-
What Are Immutable Backups?
-
Why Immutable Backups Stop Ransomware?
-
Method 1: Creating Immutable Backups On Premises With Dell EMC Data Domain
-
Method 2: Creating Immutable Backups On Premises With Rubrik Or Cohesity Appliances
-
Method 3: Using AWS S3 Object Lock For Cloud Immutable Backup Solutions
-
Method 4: Using Azure Blob Storage Immutability For Cloud Backup
-
Unified Kubernetes Backup & Immutability with Vinchin Backup & Recovery
-
Immutable Backups Ransomware FAQs
-
Conclusion
Ransomware attacks are now one of the biggest threats facing IT teams worldwide. In recent years, attackers have shifted tactics—not just encrypting production data but also targeting backup files themselves. If your backups are deleted or encrypted by malware before you notice an attack, recovery becomes impossible—and paying ransom is often the only way out.
How can you stop this nightmare? The answer is simple: immutable backups ransomware cannot touch or destroy. By making your backup copies unchangeable for a set period of time—no matter what—a single clean copy always survives for recovery.
In this guide, we’ll explain what immutable backups are in plain English; show how they block even advanced ransomware; walk through practical ways to set up immutability both on-premises and in the cloud; discuss key planning tips; then introduce how Vinchin makes it all easier with unified management.
What Are Immutable Backups?
Immutable backups are special copies of your data that cannot be changed or deleted until their retention period ends. Think of them as digital safes: once locked inside for a certain time window (days or months), not even an administrator can remove or alter them until that window closes.
This “write once, read many” (WORM) approach is enforced at the storage level—not just by software permissions—which means even if hackers get admin rights or malware runs wild in your environment, those backup files remain untouched. Immutability protects against cyberattacks but also accidental deletions or insider mistakes.
Why does this matter? Because traditional backups can be deleted by anyone with enough access—or by scripts run during an attack—leaving you exposed when disaster strikes.
Why Immutable Backups Stop Ransomware?
Ransomware gangs know that restoring from backup is your last hope after an attack. That’s why modern strains actively search for backup files first—deleting them before encrypting everything else.
Immutable backups break this cycle completely. Even if attackers gain full control over your systems—including admin credentials—they cannot delete or overwrite these protected copies during their retention period.
This means you always have at least one clean version ready for restore without paying ransom or suffering extended downtime. Immutability also helps meet compliance requirements and shields against human error or rogue insiders who might try to sabotage recovery plans.
Method 1: Creating Immutable Backups On Premises With Dell EMC Data Domain
On-premises immutable backup appliances give you direct physical control over sensitive data—a big plus for regulated industries or those wary of public cloud risks. Dell EMC Data Domain systems offer hardware-enforced immutability using their Retention Lock feature.
To enable immutable backups:
Log in to the Data Domain System Manager web interface
Go to Data Management > Retention Lock
Create a new storage unit; enable either Retention Lock Compliance (strictest) or Retention Lock Governance mode depending on policy needs
Point your backup software at this new storage unit
Set desired retention periods per job; once written here no file can be altered/deleted until its timer expires—even by admins
Note: Some features require specific firmware versions/licenses. Plan network access/storage pools ahead of time!
While these systems offer strong local control—and fast restores—they require upfront investment in hardware plus ongoing maintenance.
Method 2: Creating Immutable Backups On Premises With Rubrik Or Cohesity Appliances
Software-defined appliances like Rubrik and Cohesity bring automation and flexibility while still keeping data onsite under your roof—a good fit if you want policy-driven protection without heavy manual work.
To create immutable backups:
Access the appliance’s web interface (Rubrik/Cohesity)
Navigate to either Protection > Policies, then create/select a policy
Enable options labeled either Immutability, Lock, or similar wording within policy settings
Assign this policy directly to relevant backup jobs
Define retention periods per job/policy
Once set up correctly under an immutable policy—even administrators cannot delete/change those files until expiration passes. Both platforms support audit logs plus role-based access controls for extra security layers beyond basic immutability itself.
Remember: Some advanced features may need additional licenses/configuration steps.
Method 3: Using AWS S3 Object Lock For Cloud Immutable Backup Solutions
Cloud storage offers offsite resilience plus elastic scaling—but requires careful configuration so immutability isn’t bypassed accidentally! Amazon S3 provides Object Lock specifically designed for this purpose:
To set up AWS S3 Object Lock:
Open the AWS Management Console > select S3
Create a new bucket (Object Lock must be enabled at creation—it cannot be added later!)
During setup check “Enable Object Lock”; confirm bucket versioning is ON too
After creation go into bucket properties > set default retention mode (Compliance/Governance) as needed
When uploading objects/backups specify individual retention periods if required
Warning: Once enabled Object Lock settings are permanent—you cannot disable them later! Also consider using IAM policies restricting who can write/delete objects within these buckets.
With proper setup no one—including root users—can delete/overwrite locked objects until timers expire, making AWS S3 Object Lock ideal for scalable ransomware-proof cloud archives.
Method 4: Using Azure Blob Storage Immutability For Cloud Backup
Microsoft Azure offers similar protections via Blob Storage immutability policies—a great choice if you already rely on Azure services elsewhere:
To configure Azure Blob Storage immutability:
Log into the Azure Portal
Select target account under Storage Accounts
Go into desired container via the left menu (Containers)—create new if needed
Under container settings find/access “Access Policy”
Enable options labeled either “Immutable Blob Storage,” “Time-based retention,” OR “Legal hold” depending on needs
Define exact duration/time window per object/container
Once applied no blob/file inside that container may be modified/deleted until its timer ends—even with full admin rights.
Tip: Use RBAC/IAM roles carefully so only trusted users manage containers/policies!
Cloud approaches offer geographic redundancy/scalability—but require strict process discipline around permissions/configuration changes compared with local appliances.
Unified Kubernetes Backup & Immutability with Vinchin Backup & Recovery
Building upon these foundational methods, organizations seeking streamlined enterprise-grade Kubernetes protection should consider Vinchin Backup & Recovery—a professional solution purpose-built for robust data security and operational simplicity. As an enterprise-level platform, Vinchin Backup & Recovery delivers comprehensive Kubernetes-native capabilities including full and incremental cluster-level backups, fine-grained restore down to namespace/application/PVC/resource levels, WORM-style immutability enforcement, cross-cluster/cross-version recovery, and intelligent automation through customizable policies. These features collectively empower businesses with resilient ransomware defense, seamless workload migration across environments, granular restore flexibility, automated compliance adherence, and optimized resource usage—all managed centrally from one intuitive interface.
The web console of Vinchin Backup & Recovery makes protecting Kubernetes workloads remarkably straightforward. Launching an immutable backup typically involves four clear steps:
1. Just select VMs on the host
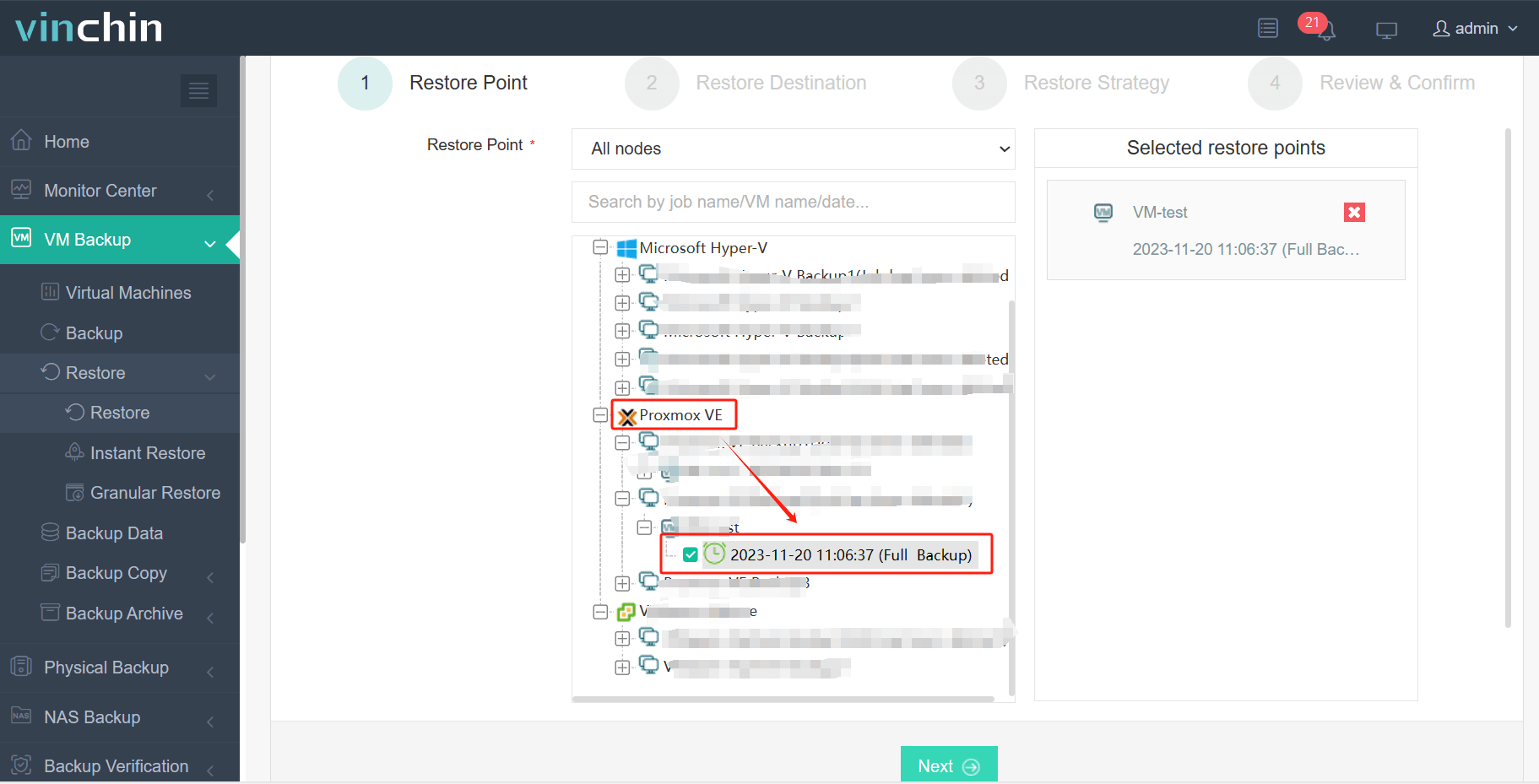
2.Then select backup destination
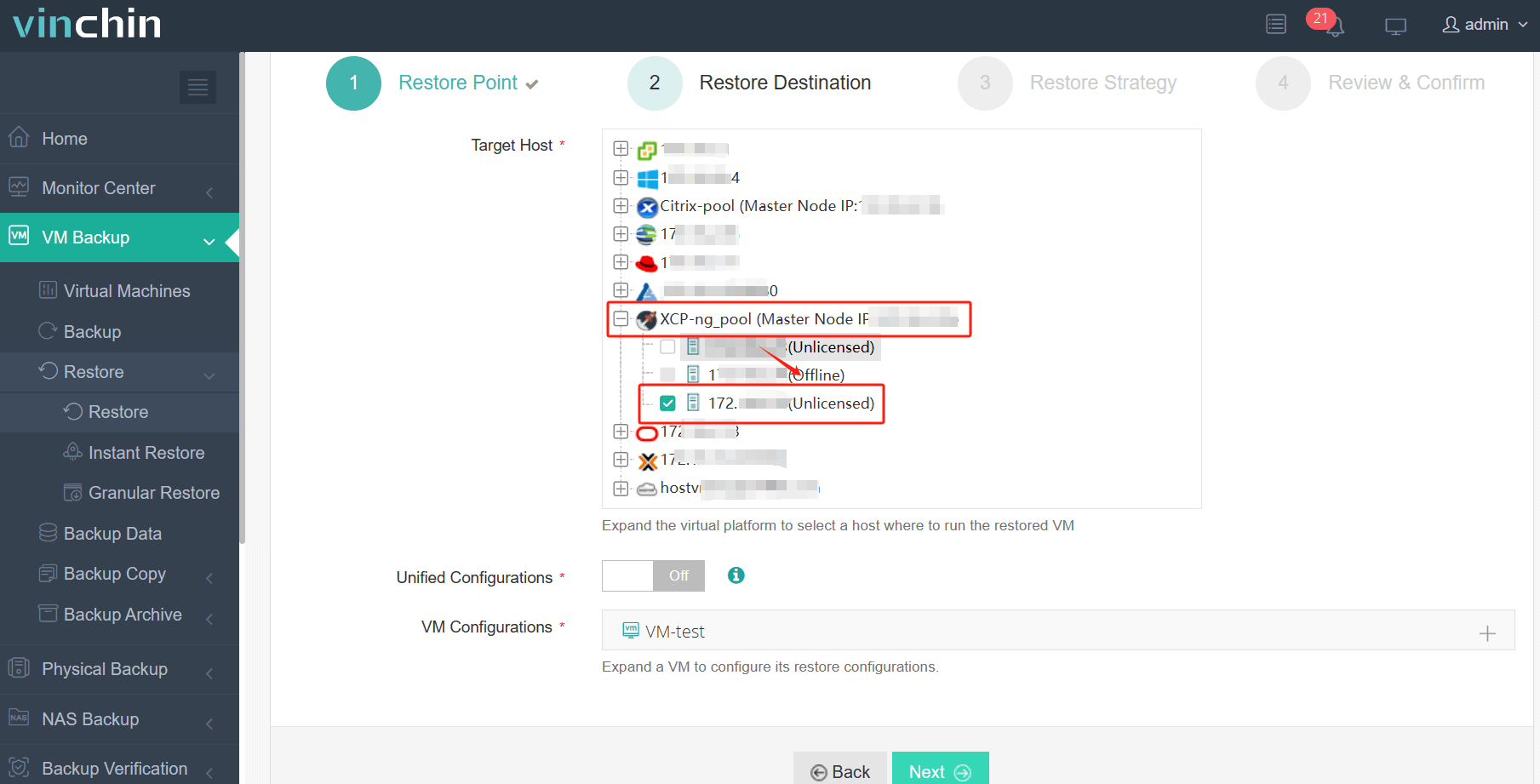
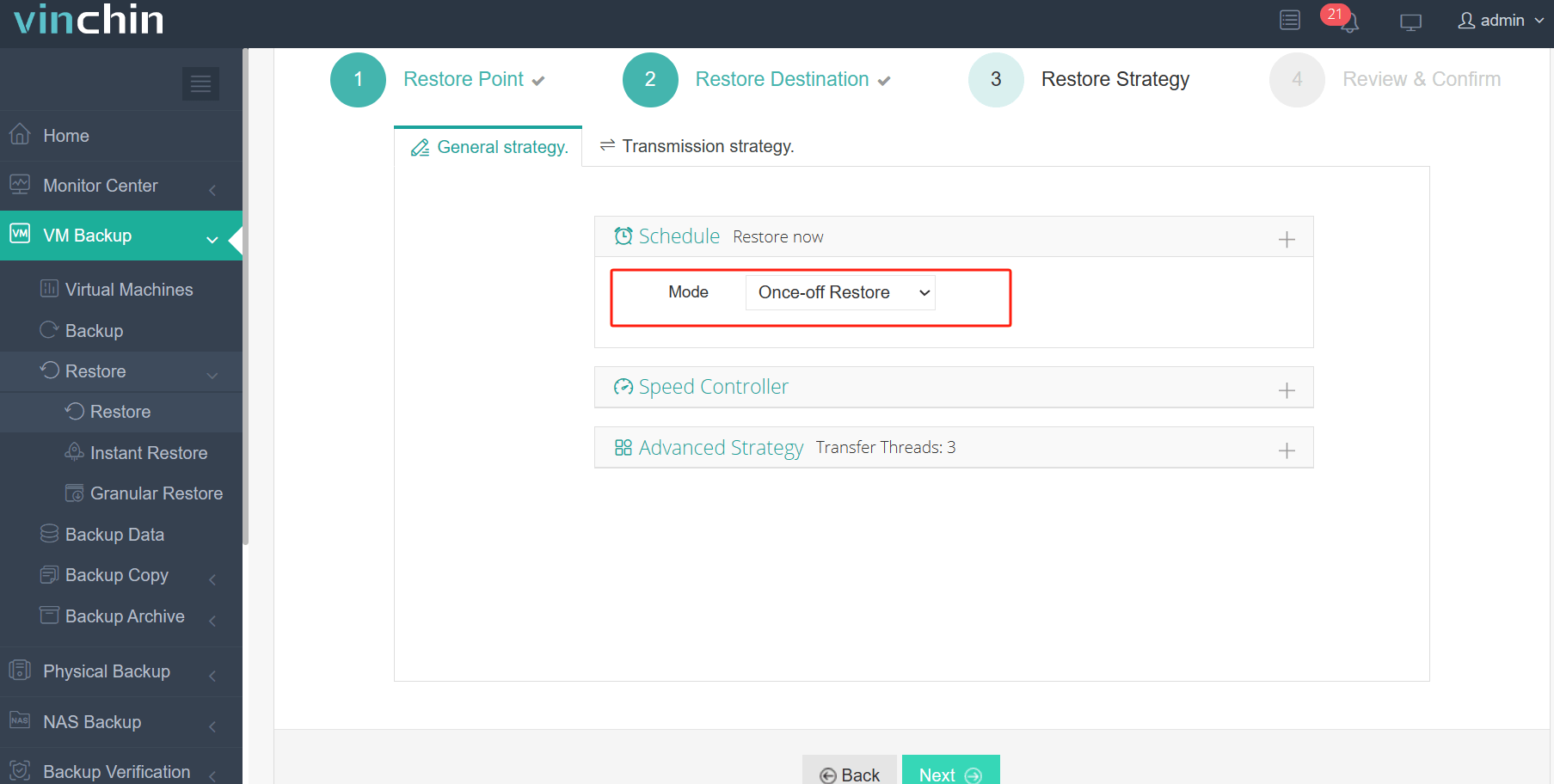
3.Select strategies
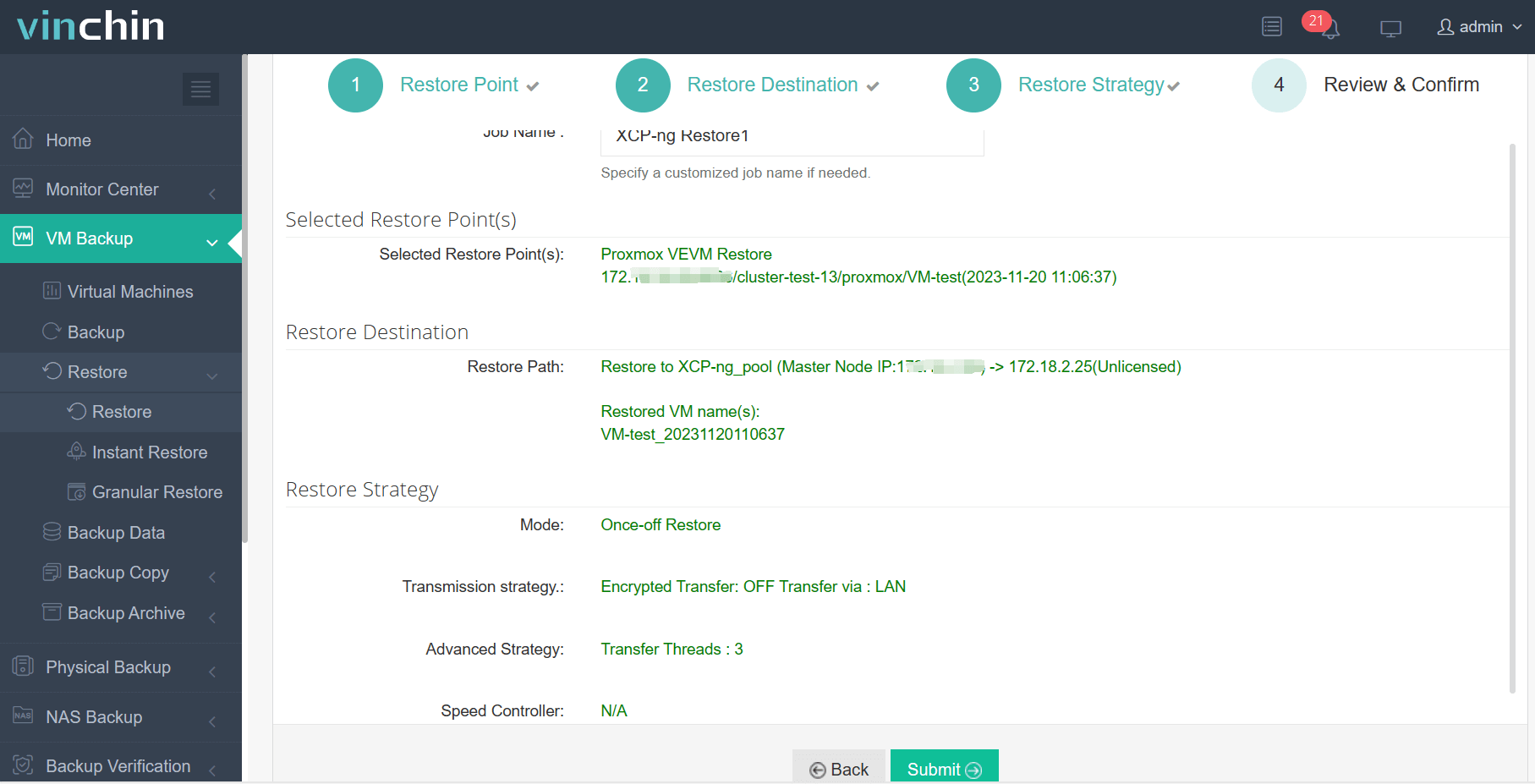
4.Finally submit the job
Recognized globally with top ratings and trusted by thousands of enterprises, Vinchin Backup & Recovery offers a fully featured 60-day free trial—experience world-class data protection today by clicking download below!
Immutable Backups Ransomware FAQs
Q1: Can I integrate immutable backups into my existing hybrid workflow?
A1: Yes—you can combine local/cloud repositories with centralized scheduling/policy enforcement using compatible tools like Vinchin.
Q2: Does enabling immutability slow down my regular backup operations?
A2: No significant impact occurs during writes; however large-scale restores may depend on underlying storage/network speeds.
Q3: What should I do if someone tries deleting an immutable copy before expiry?
A3: Attempted deletions will fail automatically—the system blocks removal/modification actions until configured timer expires.
Conclusion
Immutable backups form your strongest line of defense against modern ransomware attacks—ensuring safe recoveries even after worst-case breaches occur across local/cloud environments alike. Try Vinchin today for seamless end-to-end protection built around true WORM principles—and sleep easier knowing your business continuity plan is bulletproof!
Share on:






