-
What Is AWS S3 Ransomware?
-
Common AWS S3 Ransomware Attack Vectors
-
Why AWS S3 Needs Ransomware Protection?
-
Native AWS Tools for Preventive Ransomware Protection
-
Enterprise File Backup Solution for AWS S3 Ransomware Protection with Vinchin Backup & Recovery
-
FAQs About Advanced AWS S3 Ransomware Protection
-
Conclusion
Ransomware is no longer just a threat to local servers—it now targets cloud storage like Amazon S3 as well. With so much business-critical data stored in S3 buckets, aws s3 ransomware protection has become essential for every operations administrator. In this guide, you’ll learn what makes S3 vulnerable, how attacks happen, and how to build strong defenses using both native AWS tools and advanced solutions like Vinchin.
What Is AWS S3 Ransomware?
Ransomware is malicious software that encrypts or deletes your files until you pay a ransom. In Amazon S3 environments, attackers may use stolen credentials to access your buckets and either encrypt objects with their own keys or delete them outright. Sometimes they set up lifecycle rules that erase data after a short time—leaving you scrambling for recovery options if you lack proper safeguards.
Unlike traditional ransomware that exploits software flaws, most S3 attacks rely on compromised access keys or weak permissions settings. Once inside your environment, attackers can lock down your data using features like Server-Side Encryption with Customer Provided Keys (SSE-C) or simply wipe out entire buckets.
Common AWS S3 Ransomware Attack Vectors
Understanding how ransomware reaches your S3 buckets helps you defend against it more effectively. Attackers often exploit gaps in identity management or misconfigured policies rather than hacking AWS itself.
Some common attack vectors include:
Leaked IAM access keys posted online or harvested through phishing.
Overly broad permissions granted via IAM roles or bucket policies.
Publicly accessible buckets due to misconfigured permissions.
Abuse of SSE-C encryption by supplying attacker-controlled keys.
Malicious lifecycle rules that delete objects quickly after infection.
Exploiting automation scripts with embedded credentials left unsecured.
Each vector highlights why aws s3 ransomware protection requires both prevention and detection strategies—not just one layer of defense.
Why AWS S3 Needs Ransomware Protection?
Amazon designed S3 for high durability and availability—but not specifically for ransomware resilience. If an attacker gains access through leaked credentials or poor policy controls, they can cause massive damage fast: encrypting files with unknown keys or deleting critical objects beyond recovery if versioning isn’t enabled.
The shared responsibility model means AWS secures its infrastructure while you must secure your data and access controls. Without layered aws s3 ransomware protection—including immutability settings, monitoring tools, backups, and incident response plans—you risk downtime, financial loss, compliance violations, and permanent data loss from even a single compromised account.
Native AWS Tools for Preventive Ransomware Protection
AWS offers several built-in features to help prevent unauthorized changes to your data—and each plays a role in effective aws s3 ransomware protection strategies.
Before making changes in production environments, always test procedures first on non-critical resources to avoid accidental lockouts or deletions.
1. Enable Object Lock for Immutability
Object Lock lets you store objects using a write-once-read-many (WORM) model so they cannot be deleted or overwritten during the retention period—a powerful defense against ransomware tampering.
When creating a new bucket in the console: select Enable Object Lock under Advanced settings.
For existing buckets: enable versioning first under Properties > Bucket Versioning, then turn on Object Lock.
To set retention: upload an object; select its version; click Actions > Retain until date; choose duration (7–30 days is typical); pick Compliance mode for strictest enforcement (Warning: Compliance mode prevents deletion even by admins until expiration).
CLI example:
aws s3api create-bucket --bucket my-bucket --object-lock-enabled-for-bucket aws s3api put-object-retention --bucket my-bucket --key my-object --retention "RetainUntilDate=2024-07-31T00:00:00Z"
2. Turn On Versioning
Versioning keeps multiple versions of each object so you can restore previous copies if files are overwritten or deleted—intentionally or by malware.
In the console: select bucket > Properties > Bucket Versioning > Enable > save changes.
CLI:
aws s3api put-bucket-versioning --bucket my-bucket --versioning-configuration Status=Enabled
Note: Enabling versioning increases storage costs since all versions are retained unless manually cleaned up later—but it’s vital insurance against accidental deletions by attackers.
3. Enforce MFA Delete
MFA Delete adds another layer by requiring multi-factor authentication before permanently deleting any object version—making it harder for attackers who only have stolen credentials.
Only available via CLI/API; not supported via web console yet.
First enable versioning as above
Find MFA serial number under IAM > Users > Security credentials
Run:
aws s3api put-bucket-versioning --bucket my-bucket --versioning-configuration Status=Enabled,MFADelete=Enabled --mfa "SERIAL_NUMBER MFA_CODE"
4. Restrict Use of SSE-C Encryption
Attackers sometimes abuse SSE-C encryption by providing their own keys—locking out legitimate users from their own data!
To reduce this risk:
Create/edit an IAM policy restricting use of
x-amz-server-side-encryption-customer-algorithmheader except for approved users/applications using the Condition blockAttach policy only where needed
By combining these preventive controls—immutability via Object Lock; recoverability via Versioning; deletion control via MFA Delete; tight encryption key usage—you make it much harder for ransomware actors to destroy your cloud assets quickly.
Enterprise File Backup Solution for AWS S3 Ransomware Protection with Vinchin Backup & Recovery
While native tools provide foundational security layers against threats targeting Amazon S3 file storage, organizations seeking comprehensive aws s3 ransomware protection benefit from enterprise-grade solutions such as Vinchin Backup & Recovery. This professional platform supports backup across mainstream file storage systems—including Amazon S3 object storage (as highlighted here), Windows/Linux file servers, and NAS devices—with exceptionally fast backup speeds surpassing competitors thanks to proprietary technologies like simultaneous scanning/data transfer and merged file transmission.
Vinchin Backup & Recovery delivers robust protection through features such asincremental backup support, wildcard filtering capabilities, multi-level compression options, cross-platform restore between file server/NAS/object storage targets, and end-to-end data encryption—all working together to maximize efficiency while minimizing risk exposure across hybrid environments.
The intuitive web console streamlines backup workflows into four simple steps tailored specifically for Amazon S3 scenarios:
1.Just select the object to backup
2.Then select backup destination
3.Select strategies
4.Finally submit the job
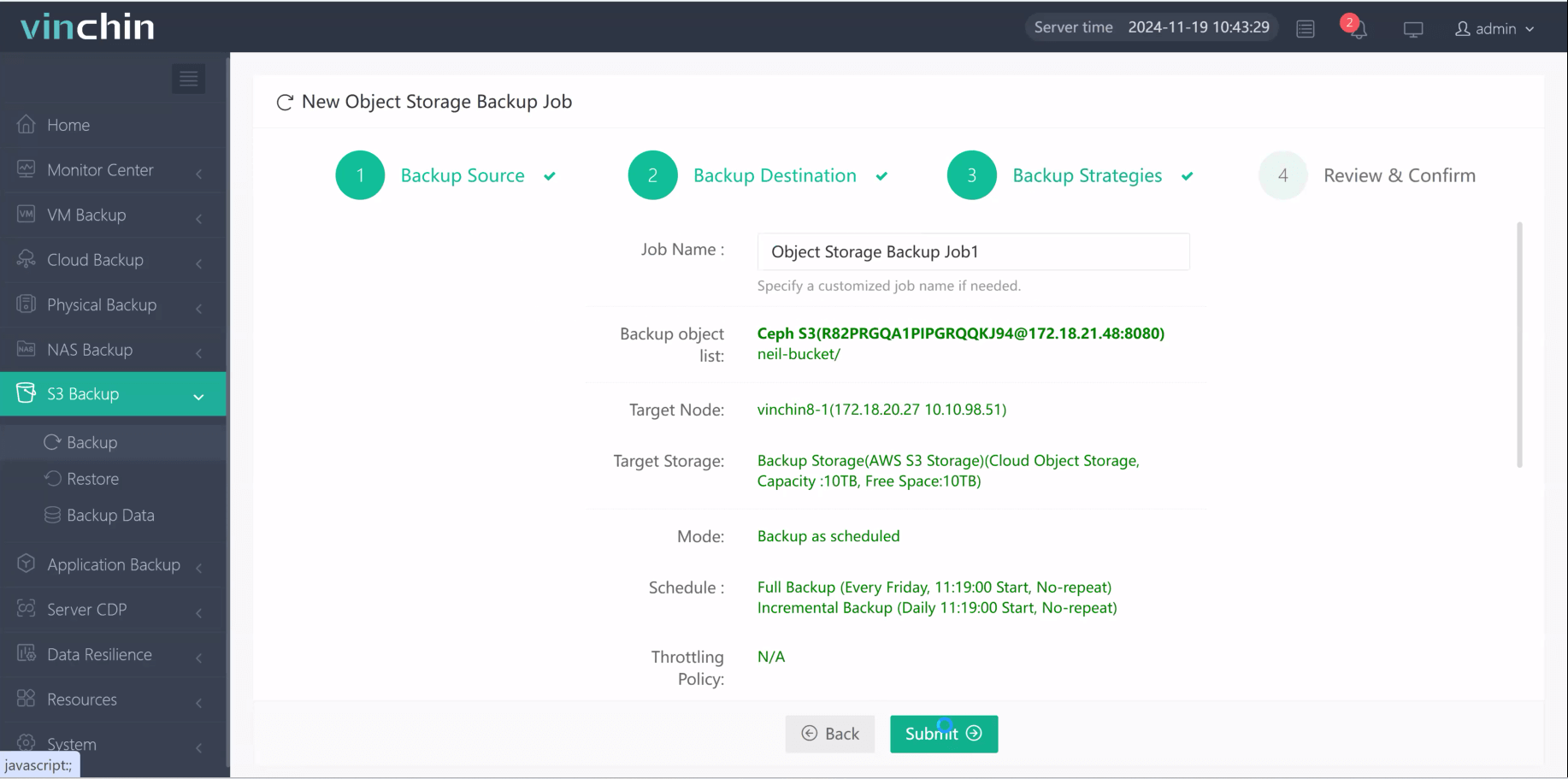
Recognized globally with top customer ratings and trusted by thousands of enterprises worldwide, Vinchin Backup & Recovery offers a fully featured free trial valid for 60 days—click below to experience industry-leading cloud data protection firsthand!
FAQs About Advanced AWS S3 Ransomware Protection
Q1: What should I do if my encryption keys are compromised during a ransomware attack?
A1: Immediately rotate affected keys using KMS/AWS Console then restore clean copies from immutable backup sources secured elsewhere—not just within same account/region!
Q2: How can I protect critical data stored across multiple accounts?
A2: Use cross-account replication plus centralized monitoring/logging tools—and ensure consistent application of policies/playbooks everywhere involved!
Q3: Does enabling advanced protections slow down normal business operations?
A3: Most controls have minimal impact day-to-day but always test performance impacts beforehand—especially when activating features like Object Lock/MFA Delete at scale.
Conclusion
Ransomware threats targeting Amazon S3 are rising fast—but layered defenses combining native tools with enterprise solutions like Vinchin deliver true aws s3 ransomware protection at every level without compromise! Secure your cloud assets now before attackers strike next time.
Share on:







