-
What Is Endpoint Cloud Backup?
-
Why Endpoint Cloud Backup Matters?
-
How Endpoint Cloud Backup Works?
-
Introducing Vinchin Backup & Recovery: Fast Enterprise File Protection Across Platforms
-
Endpoint Cloud Backup FAQs
-
Conclusion
Data loss can strike at any time—laptops get stolen, desktops crash without warning, and ransomware attacks are on the rise everywhere. For IT administrators managing distributed teams or remote workers, protecting every endpoint is now a top priority. Endpoint cloud backup offers a reliable answer to these challenges by securing data offsite in the cloud. But what does this really mean? How do you set it up? Let’s break it down step by step so you can protect your organization’s most vulnerable devices with confidence.
What Is Endpoint Cloud Backup?
Endpoint cloud backup is the process of copying data from endpoint devices—like laptops, desktops, tablets, or even mobile phones—to secure cloud storage managed by your organization or a trusted provider. Unlike traditional backups that rely on local servers or external drives connected directly to endpoints, endpoint cloud backup sends files straight to remote storage over an encrypted internet connection.
Key Components: Agent Software and Cloud Storage
Most solutions require installing a lightweight agent on each device you want to protect. This agent scans selected folders or drives for important files based on policies you define centrally as an administrator. Once identified, files are encrypted using strong algorithms such as AES-256 before leaving the device—ensuring privacy during transit and at rest in the cloud. Data then travels securely via protocols like HTTPS or TLS 1.2+ to dedicated storage buckets in public or private clouds.
The result? Even if an endpoint is lost or destroyed—whether due to theft, hardware failure, fire, flood, or malware—you can restore its critical data quickly from anywhere with internet access.
Why Endpoint Cloud Backup Matters?
Why should organizations invest in endpoint cloud backup? Endpoints are everywhere—and they’re often outside traditional network defenses due to remote work trends and BYOD (bring-your-own-device) policies. Each device holds valuable business information that could be lost forever if not protected properly.
Common Risks and Scenarios
Consider these everyday risks: A sales manager loses their laptop at an airport; a developer’s desktop crashes after a power surge; ransomware encrypts every file on an executive’s tablet overnight; someone accidentally deletes project folders while working remotely; compliance auditors request proof of recoverable records after an incident.
In each case above—and many more—endpoint cloud backup ensures business continuity by making sure recent copies of important files exist offsite where they can’t be tampered with locally.
Business Impact & Compliance Needs
Lost endpoint data isn’t just inconvenient—it can cost thousands of dollars per incident when factoring in downtime recovery efforts. Regulatory requirements like GDPR or HIPAA mandate that sensitive information must always be recoverable after disasters or cyberattacks; failing this could result in heavy fines or reputational damage for your company.
Endpoint cloud backup helps meet these obligations by providing automated retention policies and immutable archives that prove compliance during audits—a must-have feature for regulated industries like healthcare or finance.
How Endpoint Cloud Backup Works?
Let’s look closer at how endpoint cloud backup operates behind the scenes so you know what happens at each stage—from setup through recovery.
Key Steps in the Backup Process
First comes deployment: You install agent software on every device needing protection using tools like group policy scripts or manual installers provided by your chosen solution vendor (no competitor names here!). Next:
1. Agents scan designated folders/drives based on admin-defined rules.
2. Files are encrypted locally using robust ciphers such as AES-256.
3. Encrypted blocks are sent over secure channels (HTTPS/TLS) directly into assigned buckets within your organization’s preferred public/private/hybrid clouds.
4. Backups run automatically according to schedules you set—hourly/daily/weekly—or trigger upon certain events such as user logoff.
5. Centralized dashboards let admins monitor job status across hundreds/thousands of endpoints from anywhere via web browsers.
6. When disaster strikes—or users need specific files restored—you simply select desired versions/timestamps from intuitive interfaces then click RESTORE; data flows back securely onto original/new devices within minutes depending on bandwidth/location factors.
7. Advanced systems support point-in-time restores so you can roll back entire directories/systems before malware infections occurred—a lifesaver during ransomware outbreaks!
Introducing Vinchin Backup & Recovery: Fast Enterprise File Protection Across Platforms
For organizations seeking high-performance file protection across diverse environments—including Windows/Linux file servers, NAS devices, S3 object storage, and more—a robust solution is essential. Vinchin Backup & Recovery stands out as a professional enterprise-grade file backup platform supporting nearly all mainstream file storage types found in modern infrastructures. Whether you're safeguarding NAS shares central to team collaboration or Linux servers powering critical workloads, Vinchin Backup & Recovery delivers exceptional speed thanks to its advanced architecture.
By leveraging proprietary technologies such as simultaneous scanning with real-time data transfer and merged file transmission methods, Vinchin Backup & Recovery achieves significantly faster backup speeds than most competitors—even under demanding workloads typical of large enterprises.
Among its extensive capabilities are incremental backups for efficiency, wildcard filtering for precise selection criteria, throttling policies for bandwidth management, multi-level compression options, automatic reconnection handling unstable networks, invalid shortcut cleanup routines, granular permission recovery features, strong encryption standards (AES), cross-platform restore flexibility between different storage types (file server/NAS/Hadoop/object), integrity checks ensuring unaltered restorations, advanced storage protection against ransomware threats including WORM support and built-in Kaspersky-powered malware detection—all designed around reliability and security at scale. Five standout features—integration with major platforms including NAS/S3/Linux servers; ultra-fast incremental backups; comprehensive integrity checks; ransomware-resistant storage protection; and seamless cross-platform restoration—combine to deliver unmatched resilience and operational simplicity for enterprise environments.
Managing backups through Vinchin Backup & Recovery's web console is exceptionally straightforward:
Step 1. Select the files from your chosen platform to back up
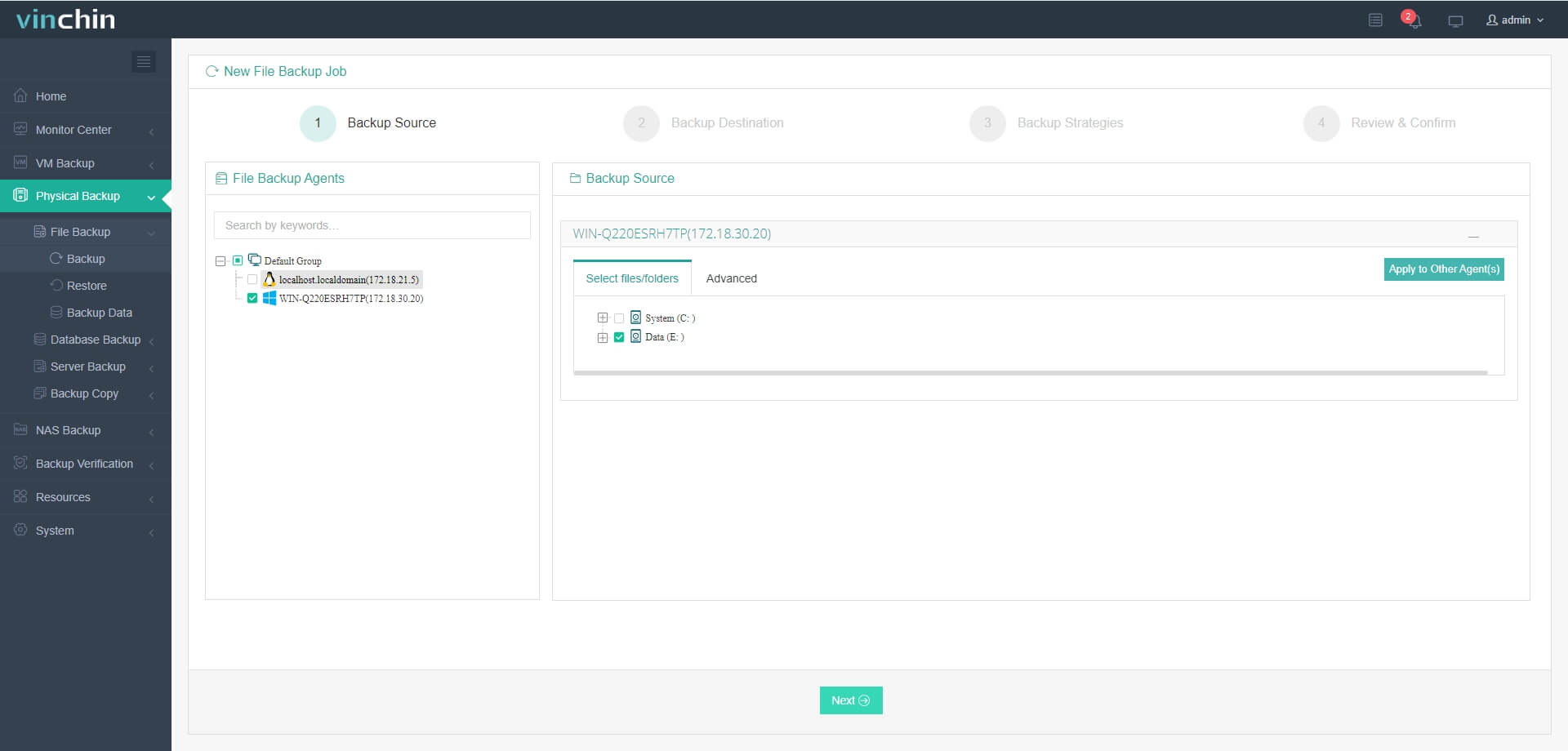
Step 2. Choose the destination storage
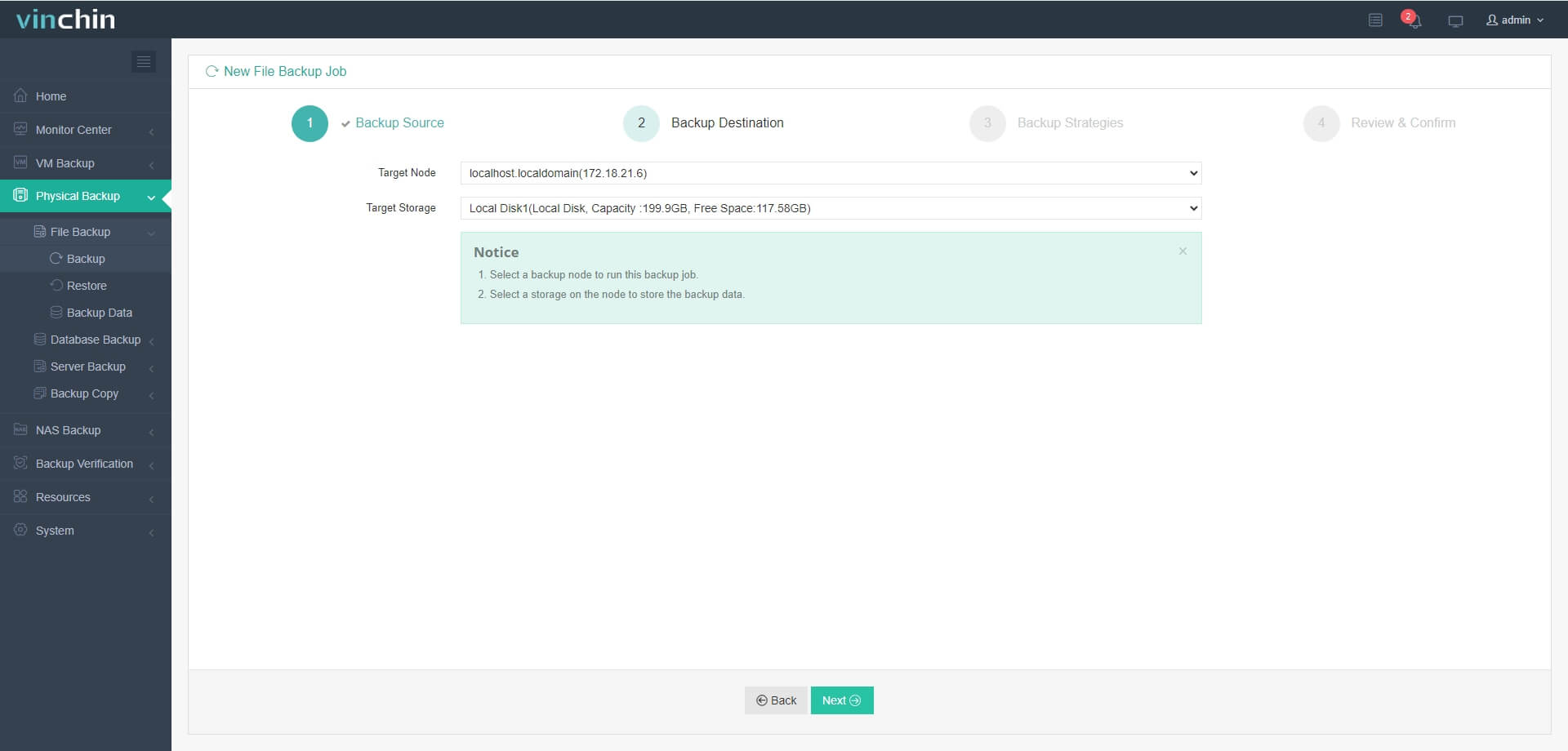
Step 3. Define your preferred backup strategy
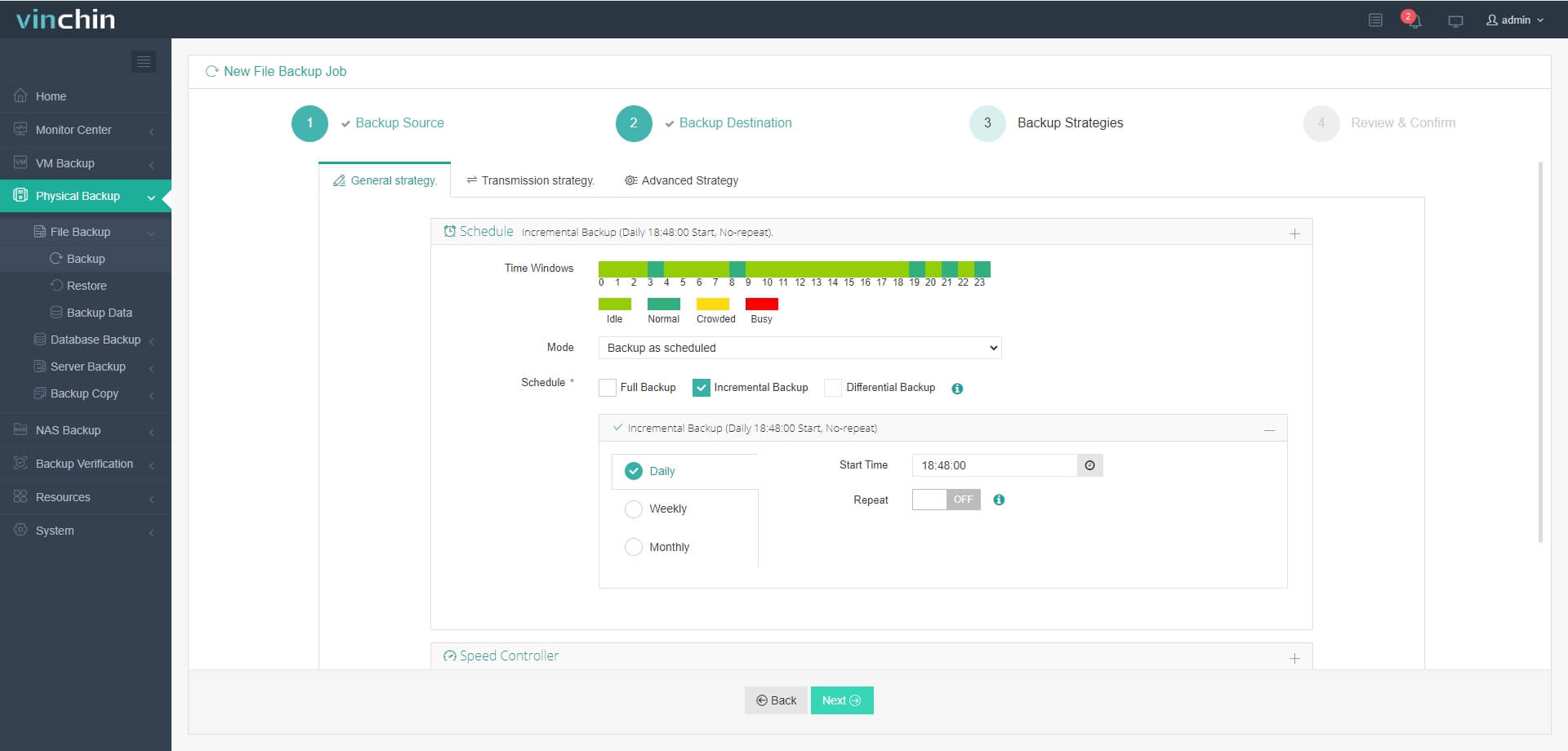
Step 4. Submit the job
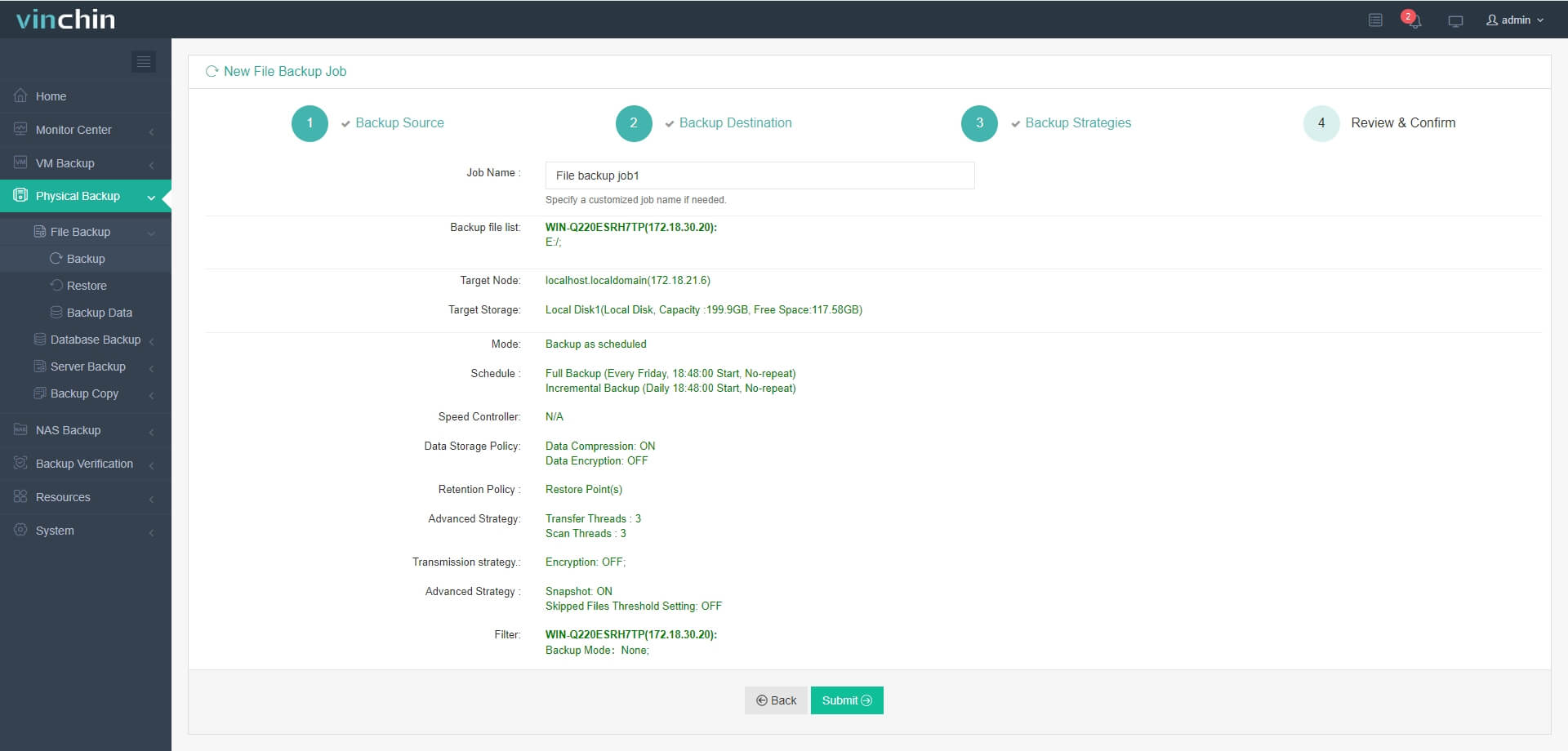
Recognized globally by thousands of satisfied customers and consistently rated among top enterprise data-protection solutions worldwide—Vinchin Backup & Recovery offers a full-featured 60-day free trial so you can experience its advantages firsthand today!
Endpoint Cloud Backup FAQs
Q1: Can I protect employee laptops that connect sporadically?
A1: Yes; agents resume uploads automatically whenever devices reconnect online ensuring no gaps even if users travel frequently/offline often.
Q2: How do I quickly restore just one document without overwriting everything else?
A2: Log into WEB CONSOLE > Find DEVICE > Open BACKUP > Select FILE > Click RESTORE
Q3: What should I do if malware infects several endpoints simultaneously?
A3: Use centralized dashboard to identify affected machines > Restore clean versions from last safe point-in-time > Initiate full scans post-recovery
Conclusion
Endpoint cloud backup keeps business-critical data safe wherever employees work—from home offices to airports worldwide—and ensures fast recovery after disasters big/small alike! Vinchin provides fast secure protection purpose-built for today’s dynamic environments—try it now risk-free!
Share on:






