-
Why is data protection so important?
-
What are the six core elements of an enterprise data protection strategy?
-
Tech-driven protection: how to choose the right platform for data security
-
Enterprise data protection strategy FAQs
-
Conclusion
In an era where cyber threats and regulatory scrutiny are escalating, data protection is no longer just a compliance checkbox—it’s a cornerstone of modern business resilience. Against the backdrop of accelerated digital transformation, data has surpassed traditional resources to become the lifeblood of operations and decision-making. From customer information and transaction records to R\&D results and intellectual property, the volume of data generated and relied upon by enterprises is growing exponentially. At the same time, the rise in threats such as cyberattacks, system failures, human errors, and natural disasters has made effective protection of critical data a pressing issue for business survival and growth.
Therefore, building a scientific, systematic, and sustainable enterprise data protection strategy is not only vital to ensuring the integrity and security of data itself, but also to safeguarding a company’s reputation, operational continuity, and legal compliance. Whether a large multinational corporation or a small-to-medium-sized business, data protection should never be treated as an “optional” initiative—it must be an integral part of corporate strategic planning.
Why is data protection so important?
Preventing Data Breaches and Cyberattack Risks
Data breaches are becoming increasingly common, with evolving threats such as ransomware, phishing emails, and supply chain attacks. When an enterprise’s core data is stolen or compromised, it can lead not only to direct financial losses but also to customer churn and serious damage to brand reputation.
Meeting Global Compliance and Privacy Protection Requirements
Governments and regions around the world are enacting stricter data protection regulations, such as the EU's General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA) in the U.S., and Brazil’s General Data Protection Law (LGPD). As businesses expand globally, they must navigate diverse data compliance requirements to avoid legal penalties and maintain a positive corporate image.
Ensuring Business Continuity and Disaster Preparedness
In the event of hardware failures, system crashes, fires, floods, or other emergencies, a lack of proper data backup and recovery mechanisms can leave a company paralyzed for extended periods—or worse, unable to survive. A sound data protection strategy is a key component of any disaster recovery plan.
Strengthening Customer Trust and Partner Relationships
In today's business ecosystem, both customers and partners are increasingly concerned with an organization’s data protection capabilities. A robust data security framework not only builds trust but also enhances a company's competitiveness in bidding processes and business expansion efforts.
What are the six core elements of an enterprise data protection strategy?
To achieve comprehensive and sustainable data protection, enterprises must focus on the following critical areas:
1. Data Classification and Tiered Management
Not all data holds the same value. Enterprises should identify and categorize their data into levels such as “highly sensitive,” “important,” and “general,” then implement corresponding protection measures and access control policies. Only through tiered data protection can resources be allocated efficiently and risks managed with precision.
2. Multi-Level Backup and Recovery Mechanisms
Backup is the cornerstone of data protection. Enterprises should adopt a layered backup architecture that includes on-premises, offsite, and cloud-based backups to ensure redundancy across different physical locations. Solutions should support full backups, incremental backups, and deduplication/compression technologies, and regular recovery tests must be conducted to validate the effectiveness and timeliness of emergency recovery processes.
3. Data Encryption and Identity Authentication
Sensitive data must be encrypted during both storage and transmission. Deploying multi-factor authentication (MFA) and access log auditing helps prevent unauthorized access and mitigate the risk of internal data leaks.
4. Network and Endpoint Security Protection
Establish a layered defense system including firewalls, intrusion detection and prevention systems (IDS/IPS), and Security Information and Event Management (SIEM) tools. At the same time, strengthen the management of employee endpoint devices to prevent data leakage caused by weakened security boundaries.
5. Security Awareness Training and Policy Development
Technology alone cannot solve all security challenges—human factors are equally critical. Organizations should conduct regular security awareness training for employees, clearly define data handling procedures and responsibilities, and establish formal policies for data access, storage, sharing, and deletion.
6. Business Continuity and Disaster Recovery Planning (BCP/DRP)
Enterprises should develop business continuity plans and disaster recovery strategies targeting core systems. These plans must define key parameters such as data recovery priorities, Recovery Time Objectives (RTOs), and Recovery Point Objectives (RPOs). Regular drills should be conducted to ensure readiness in real-world scenarios.
Tech-driven protection: how to choose the right platform for data security
In building an enterprise data protection strategy, the choice of technology plays a critical role. Data protection is not just about establishing a management framework—it also requires the support of advanced and reliable technical solutions for effective implementation. Today’s market offers a wide range of mature, specialized tools covering data backup, recovery, encryption, data loss prevention, and disaster recovery. Enterprises should evaluate and adopt the most suitable technologies based on their IT infrastructure, business complexity, and data sensitivity to ensure both data security and business continuity.
Vinchin Backup & Recovery is a unified data protection solution designed for virtual environments, databases, and physical servers, providing comprehensive technical support for enterprises of various sizes and types. The platform is compatible with major virtualization platforms such as VMware, Hyper-V, XenServer, Proxmox, and OpenStack. By leveraging technologies like agentless backup, encrypted data transmission, and deduplication with compression, Vinchin significantly enhances both backup efficiency and data security.
It also supports full VM recovery, file-level recovery, and cross-platform recovery (V2V), offering flexible restore options to meet diverse business needs. For disaster preparedness, Vinchin provides features such as offsite replication, disaster recovery drills, and recovery verification, helping organizations build a robust disaster recovery framework. This ensures uninterrupted critical operations and zero data loss, even in the face of unexpected events.
Vinchin Backup & Recovery's operation is very simple, just a few simple steps.
1.Just select VMs on the host
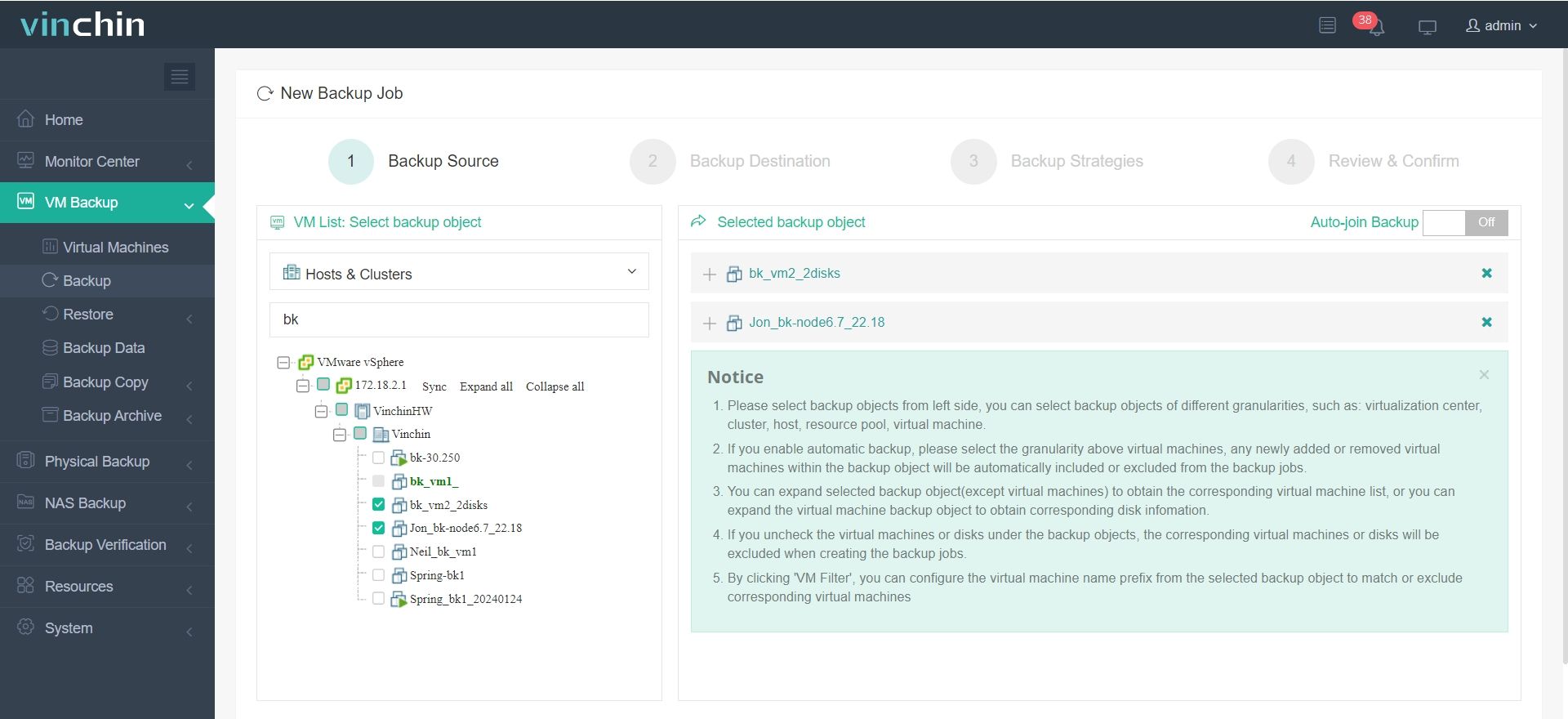
2.Then select backup destination
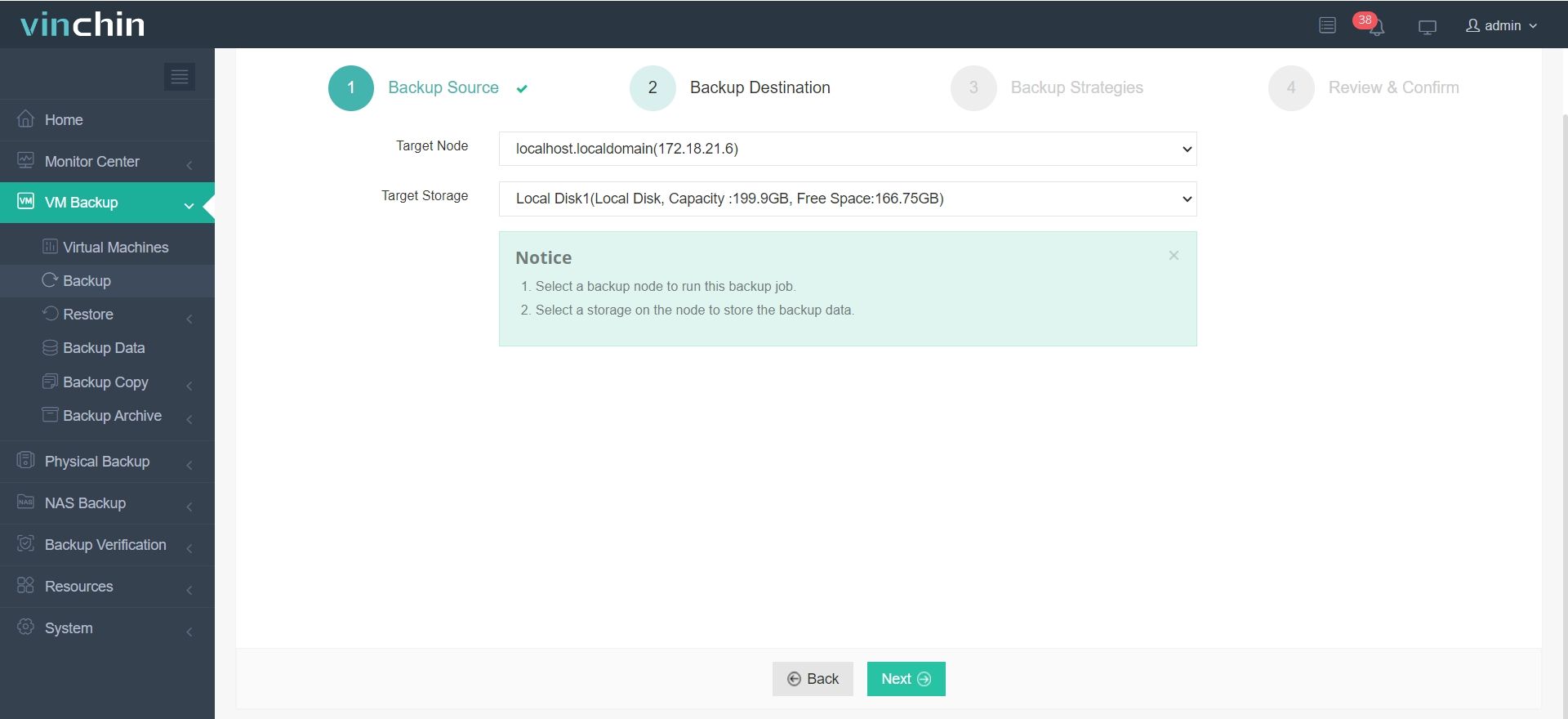
3.Select strategies
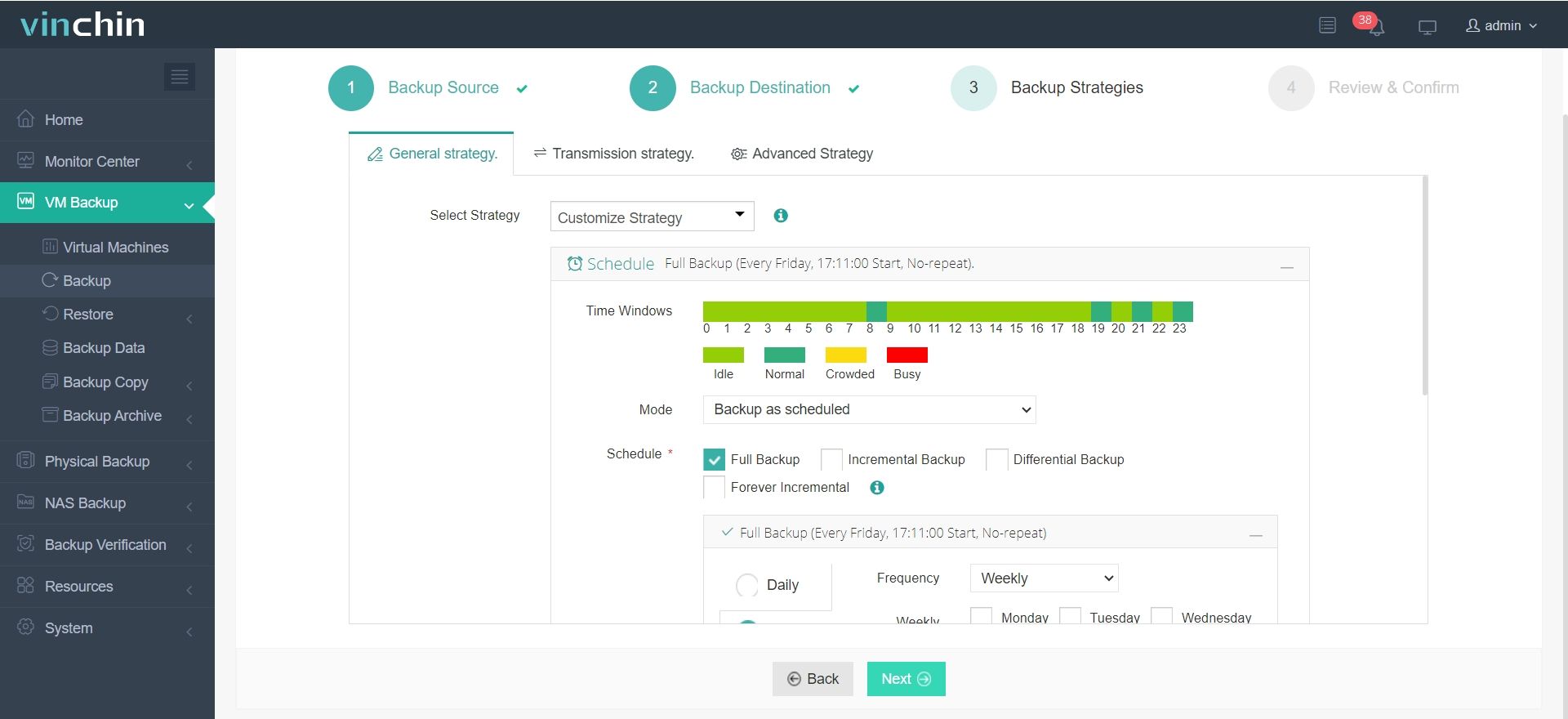
4.Finally submit the job
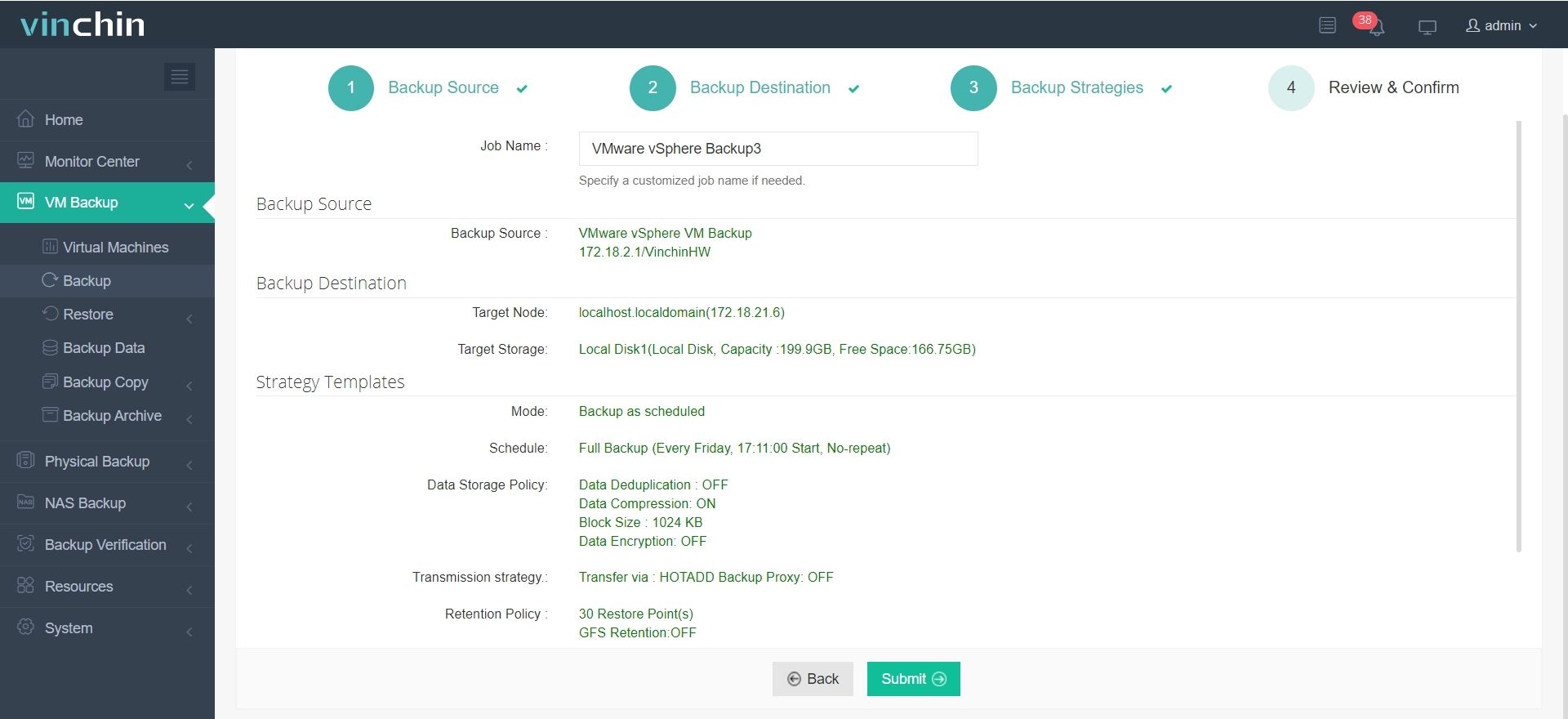
Try before you commit — Vinchin offers a full-featured 60-day trial.
Test it in your own environment. Reach out to us.
Enterprise data protection strategy FAQs
Q1: How to choose the right data protection solution?
A1: Choose the right technology and services based on your organization's size, budget, industry requirements, and specific needs. Considerations include, but are not limited to, ease of use, cost-effectiveness, scalability, compatibility, etc.
Q2: How do I assess the effectiveness of my data protection strategy?
A2: Examine the effectiveness of existing defenses by performing regular security assessments and penetration tests. Incident response plans should also be reviewed to ensure that you can respond quickly and effectively in the event of a data breach or other security incident.
Conclusion
Ultimately, data protection is not merely about avoiding penalties—it’s about future-proofing your business. By embedding resilience into data strategies (through classification, encryption, backups, and disaster recovery), enterprises can turn compliance into competitive advantage. In a world where disruptions are inevitable, the ability to safeguard and rapidly restore data defines which organizations thrive—and which merely survive.
Share on:





