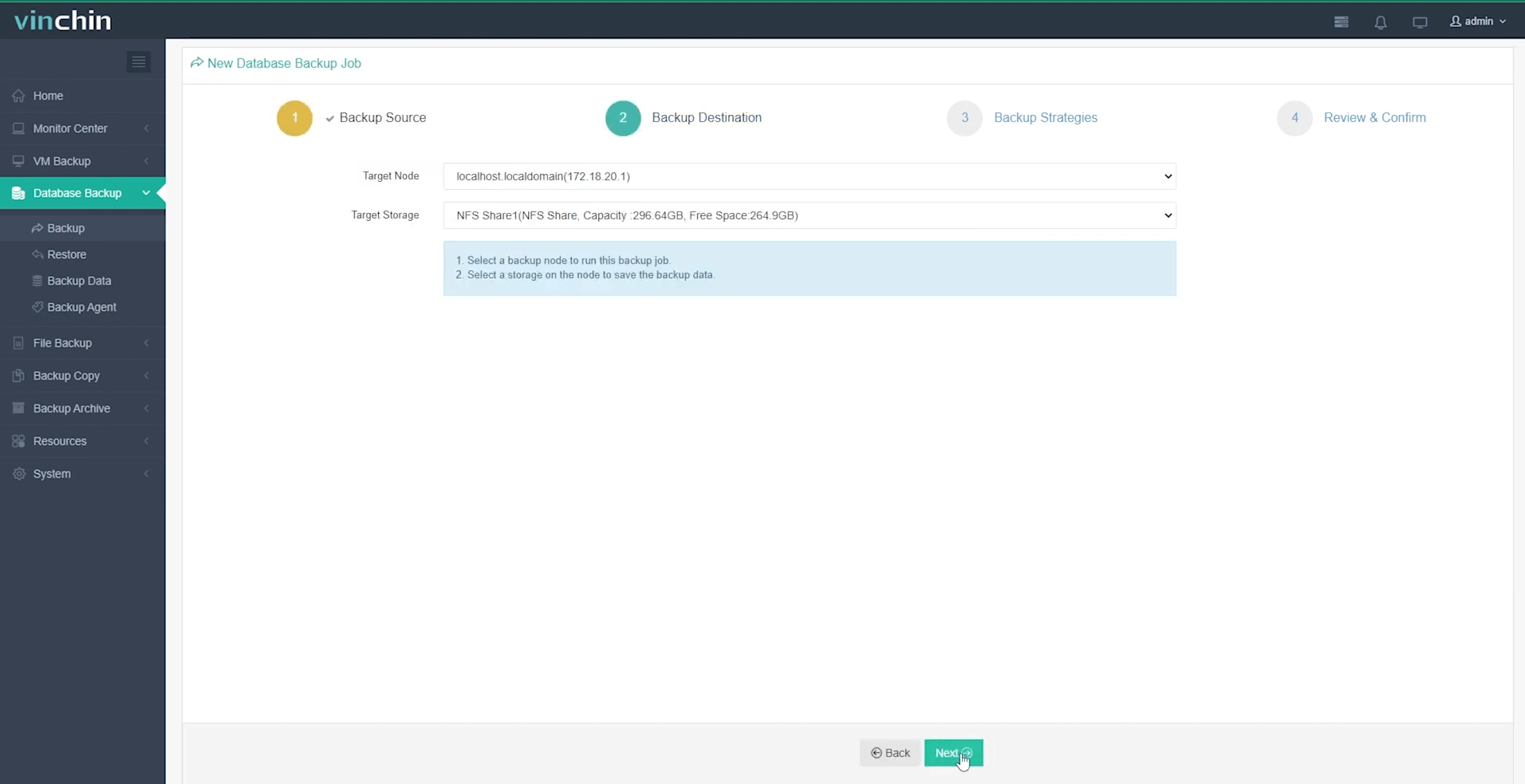
Step 3: Define automated backup strategy parameters
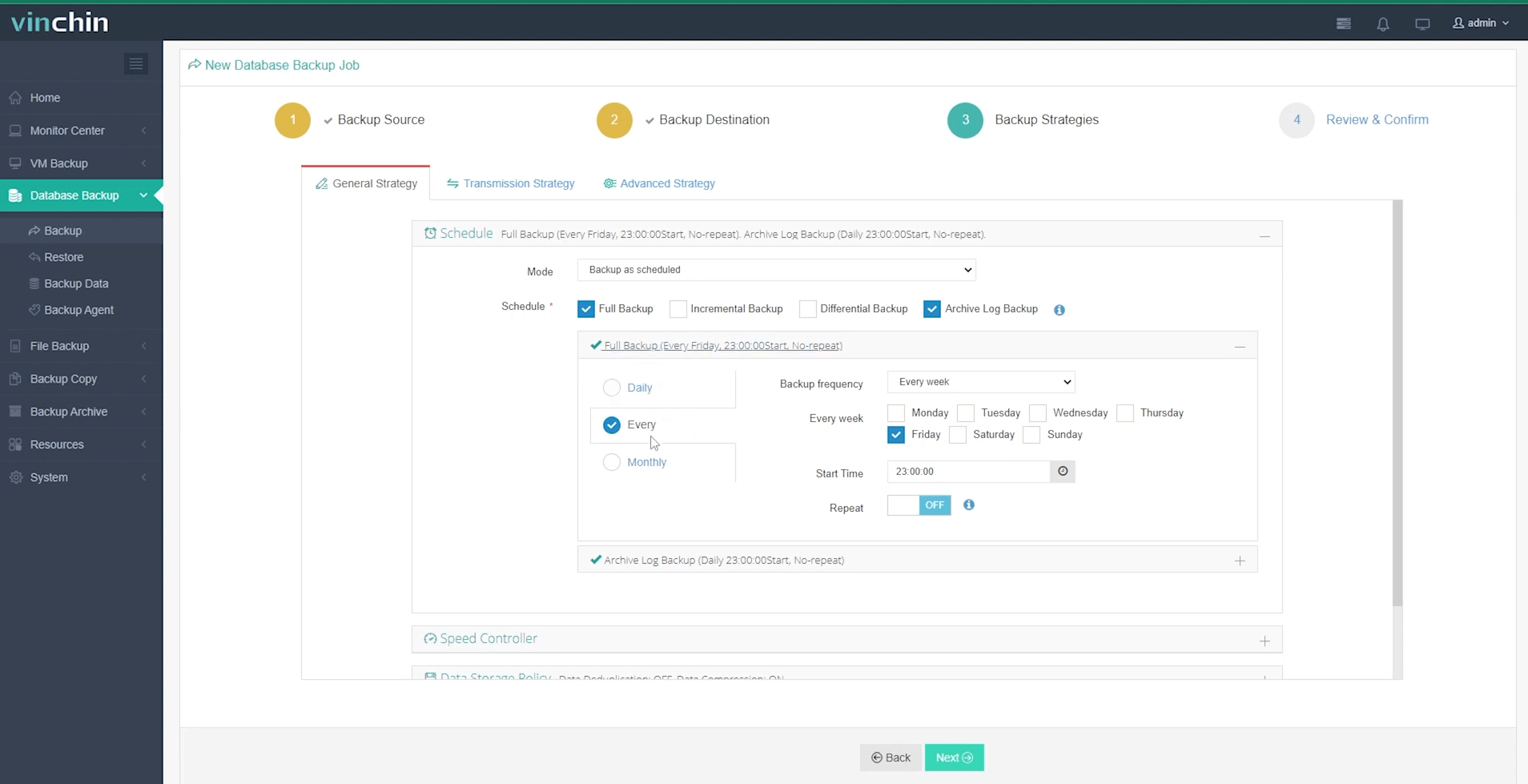
Step 4: Submit the job
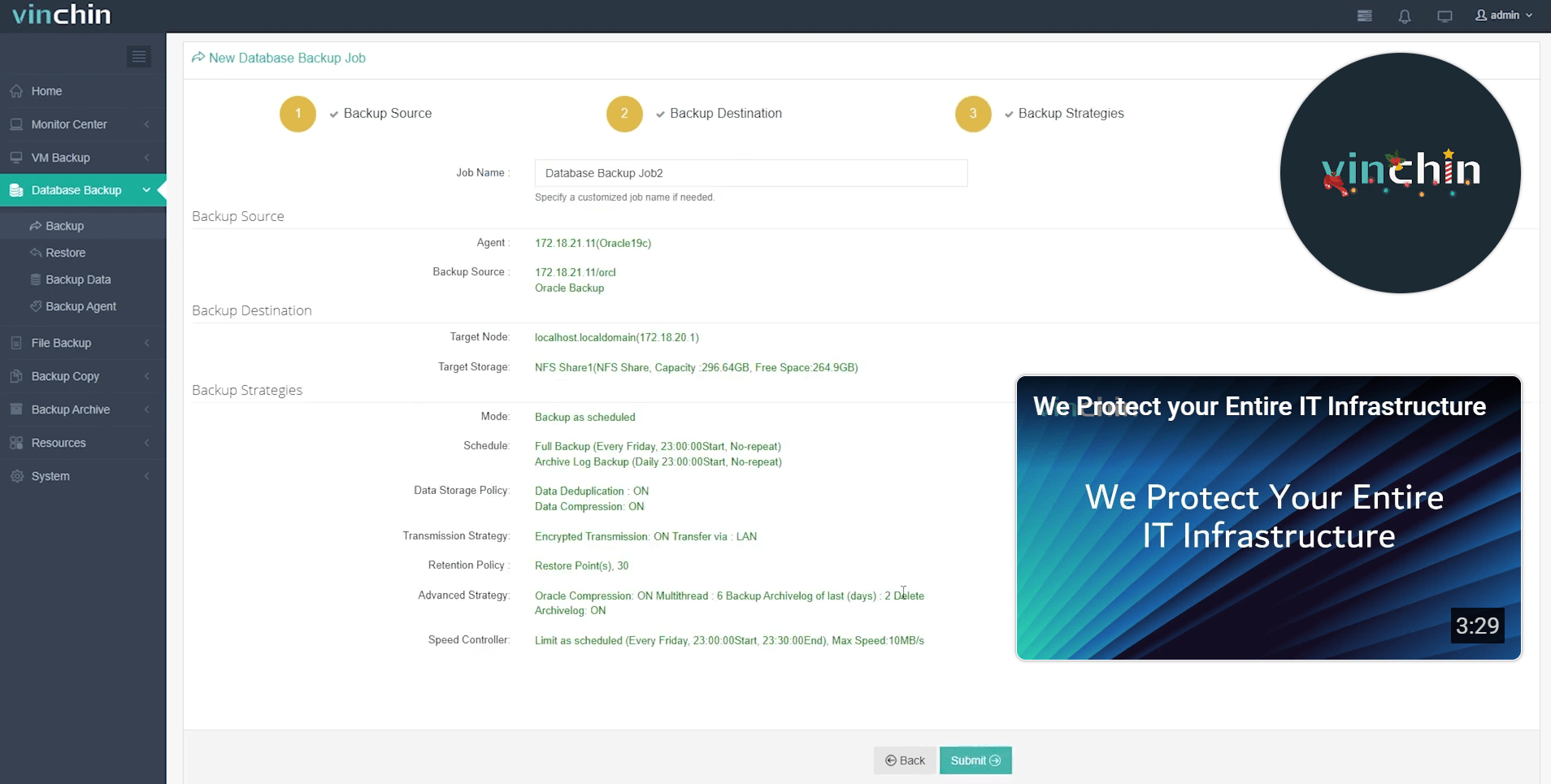
Recognized globally among leading enterprise IT teams—with thousands protected worldwide—Vinchin Backup & Recovery offers a fully featured 60-day free trial so you can experience its reliability firsthand before committing long-term; click below to start safeguarding your environment today.
Enterprise Database Security FAQs
Q1: What immediate action should I take if my monitoring system detects unusual query activity?
A1: Investigate affected accounts right away; temporarily disable suspicious user sessions while reviewing recent changes via audit logs before restoring normal access levels.
Q2: Can I restrict certain employees’ access only during work hours?
A2: Yes; configure time-based restrictions within your authentication system or implement scheduled network firewall rules tied specifically around shift schedules/user groups involved.
Q3: How do I ensure my backups aren’t vulnerable if ransomware hits my primary environment?
A3: Store encrypted backups offsite/in immutable storage locations separate from main infrastructure; test restores regularly so recovery works smoothly under pressure.
Conclusion
Enterprise database security requires ongoing effort—from basic controls like patching/encryption through advanced monitoring/auditing techniques layered together thoughtfully.By combining these best practices,you defend against modern threats while keeping operations resilient.Vinchin strengthens this strategy further with reliable backup/recovery solutions.Stay proactive,and keep learning—the safety of your organization depends on it!
Share on:








