-
What are vSphere Integrated Containers?
-
How to Deploy vSphere Integrated Containers?
-
How to Manage Containers with VIC in Day-to-Day Operations?
-
How to Troubleshoot Common Issues in Production Environments?
-
Protecting Your VMware Environment with Vinchin
-
vSphere Integrated Containers FAQs
-
Conclusion
Containers have changed how we build and run applications. They offer speed, flexibility, and portability—but many enterprises rely on VMware vSphere for their core infrastructure. How can you bring container agility to your existing VMware environment without abandoning what works? That's where vSphere Integrated Containers (VIC) come in. This guide explores what VIC is, how it works under the hood, how to deploy it step by step, manage containers efficiently—and how to protect your VMware VMs running containers with confidence.
What are vSphere Integrated Containers?
vSphere Integrated Containers (VIC) is a solution from VMware that lets you run container workloads natively on your vSphere infrastructure. It bridges traditional virtual machines (VMs) with modern containers so both can coexist seamlessly on one platform.
With VIC, you don't need to choose between VMs or containers—you get both. Each container runs inside its own lightweight VM called a Container VM, managed by a special appliance known as the Virtual Container Host (VCH). Developers interact with VIC using familiar Docker tools while IT teams retain full control using vCenter features like DRS (Distributed Resource Scheduler), HA (High Availability), and vMotion.
Why does this matter? Many organizations want to modernize their application delivery but cannot abandon their stable VM-based systems overnight. VIC allows gradual adoption of containers without disrupting proven workflows or sacrificing enterprise-grade security.
Key Benefits of Using VIC
Let's break down why enterprises choose VIC:
1. Seamless Integration: Run VMs and containers side-by-side on existing clusters—no need for separate hardware or siloed teams.
2. Enterprise Features: Leverage all core vSphere capabilities—like snapshots, resource controls, live migration—for both VMs and Container VMs.
3. Security & Isolation: Each container gets its own VM boundary—reducing risk compared to shared-kernel models used elsewhere.
4. Familiar Tools: Developers use Docker CLI as usual while admins manage everything through vCenter—no steep learning curve required.
If you're looking for modernization without disruption—or want to avoid managing two separate platforms—VIC offers a practical path forward.
How to Deploy vSphere Integrated Containers?
Deploying VIC may seem daunting at first glance—but if you follow these steps carefully you'll be up and running quickly even if you're new to hybrid cloud setups.
Prerequisites Checklist
Before installing anything:
1. Confirm you're running at least VMware ESXi 6.x+ with corresponding version of vCenter Server
2. Verify Enterprise Plus license covers target clusters
3. Ensure DNS records exist for all ESXi hosts plus reverse lookups resolve correctly
4. Prepare storage locations accessible from every host involved—NFS shares work well but VSAN datastores are supported too
5. Download latest release package from official VMware GitHub page
6. Extract certificate thumbprint needed during setup using OpenSSL command line:
openssl x509 -in /etc/vmware/vpxd/vpxd.crt -sha1 -noout -fingerprint
7. Decide which Distributed Port Groups will serve as bridge/public networks
Method 1: Deploying With vic-machine CLI Tool
The most common way admins install Virtual Container Hosts is via vic-machine utility provided in download bundle:
1) Upload extracted files onto jumpbox/server able to reach both ESXi hosts and management interfaces over network
2) Open terminal window then run following command template:
vic-machine-linux create \ --target 'vcenter.company.com' \ --user 'administrator@vsphere.local' \ --password 'YourPasswordHere' \ --compute-resource 'ClusterName' \ --image-store 'DatastoreName' \ --bridge-network 'BridgePortGroupName' \ --public-network 'PublicPortGroupName' \ --name 'MyFirstVCH'
Replace values above according to local environment details shown inside Web Client UI screens (Hosts & Clusters, Networking, etc).
3) Wait until script completes successfully—it will output connection info including IP address/port number assigned
Method 2: Deploying With HTML5 Plugin Wizard
Prefer point-and-click? Recent releases include browser-based wizard available after importing OVA file into inventory:
1) Log into Web Client using administrator credentials
2) Right-click target cluster > select “Deploy OVF Template” > browse downloaded OVA file
3) Follow prompts assigning compute/storage/network resources per earlier checklist items
4) Once deployed open plugin dashboard under “Shortcuts” menu > launch guided configuration workflow
Post-deployment Validation Steps
After creating first Virtual Container Host always verify connectivity before inviting developers onboard:
1) From admin workstation install latest Docker client tools compatible with target version
2) Set environment variable pointing CLI at newly created endpoint:
export DOCKER_HOST=tcp://<VCH-IP>:2376
3) Test basic operation by running simple info query:
docker info
If output lists expected number/types of nodes/resources then everything worked!
How to Manage Containers with VIC in Day-to-Day Operations?
Once deployed successfully most questions shift toward daily operations: How do developers launch apps? How do admins monitor health? What about scaling securely?
Developer Workflow Using Familiar Tools
Developers interact with Virtual Container Hosts exactly like any remote Docker daemon—they don't need direct access inside data center walls! Typical workflow looks like this:
1) Export correct DOCKER_HOST value matching assigned endpoint/IP address received after deployment
2) Authenticate using TLS certificates generated during setup phase
3) Run standard commands such as docker run, docker ps, docker logs against remote engine
All images pulled/pushed flow through registry service configured earlier—or fallback automatically onto public sources if none specified locally
Admin Monitoring Through Admiral UI And Beyond
Admins gain visibility/control via several channels:
Use built-in Admiral web interface (
https://<Admiral-IP>:8282) for graphical view over current state—including active/inactive workloads per host/resource poolCheck event logs directly within standard Web Client screens under “Monitor” tab
Integrate alerts/actions into broader automation stacks using REST APIs exposed by underlying appliances
Want deeper analytics? Connect existing monitoring suites such as VMware Aria Operations Manager (formerly known as vRealize Operations)—these recognize new object types introduced by VIC automatically once registered
Scaling Up Or Down Responsively
Need more capacity fast? Simply deploy additional Virtual Container Hosts targeting different clusters/datastores/networks depending on business needs—or scale back unused ones safely when demand drops off again later
How to Troubleshoot Common Issues in Production Environments?
Even seasoned pros hit snags sometimes! Here's how experienced ops teams tackle frequent pain points:
Certificate Errors During Connection Attempts
If seeing errors about invalid/untrusted cert chains double-check CA root bundles installed locally match those issued during original deployment process—or temporarily bypass checks using --tlsverify=false flag strictly while testing only
Network Misconfiguration Symptoms
Are some services unreachable despite appearing healthy elsewhere? Inspect settings applied atop Distributed Port Groups especially around Promiscuous Mode/MAC Address Changes/Forged Transmits toggles—all three must be enabled correctly otherwise packets may drop silently midstream
Resource Contention Or Unexpected Restarts
Notice slowdowns/crashes affecting only certain tenants/projects intermittently? Review DRS affinity/anti-affinity rule assignments ensuring enough headroom exists per node/resource pool combination supporting bursty loads typical among microservice architectures
Stale Image Caches Or Registry Sync Failures
If builds fail due missing/outdated layers check synchronization status reported under Image Registry Service dashboard—and clear caches manually where necessary before retrying affected jobs again.
Protecting Your VMware Environment with Vinchin
Vinchin Backup & Recovery provides robust protection for VMware environments, including those running vSphere Integrated Containers. It supports over 15 major virtualization platforms such as VMware, Hyper-V, Proxmox VE, oVirt, XCP-ng, and more, with a primary focus on VMware. This solution is designed to meet the needs of complex enterprise environments.
Vinchin provides advanced backup features such as incremental backups to optimize storage, deduplication, and powerful restore options. Its capabilities also include seamless V2V migration, instant recovery, encryption, and LAN-free backups, offering a reliable solution for ensuring data availability and minimizing downtime.
1.Just select VMware VMs on the host
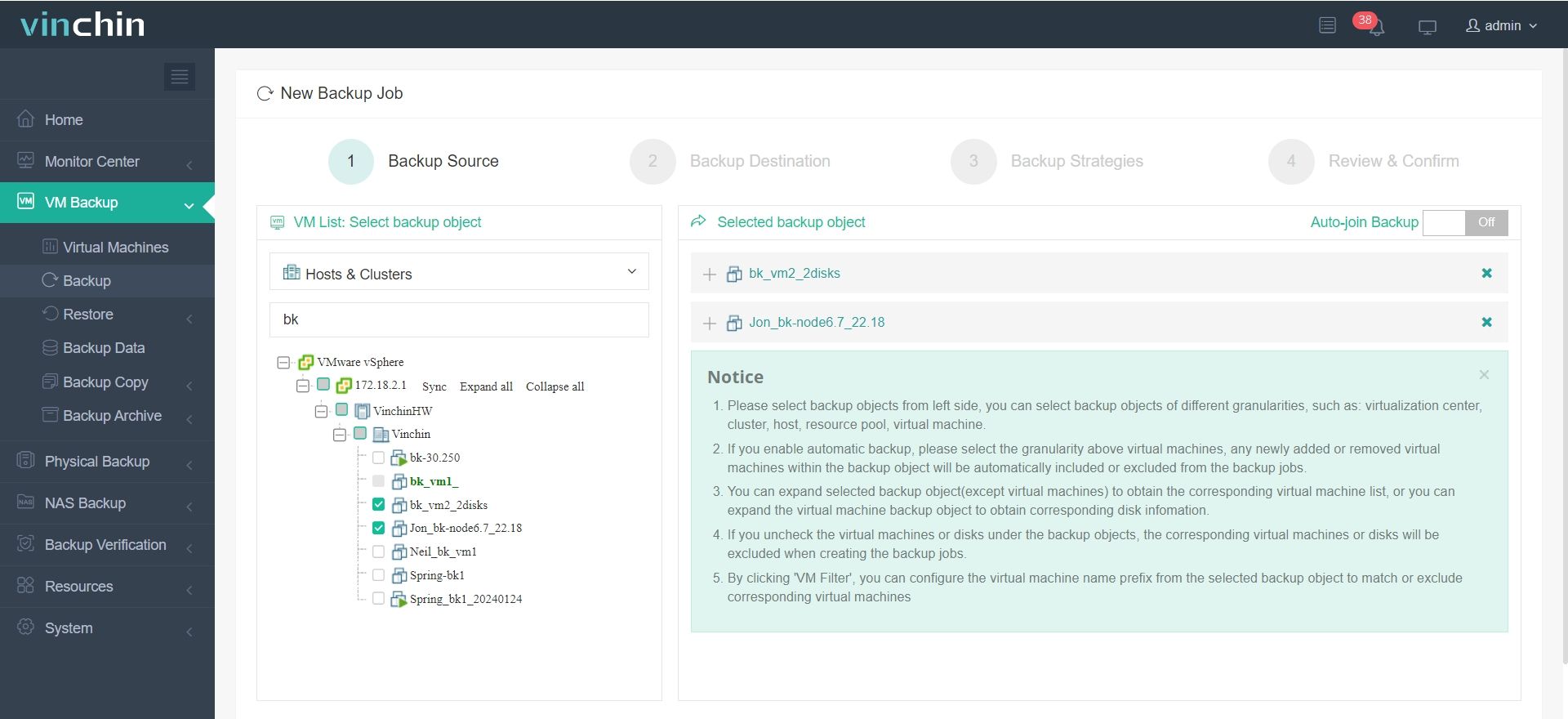
2.Then select backup destination
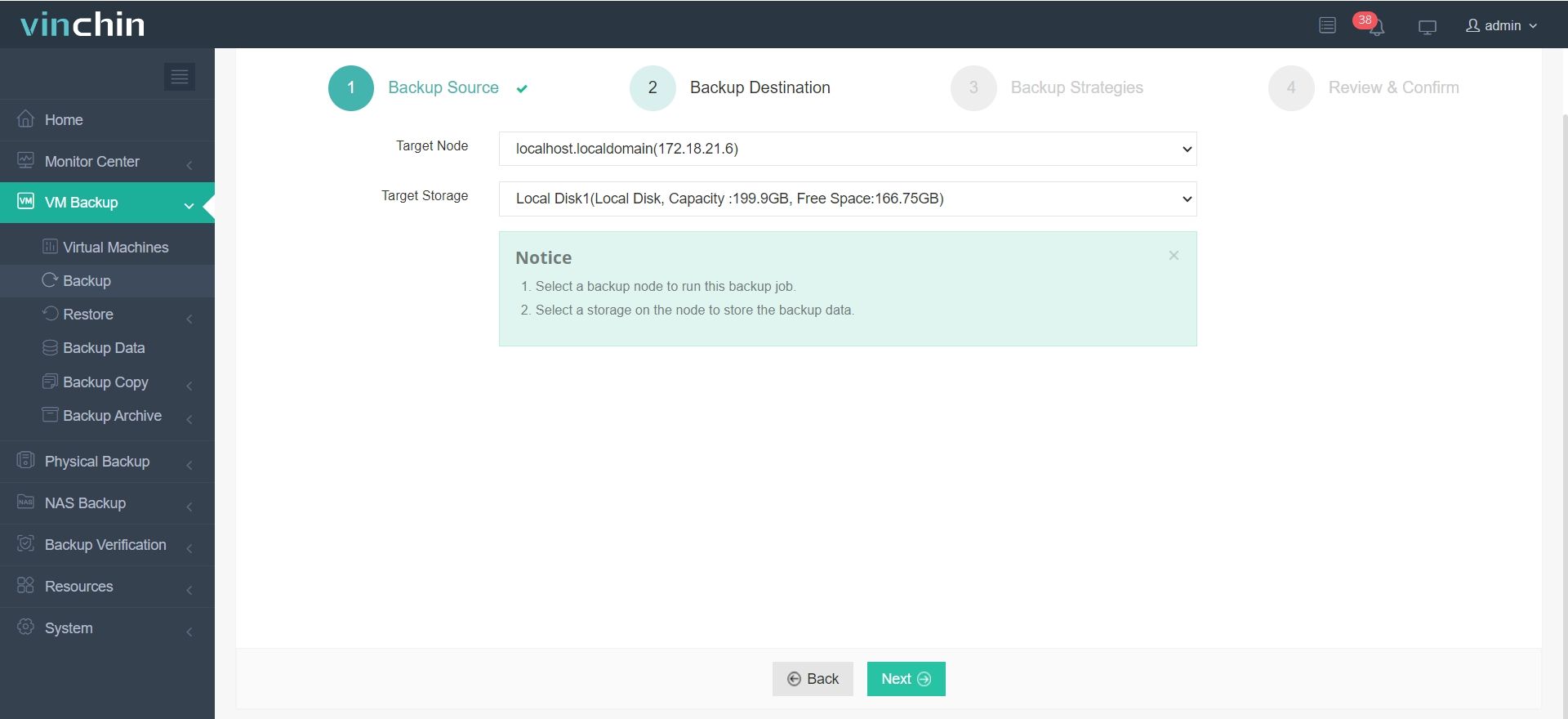
3.Select strategies
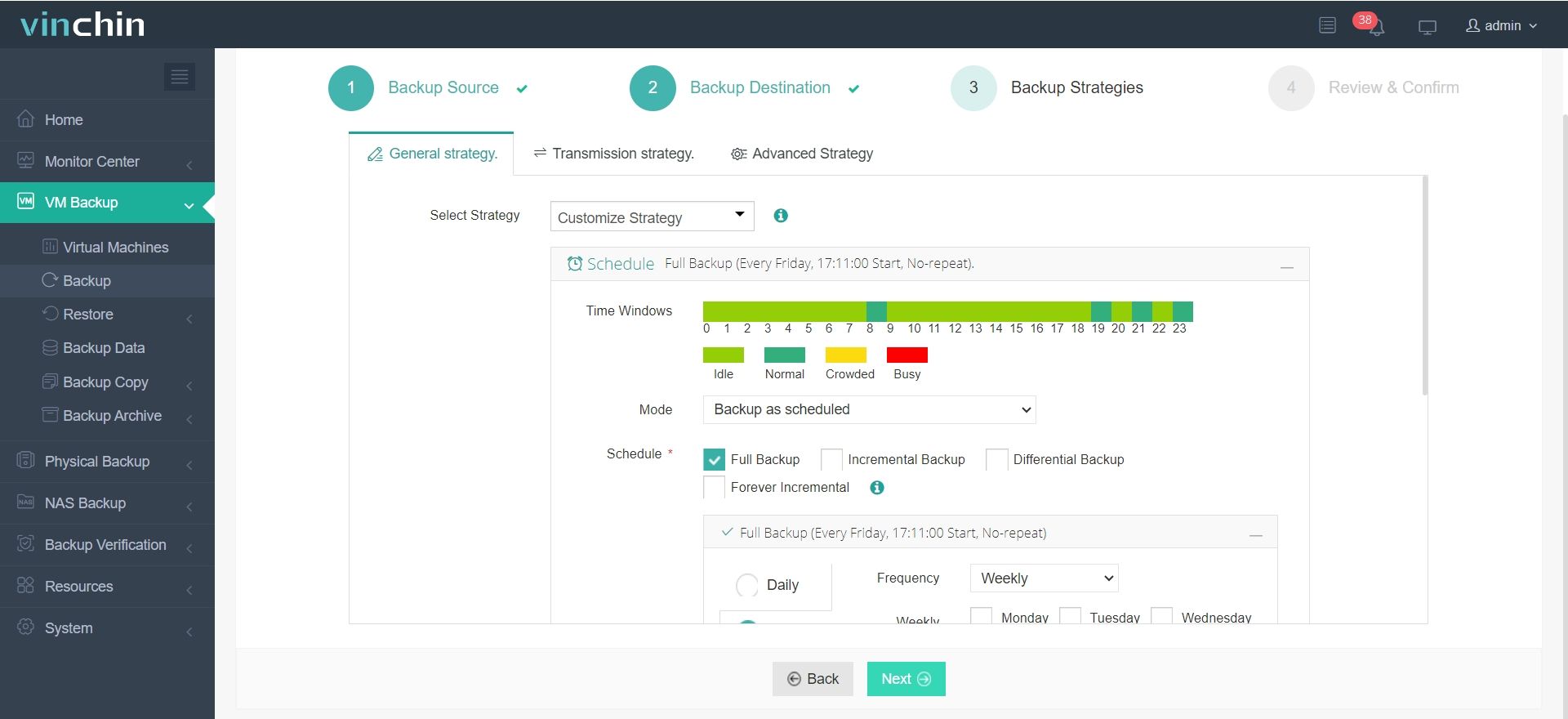
4.Finally submit the job
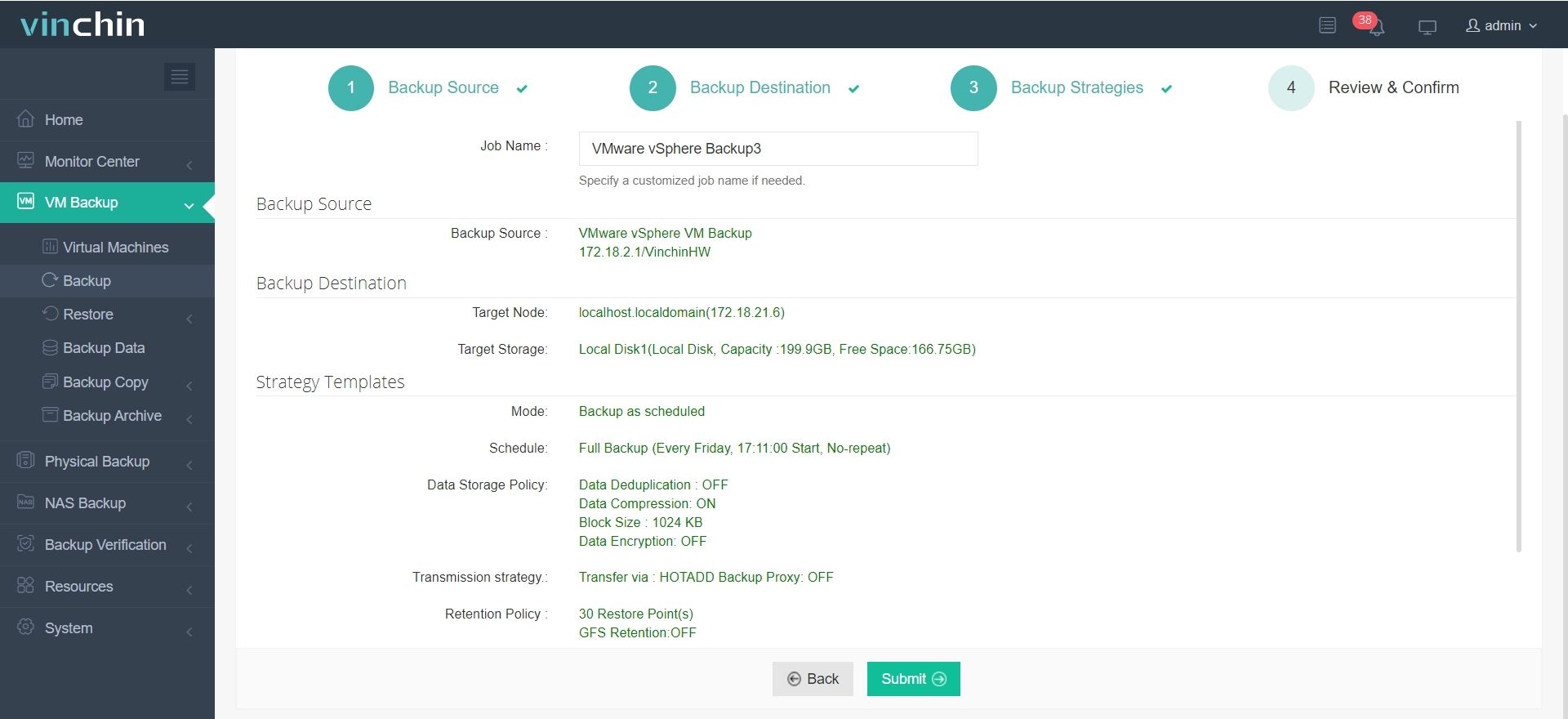
Try before you commit — Vinchin offers a full-featured 60-day trial.
Test it in your own environment. Reach out to us.
vSphere Integrated Containers FAQs
Q1: Can I migrate my existing non-containerized apps into vsphere integrated containers easily?
A1: Yes—you can refactor legacy apps gradually by wrapping them in lightweight Photon-based images then deploying via familiar workflows without rearchitecting everything upfront.
Q2: How do I grant developers access only to specific projects within my cluster?
A2: Create dedicated resource pools mapped against custom roles/groups limiting scope accordingly through standard RBAC controls enforced natively within Web Client UI screens.
Q3: What should I check first if my developer reports failed image pulls?
A3: Verify local registry service availability then confirm outbound firewall/NAT rules permit connections toward upstream sources required fetching missing layers dynamically when needed.
Conclusion
vSphere Integrated Containers enable seamless integration of modern app delivery with trusted virtualization tools. By following best practices, anyone can unlock its potential. For mixed environment protection, consider evaluating Vinchin Backup & Recovery alongside other reliable solutions for robust data security.
Share on:







