-
What Is Cloud Backup Ransomware?
-
Why Do Attackers Target Cloud Backups?
-
Method 1: Enable Immutable Backups With AWS S3 Object Lock
-
Method 2: Use Microsoft Azure Backup Protection Features
-
Method 3: Implement Multi-Factor Authentication On Backup Access
-
How to Protect Data from Ransomware With Vinchin Backup & Recovery?
-
Cloud Backup Ransomware FAQs
-
Conclusion
Ransomware is no longer just a threat to local servers—it now targets your last line of defense: cloud backups. As more businesses move critical data offsite, attackers follow close behind. Are your cloud backups truly safe? Let’s explore what you need to know about cloud backup ransomware—and how you can stay ahead of these evolving threats.
What Is Cloud Backup Ransomware?
Cloud backup ransomware refers to attacks where criminals try to encrypt, delete, or corrupt your cloud-based backup data so you cannot recover after an attack without paying them off. Unlike traditional ransomware that locks files on desktops or servers, modern variants go straight for your protected copies in the cloud—often using stolen credentials or exploiting weak security settings.
Attackers may use malware or phishing to steal admin passwords or keys that control access to your storage accounts or management consoles. Once inside, they might delete snapshots, change retention policies, disable alerts—or even overwrite clean backups with encrypted versions of their own making your recovery impossible unless you pay up.
Why Do Attackers Target Cloud Backups?
Why would someone go after your backups instead of just locking up production systems? Simple—they want leverage over you when you’re most vulnerable! If they destroy every copy of your business-critical data—even those stored in the cloud—you have little choice but to negotiate.
Cloud backups are attractive because they often hold the only untouched versions of important files like databases or virtual machines after an attack hits production systems hard. But if these backups aren’t properly secured—with strong access controls and immutability—they become easy prey for cybercriminals looking for maximum payout with minimum effort.
Weak permissions, lack of monitoring tools, missing multi-factor authentication (MFA), or misconfigured retention rules all open doors for attackers. That’s why resilient cloud backup strategies are essential—not all solutions offer equal protection!
Method 1: Enable Immutable Backups With AWS S3 Object Lock
Immutability means nobody—not even administrators—can change or delete protected data during a set period (“Write Once Read Many”). This is one of the strongest defenses against ransomware wiping out your safety net in Amazon Web Services environments.
To use AWS S3 Object Lock:
You must enable it when creating a new bucket; this setting cannot be added later.
Versioning must also be enabled since Object Lock relies on object versions.
There are two modes: Governance (admins can override under certain conditions) and Compliance (no one can remove objects until time expires—even AWS support).
Here’s how you set it up:
1. In the Amazon S3 console click Create bucket
2. Enter a unique Bucket name and select a Region
3. Under Object Lock, check Enable Object Lock
4. Complete other settings then click Create bucket
After setup:
1. Upload files as usual
2. Select objects then choose Actions > Edit retention
3. Pick either Governance mode or Compliance mode, set retention period
4. Click Save changes
With these steps done right—even if attackers get admin rights—they cannot erase locked objects until their timer runs out. Note that Compliance mode may have legal implications if used incorrectly; always consult compliance teams before enabling strict lock periods!
Method 2: Use Microsoft Azure Backup Protection Features
Microsoft Azure offers several built-in protections designed specifically against ransomware targeting cloud backups—including soft delete options, role-based access control (RBAC), immutable blob storage policies, plus Multi-User Authorization (MUA) using security PINs sent via email before destructive actions like deleting vaults or restoring sensitive items.
To create secure Azure backups:
1. In the Azure portal, navigate to Recovery Services vaults then select + Add
2. Enter a unique vault name plus region then click Review + create
3. Open your new vault then select Backup
4. Choose your source type (Azure Virtual Machine, file shares etc.)
5. Follow prompts to configure schedules/retention
Azure enables soft delete by default—deleted items remain recoverable for at least 14 days unless purged manually by authorized users only. For extra safety:
Go into vault properties under Security Settings
Confirm that Soft Delete is set as Enabled
Critical operations will prompt for a one-time Security PIN sent via email—a feature called Multi-User Authorization requiring proper Azure AD permissions
For advanced scenarios such as immutable blob storage:
Enable versioning on storage accounts holding backup blobs
Set legal hold policies where required so no one—including admins—can alter protected data until holds expire
These layers make it much harder for attackers who breach credentials alone to cause lasting damage!
Method 3: Implement Multi-Factor Authentication On Backup Access
Multi-factor authentication adds another wall between hackers and your precious backup data—even if they steal passwords through phishing emails or malware infections! It requires users prove their identity using something they know (password) plus something they have (authenticator app/hardware token).
To enable MFA across popular platforms:
1.Go into IAM console (Identity & Access Management) at your provider
2.Select users/groups responsible for managing backups/storage
3.Click on either “Enable Multi-Factor Authentication” or “Add MFA device”
4.Register authenticator app/hardware key following prompts
For AWS use IAM > Users > Security credentials > Manage MFA device; in Azure use Azure Active Directory > Users > Multi-Factor Authentication settings menu.
Remember—not all service accounts support standard MFA! Where possible combine this with conditional access policies limiting login locations/devices plus principle-of-least privilege so only necessary people touch sensitive controls.
How to Protect Data from Ransomware With Vinchin Backup & Recovery?
Beyond native public-cloud features, organizations benefit from unified solutions that streamline protection across diverse platforms such as S3 object storage, NAS appliances, and Windows/Linux file servers—all common targets in today’s hybrid IT environments impacted by ransomware threats discussed above. Vinchin Backup & Recovery stands out as an enterprise-grade file backup solution supporting nearly all mainstream file storage types on the market—including but not limited to S3-compatible object stores, NAS devices, and both Windows and Linux file servers—with industry-leading speed thanks to its advanced architecture.
Vinchin Backup & Recovery leverages proprietary technologies such as simultaneous scanning/data transfer and merged file transmission mechanisms that deliver exceptionally fast backup performance—outpacing most competitors significantly when handling large-scale workloads and complex datasets typical in enterprise settings.
Among its many capabilities, five standout features include incremental backup support for efficiency; wildcard filtering for precise selection; robust throttling policy management; multi-level compression options; and cross-platform restore flexibility allowing seamless recovery between file server/NAS/object storage targets—all designed to maximize reliability while minimizing resource consumption and operational complexity.
The web console of Vinchin Backup & Recovery is extremely intuitive: backing up critical assets typically involves just four steps tailored for each environment—for example:
Step 1. Select the S3 object storage files to back up
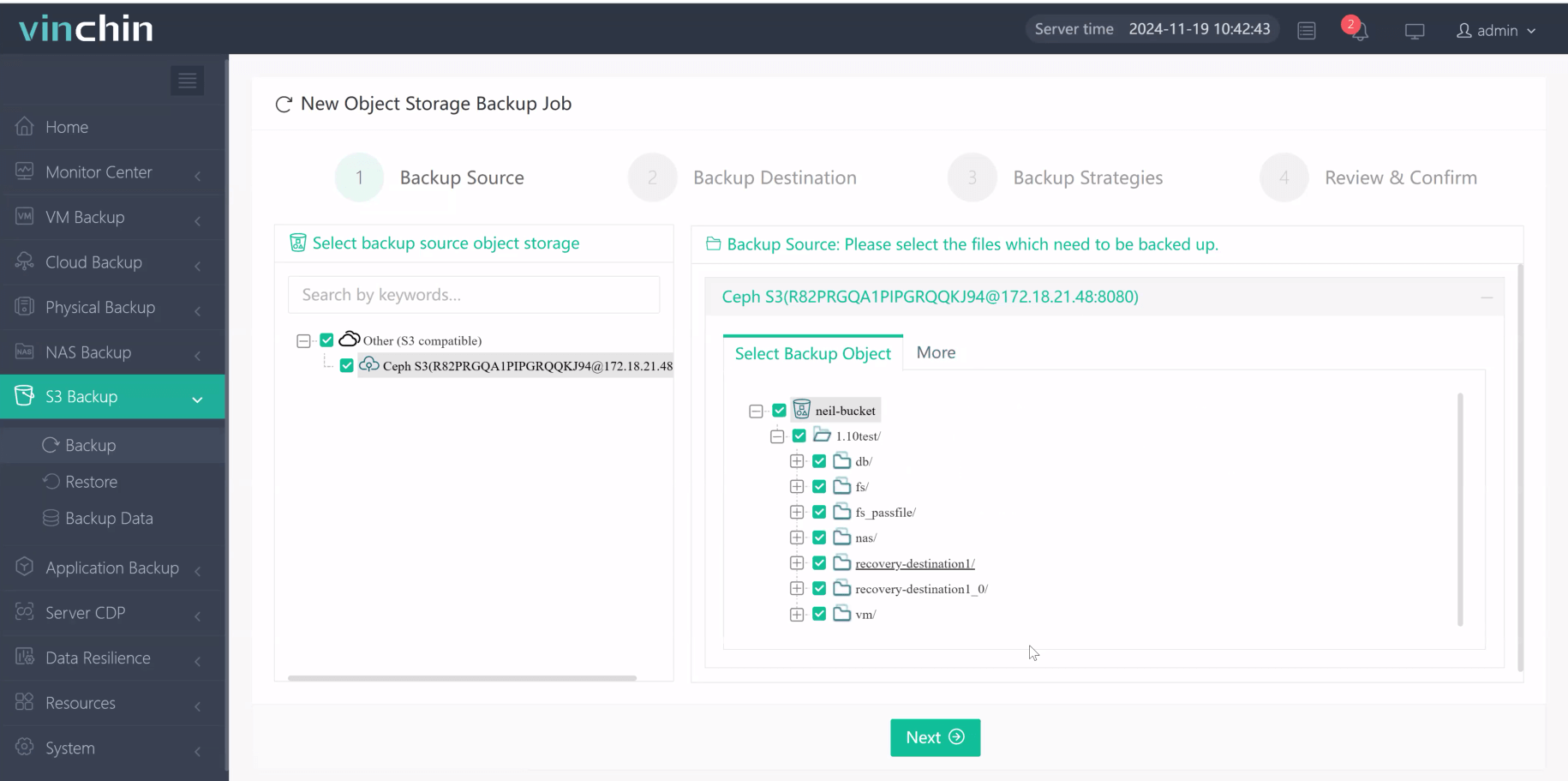
Step 2. Choose the desired backup destination
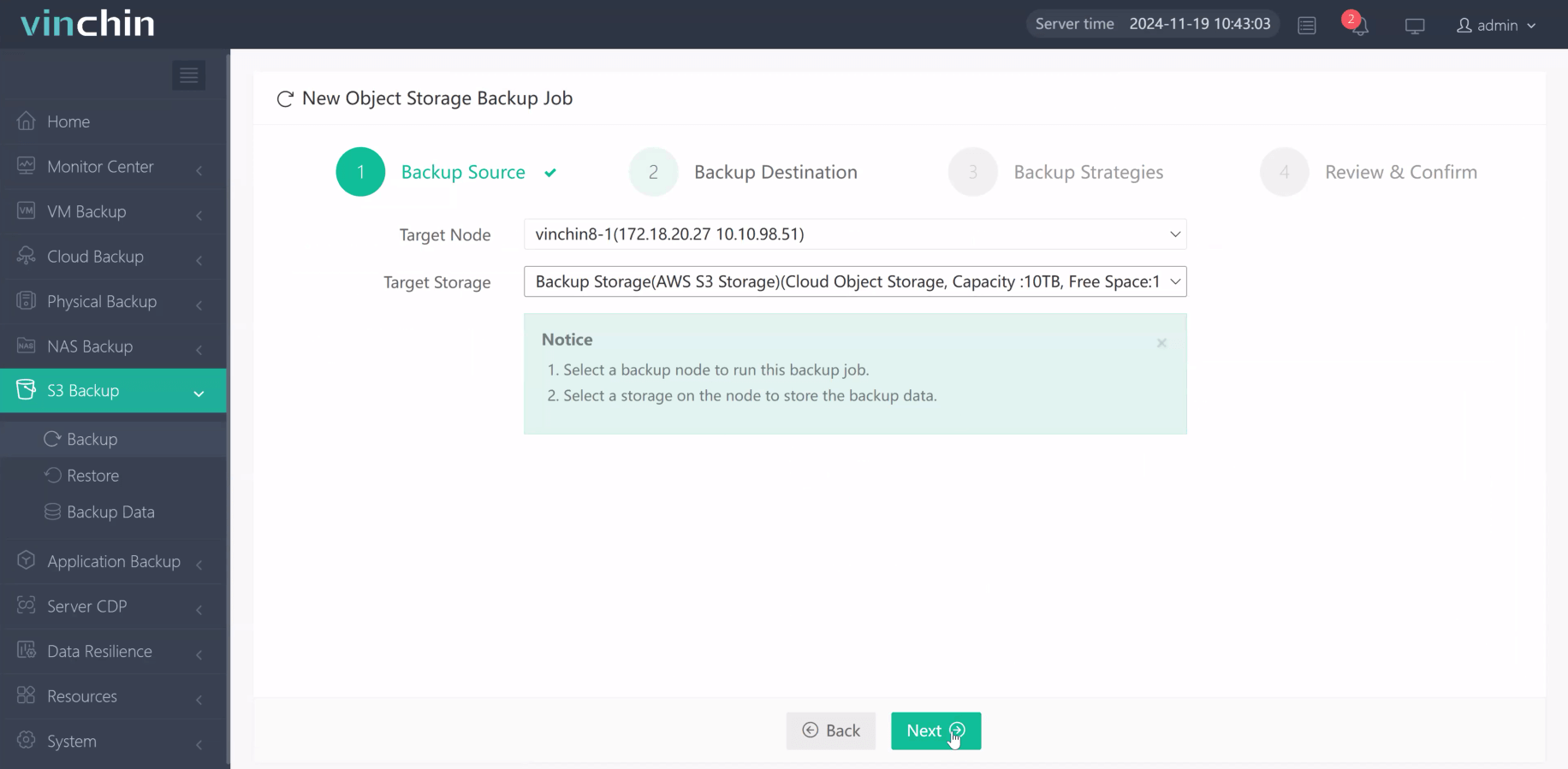
Step 3. Define scheduling/compression/throttling strategies
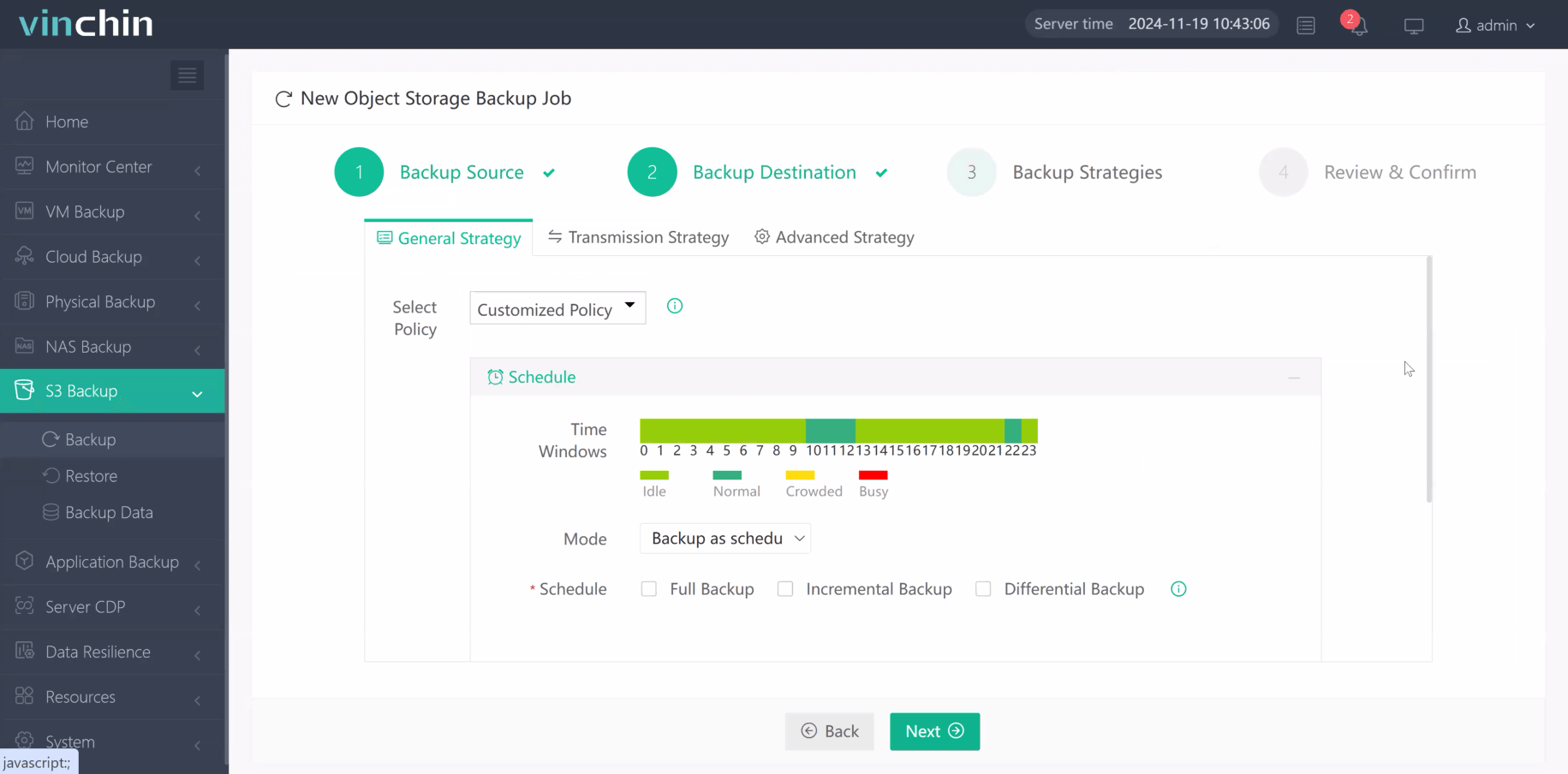
Step 4. Submit the job
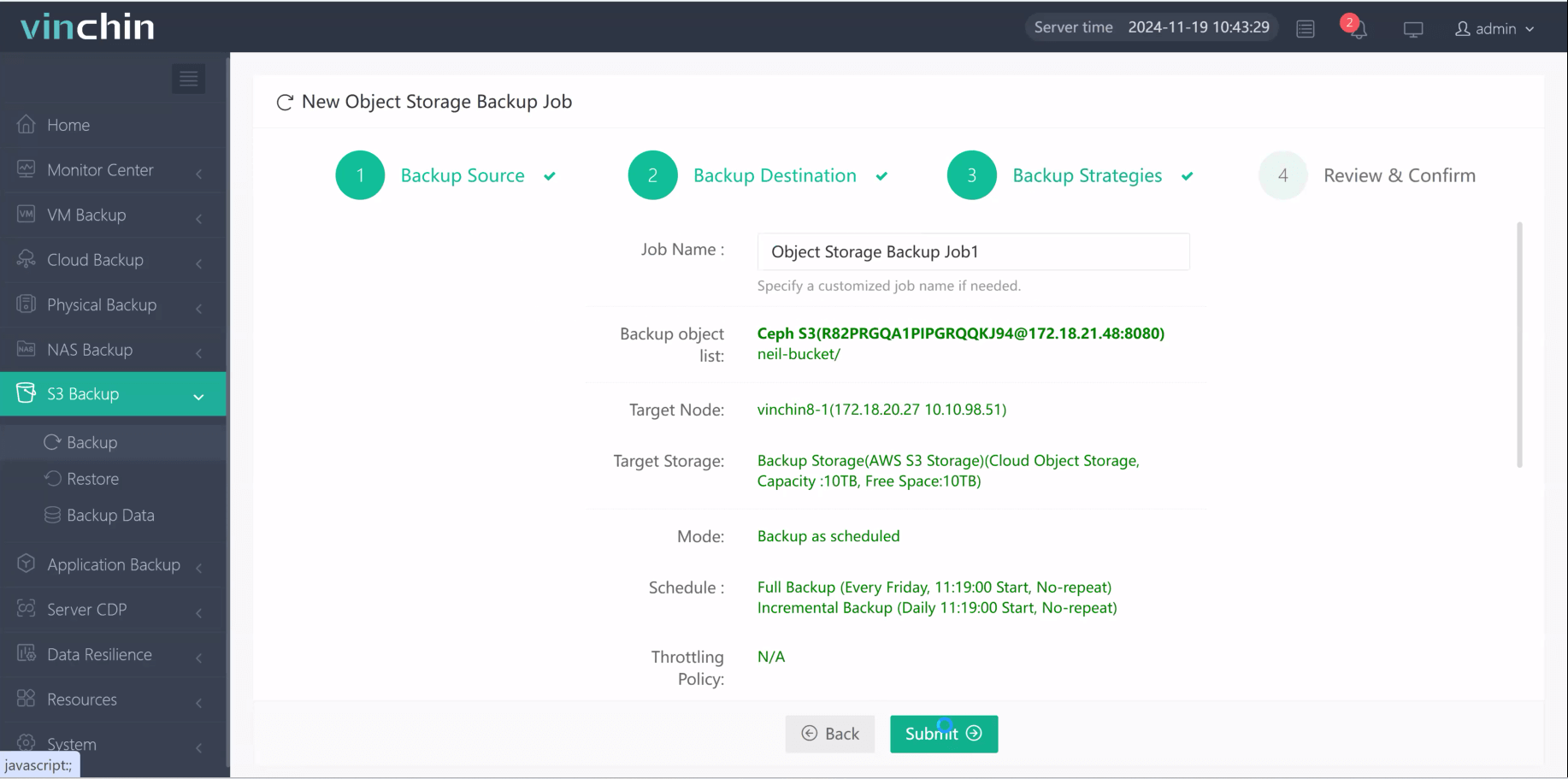
Trusted globally by thousands of enterprises with top ratings in independent reviews, Vinchin Backup & Recovery offers a fully featured free trial valid for 60 days—click below to experience comprehensive protection risk-free!
Cloud Backup Ransomware FAQs
Q1: Can I reduce costs while still using immutable storage?
A1: Yes—apply immutability only on mission-critical datasets while archiving less-sensitive files using standard lifecycle rules instead of locking everything by default.
Q2: How do I detect unauthorized deletion attempts quickly?
A2: Set up automated alerts via CloudTrail/EventBridge in AWS—or Activity Log/Sentinel integration in Azure—to notify admins immediately upon suspicious actions detected within protected buckets/vaults/accounts.
Q3: What should I do first if my primary restore fails due to corrupted backups?
A3: Immediately attempt restoring alternate copies from secondary regions/tapes/cloud providers while escalating incident response procedures per documented playbooks involving relevant stakeholders promptly coordinating next steps together efficiently.
Conclusion
Cloud backup ransomware poses serious risks—but layered defenses make successful attacks far less likely when implemented correctly across every level involved! Immutability/MFA/testing routines form foundation while proactive monitoring catches trouble early enough responding decisively matters most. Vinchin helps simplify protecting diverse environments end-to-end so peace-of-mind stays within reach always!
Share on:








