-
What Needs Protection?
-
Why Data Protection Matters
-
International Regulations Shaping Data Protection
-
Institutional Support and Policy
-
Common Research Data Protection Measures
-
Vinchin: A Trusted Partner for Research Data Protection
-
Data Protection in Research FAQs
-
Conclusion
Science thrives on data. It drives discovery, proves theories, and opens new questions. But data can also be fragile. In the wrong hands, it can lead to harm. That's why data protection in research is not just good practice — it's a responsibility.
In today's global scientific community, researchers handle sensitive information. It may include genetic data, patient health records, experimental formulas, or large collaborative datasets. This information must be protected — during collection, storage, analysis, sharing, and publication.
Let's take a hard look at how to keep these data safe in research.
What Needs Protection?
Research data encompasses diverse forms:
Personal Data: Health records, genetic information, or participant details in social studies.
Proprietary Data: Patents, experimental designs, or confidential industry collaborations.
Sensitive Findings: Data linked to national security or vulnerable populations.
A single breach can compromise privacy, derail projects, or damage reputations. For instance, a stolen laptop containing unencrypted patient data could lead to legal penalties and loss of public trust.
Why Data Protection Matters
The first reason is simple: trust. Research institutions, funders, and participants trust scientists to handle data with care. If this trust is broken, it can derail careers, compromise studies, and even hurt people.
Second, laws and ethics demand it. Even outside specific jurisdictions like the European Union's GDPR, most ethical frameworks urge scientists to protect personal and confidential data. Leaks can lead to identity theft, discrimination, or other harms.
Third, the digital world is dangerous. Devices are lost. Hackers are clever. Governments may demand access. Without protection, research data is easy prey.
International Regulations Shaping Data Protection
International policies play a pivotal role in shaping modern data protection standards, with the European Union's General Data Protection Regulation (GDPR) emerging as a transformative force since its 2018 implementation. Widely regarded as a global benchmark, the GDPR establishes rigorous requirements for personal data handling through principles that prioritize individual rights. These include mandates for organizations to obtain explicit consent and communicate data uses transparently, restrictions on repurposing information beyond its original collection purpose, and obligations to limit data gathering to only what is strictly necessary. One of its most distinctive provisions—the "right to erasure"—empowers individuals to demand the deletion of their data under specific circumstances. The regulation's extraterritorial reach continues to influence global research practices; for instance, UK-based studies involving EU participants remain subject to GDPR compliance even after Brexit, underscoring its enduring cross-border impact.
Beyond broad frameworks like the GDPR, sector-specific regulations address niche challenges across industries. In the U.S. healthcare sector, the Health Insurance Portability and Accountability Act (HIPAA) enforces strict technical safeguards such as encryption and access controls to protect sensitive medical records.
Research institutions face complementary requirements from funding bodies like the U.S. National Institutes of Health (NIH), which mandate detailed data management plans emphasizing anonymization techniques and secure storage protocols for funded projects.
Meanwhile, the UK Research Councils (RCUK) advocate for a balanced approach, encouraging researchers to prioritize open data sharing while requiring proactive identification of ethical and legal barriers during study design. Together, these layered policies reflect an evolving global landscape where data protection increasingly intersects with research ethics, technological capacity, and transnational collaboration.
Institutional Support and Policy
Universities and research organizations play a big role in data protection. They must set clear policies and provide tools and training.
Many leading universities require data management plans as part of research proposals. These plans describe how data will be collected, stored, shared, and protected.
Common elements include:
Data classification: Some data is public. Some is private. Some is sensitive. Classifying data helps decide how much protection it needs.
Restricted access: Not all researchers need full access to all data. Permissions should match roles.
Data retention rules: How long must data be kept? When and how should it be destroyed?
Harvard, for example, ranks research data in five levels — from public to highly sensitive. Each level has matching safeguards. Sensitive data may need encrypted storage, anonymization, or ethics review board approval.
Stanford, MIT, Berkeley, and Oxford have similar policies. They emphasize transparency, privacy, and accountability.
Common Research Data Protection Measures
Encryption and Authentication
Encryption renders data unreadable without a decryption key. You can also enable two-factor authentication (2FA). That means logging in requires both a password and a time-sensitive code from your phone or other device. It blocks most common hacking methods.
Anonymization and De-identification
When research involves human subjects, protecting identity is crucial. So researchers should use data anonymization and pseudonymization to hide private information. For example, replacing detailed addresses with regions. This protects identity while preserving the value of the data.But over-anonymizing can ruin data quality. The goal is balance: protect privacy without harming research.
Data Sharing
Major funding bodies now require data sharing. The U.S. National Institutes of Health, the U.K.'s Research Councils, and the European Commission all promote open science — with safety measures.
Their policies stress:
Sharing only after sensitive data has been processed.
Planning data protection from the start.
Using controlled-access repositories for restricted data.
Following privacy laws and ethical rules.
Even with safeguards, some data can't be shared. This keeps research transparent without compromising privacy.
Vinchin: A Trusted Partner for Research Data Protection
Protecting research data doesn't have to be complicated. The right tools can make it easier, safer, and more reliable.
Vinchin Backup & Recovery is designed to meet the data protection needs of various organizations facing digital transformation. With support for multiple virtualization platforms like VMware, Proxmox, XensServer, Oracle, Hyper-V and popular databases, Vinchin ensures high availability and secure data backups. Features such as deduplication, compression, and cloud integration help optimize storage and improve recovery times. Additionally, Vinchin complies with regulations like GDPR, safeguarding sensitive information and ensuring business continuity in case of disasters. This enables healthcare providers to focus on patient care while maintaining reliable data security.
It only takes 4 steps to backup your virtual machine or database with Vinchin Backup & Recovery:
1.Select the backup object.
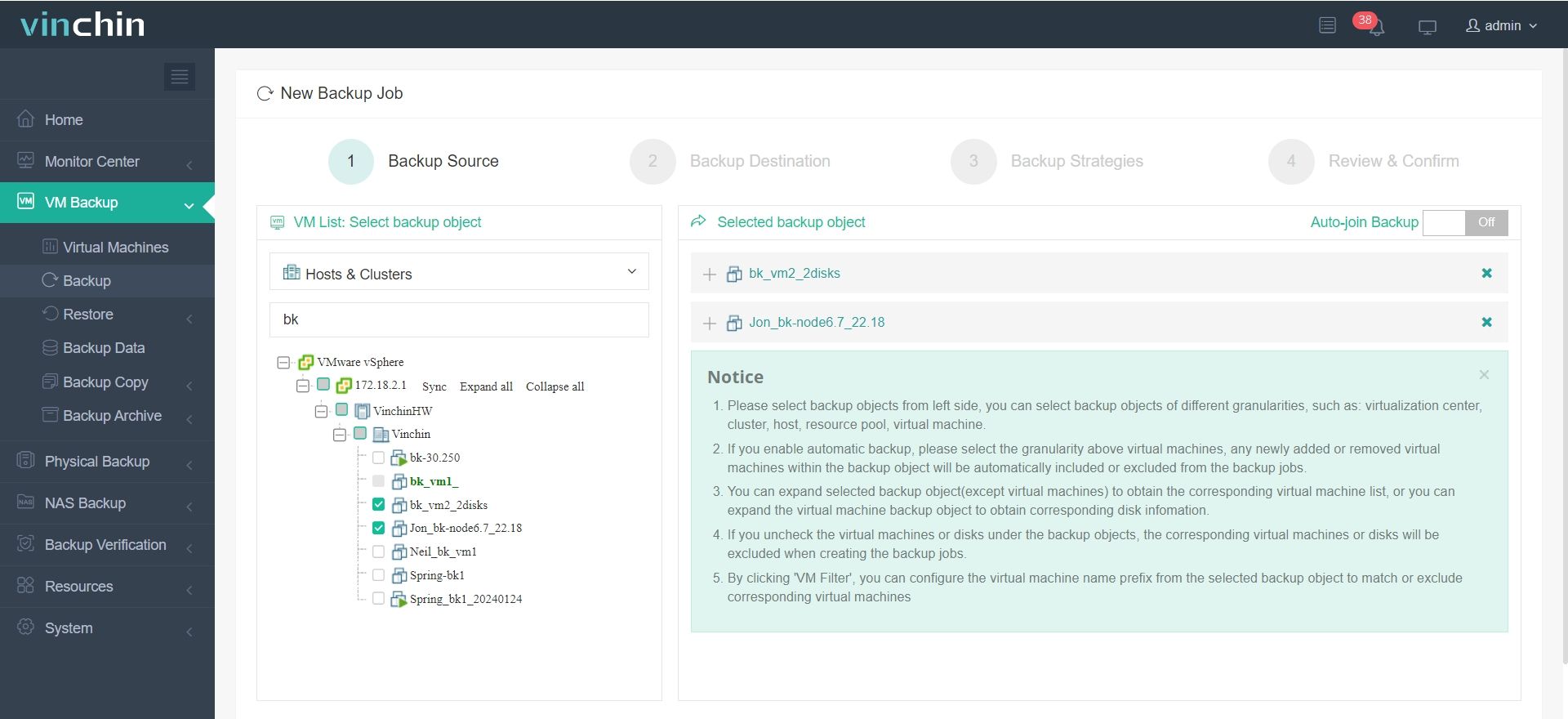
2.Select backup destination.
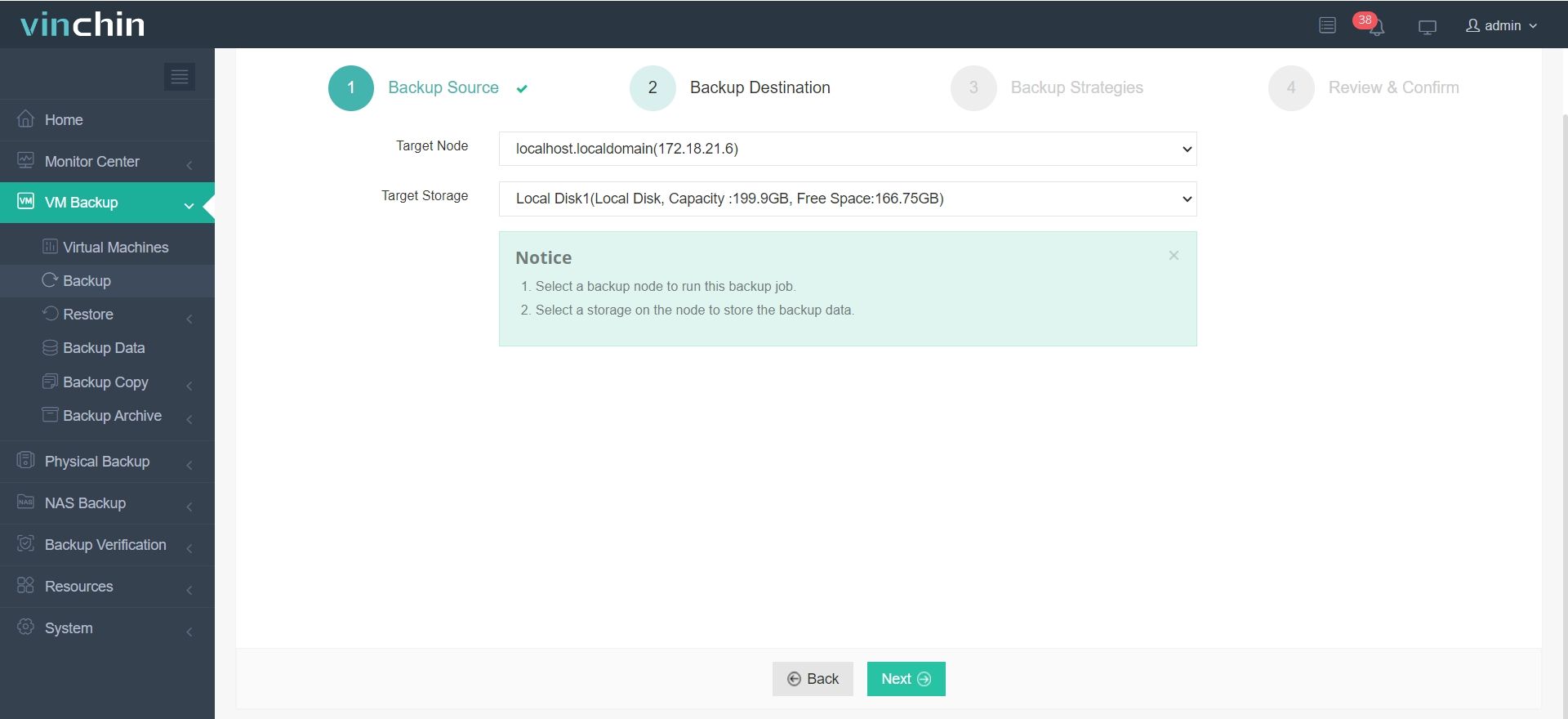
3.Configure backup strategies.
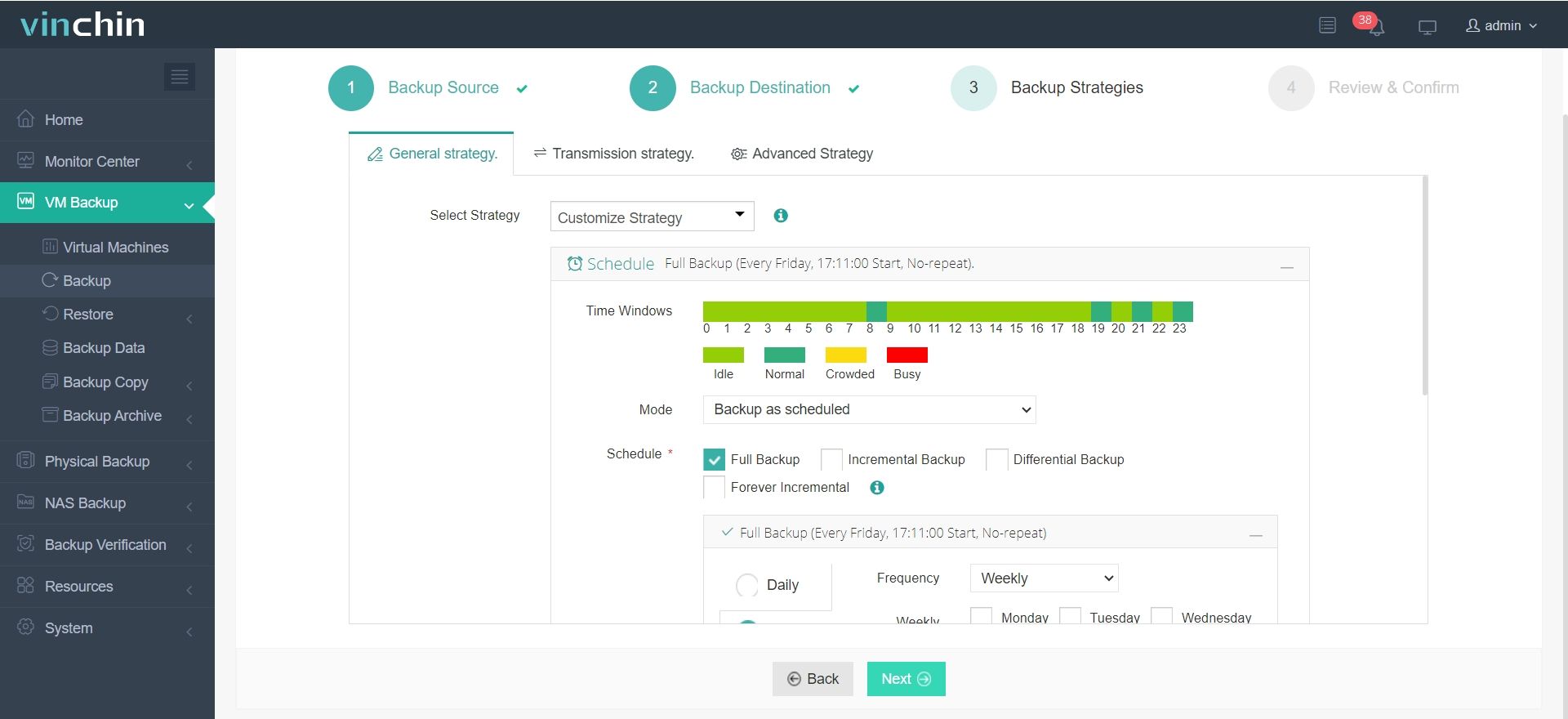
4.Review and submit the job.
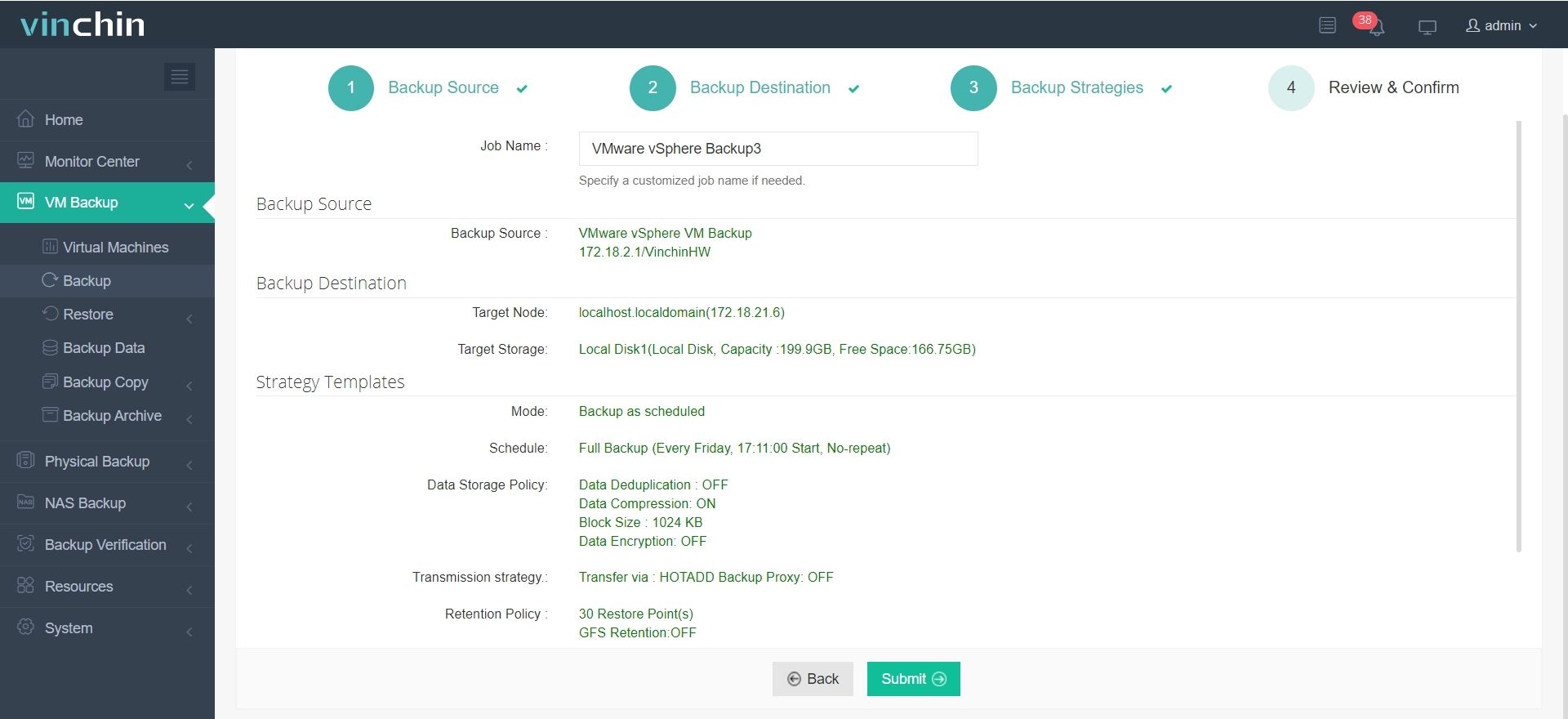
Discover the power of this comprehensive system firsthand with a free 60-day trial! Leave your specific needs, and you will get a customized solution that fits your IT environment perfectly.
Data Protection in Research FAQs
1. How long should research data be retained?
Typically 5–10 years, depending on institutional policy, funder requirements, or regulatory frameworks.
2. What's the difference between anonymized and pseudonymized data?
Anonymized data cannot be traced back to an individual.
Pseudonymized data replaces identifiers with codes but can be re-identified with a key.
Conclusion
Data protection in research is a balancing act: enabling collaboration while safeguarding privacy. From GDPR's legal rigor to encryption tools and institutional policies, a multi-layered approach is essential. As threats evolve, so must solutions—grounded in technology, guided by ethics, and sustained by global cooperation. Protecting data isn't just about avoiding breaches; it’s about preserving the integrity of science itself.
Share on:








