-
What is OpenStack Keystone?
-
Features of OpenStack Keystone
-
Debugging Common Issues With Keystone
-
The Importance of Keystone in OpenStack
-
Enterprise-Level VM Backup Solution
-
OpenStack Keystone FAQs
-
Conclusion
OpenStack powers many private clouds worldwide by offering flexible compute, storage, and networking resources on demand. But how do you keep all those services secure? That’s where Keystone comes in. Keystone is OpenStack’s identity service—it manages users, roles, permissions, authentication methods, and service discovery across your cloud environment.
Identity management is critical in any cloud platform because it controls who can access what resources—and how they do it. Without strong identity controls like those provided by Keystone OpenStack would be unmanageable at scale or vulnerable to attack.
In this article we’ll explore what makes Keystone so important for OpenStack admins—from basic concepts to advanced features—then show how you can protect your workloads with reliable backup solutions.
What is OpenStack Keystone?
Keystone acts as the central gatekeeper for your entire OpenStack deployment. Every time a user or process tries to interact with an API—whether launching a VM or listing storage volumes—Keystone checks their credentials first.
At its core Keystone organizes users into domains and projects:
A domain is a logical boundary that groups users and projects together under one administrative umbrella.
A project (sometimes called a tenant) represents an isolated pool of resources like VMs or networks assigned to specific teams or applications within your organization.
This hierarchy allows large organizations to delegate administration while keeping data separate between business units or customers.
How Authentication Works
When someone logs into Horizon (the web dashboard) or uses the openstack CLI tool:
1. They provide their username/password (or another credential).
2. Keystone checks these credentials against its backend database—or an external source like LDAP.
3. If valid it issues a token—a temporary proof of identity.
4. This token must be presented when accessing other services; each service verifies it with Keystone before allowing any action.
Tokens have limited lifespans (usually one hour), reducing risk if they’re stolen.
Keystone also maintains a service catalog—a directory listing all available APIs (like Compute/Nova Storage/Cinder Networking/Neutron) along with their endpoints (URLs). When you authenticate successfully you receive this catalog so your tools know where to send requests without manual configuration.
For example if you want to create a VM your client will look up the Compute endpoint from the catalog then send API calls there using your token as proof of identity.
Features of OpenStack Keystone
Keystone offers many features designed for flexibility scalability and security in enterprise clouds:
Authentication and Authorization
The most basic job of Keystone is checking who you are—and what you’re allowed to do:
When you log in via Horizon or CLI your credentials are validated against either an internal SQL database LDAP server or federated provider.
If successful you get back a token which proves your identity until it expires.
Each API call includes this token; services check its validity before processing requests.
Role-based access control (RBAC) lets admins assign different permissions based on user roles within projects—for example “admin” can manage everything “member” can only use resources “reader” has view-only access.
You can define custom roles tailored to organizational needs such as “backup operator” or “network auditor.
Service Catalog Multi-Tenancy & Resource Isolation
As clouds grow multi-tenancy becomes essential:
Multiple organizations (“tenants”) share infrastructure but remain isolated from each other thanks to project boundaries enforced by Keystone.
Users belong to one or more projects; their role within each project determines what actions they can take there.
The service catalog ensures every authenticated user knows exactly which endpoints are available for their assigned projects/domains—reducing confusion when working across regions or environments.
Pluggable Backends
You don’t have to store user data inside OpenStack itself—you can point Keystone at external sources like LDAP Active Directory SQL databases even custom plugins written in Python! This enables seamless integration with existing corporate directories reducing duplication of effort during onboarding/offboarding processes.
Federation Across Clouds
Federation lets users authenticate via trusted external providers using SAML 2.0 Shibboleth ADFS Google Workspace etc.—ideal for hybrid/multi-cloud setups university collaborations mergers/acquisitions where multiple identity systems must coexist securely.
Token Types Deep Dive
Three main formats exist:
UUID tokens – simple random strings stored centrally; deprecated due to scaling/security limitations
Fernet tokens – lightweight encrypted payloads verified locally by services; default since Newton release; require regular key rotation (
keystone-manage fernet_rotate)JWS tokens – signed JSON Web Signatures using asymmetric cryptography; offer extra security but require PKI setup.
Debugging Common Issues With Keystone
Even well-run clouds hit snags sometimes:
Diagnosing Authentication Failures
If users report login problems check /var/log/keystone/keystone.log first—look for errors about invalid credentials expired tokens missing endpoints misconfigured backends etc.
Using CLI Tools For Troubleshooting
Run openstack token issue --debug after sourcing admin RC file—this shows detailed output including scopes expiry times project/domain assignments helping pinpoint permission gaps quickly
Updating Service Catalog Endpoints
If new APIs appear/disappear unexpectedly verify registration status via openstack catalog list. Missing entries usually mean incomplete registration during deployment—or typos in endpoint URLs/configuration files!
The Importance of Keystone in OpenStack
Without robust identity management cloud platforms become chaotic fast! Every resource request passes through keystone ensuring only authorized actions occur according to strict policies defined by admins—not end-users themselves.
If keystone goes down nothing else works reliably—that’s why high availability redundant controllers regular backups careful monitoring matter so much here compared with less critical components elsewhere!
Federation support means large enterprises universities research consortia can link disparate systems together securely without duplicating accounts everywhere—a huge win for operational efficiency compliance auditing too!
In short keystone isn’t just another microservice—it’s the backbone holding everything else together safely at scale!
Enterprise-Level VM Backup Solution
To ensure business continuity and safeguard critical workloads running on platforms like OpenStack, it's vital to choose a robust backup solution tailored for virtual environments at scale.
Vinchin stands out as a professional enterprise-level virtual machine backup solution supporting over 15 mainstream virtualization platforms—including VMware, Hyper-V, Proxmox, oVirt, OLVM, RHV, XCP-ng, XenServer, ZStack, and notably OpenStack itself—making it ideal for diverse IT infrastructures.
Key features include forever-incremental backup technology that minimizes storage usage while ensuring rapid recovery points; advanced deduplication and compression algorithms that reduce backup size and network load; seamless V2V migration capabilities across supported hypervisors; scheduled automated backups; granular restore options; plus comprehensive data verification mechanisms—all managed through an intuitive web console designed for simplicity even at scale.
Backing up an OpenStack VM with Vinchin takes just four steps:
1. Select the target OpenStack VM(s),
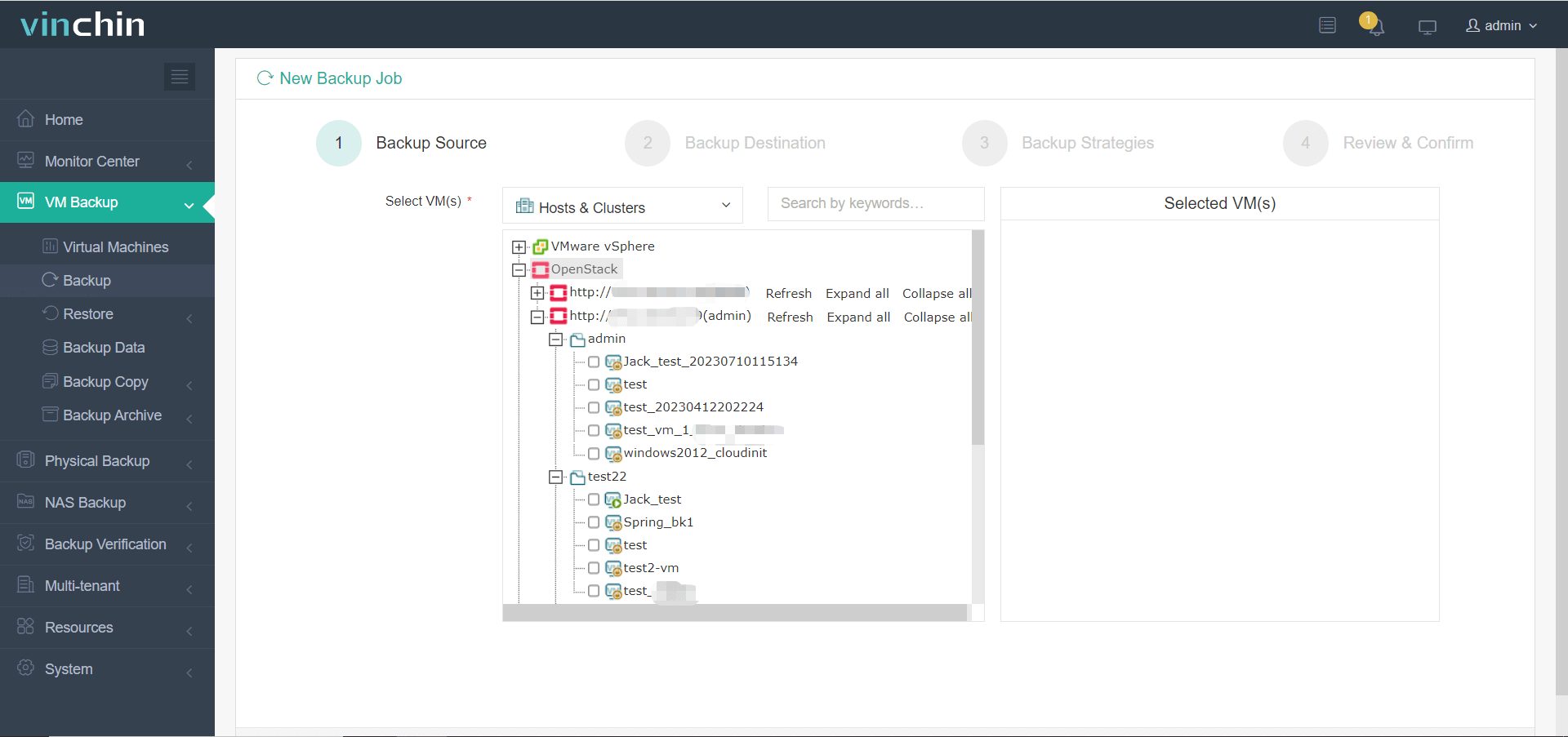
2. Choose backup storage location,
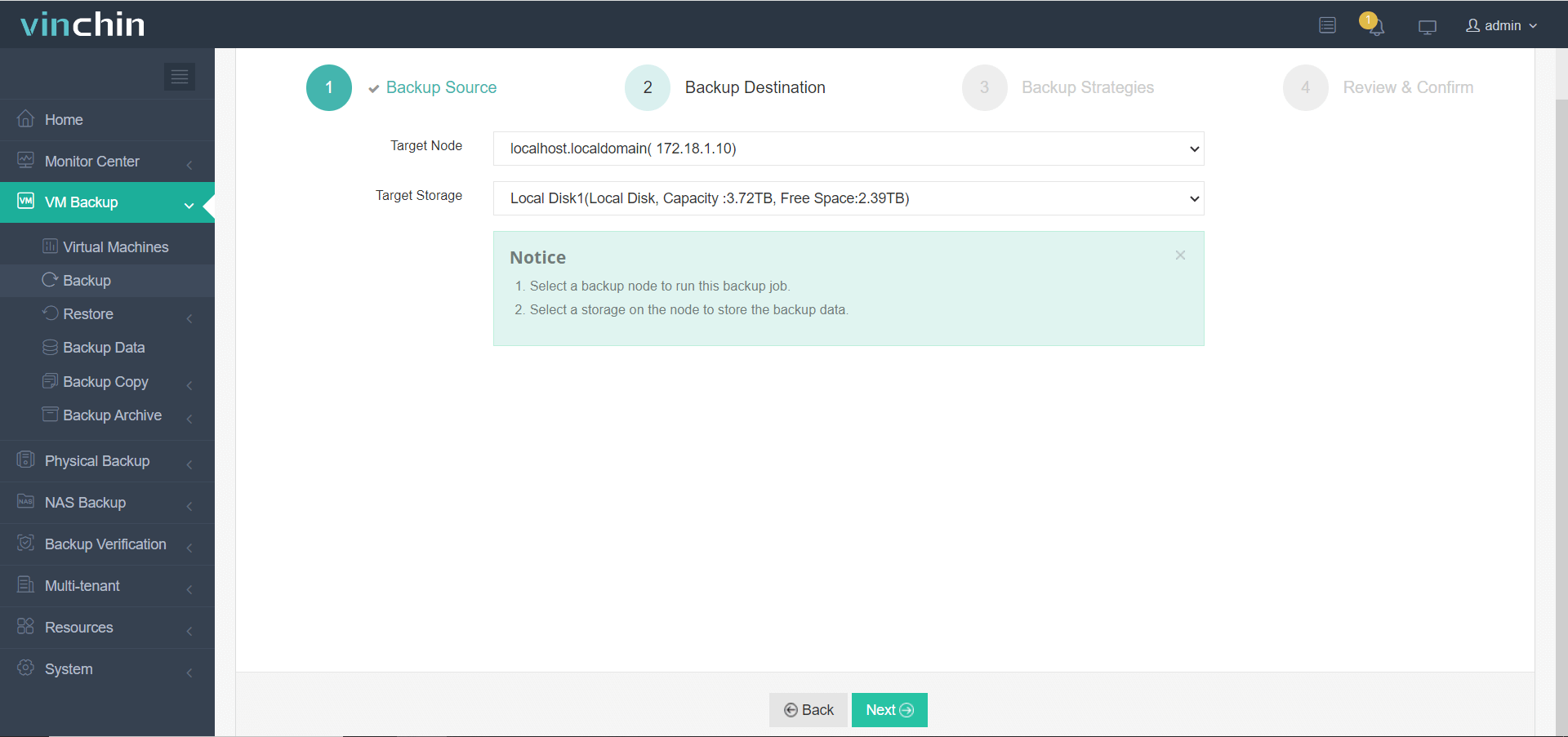
3. Configure desired backup strategies,
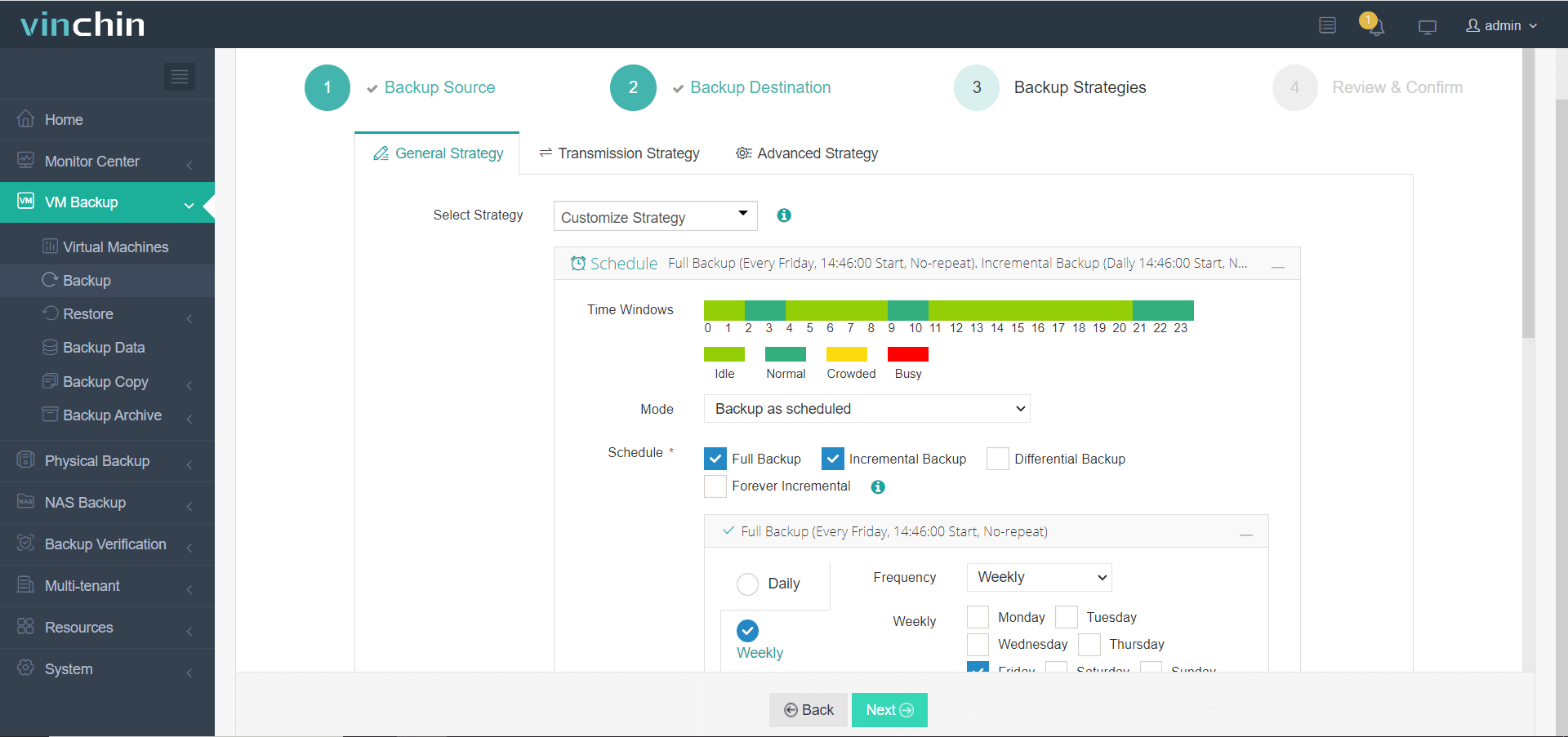
4. Submit the job.
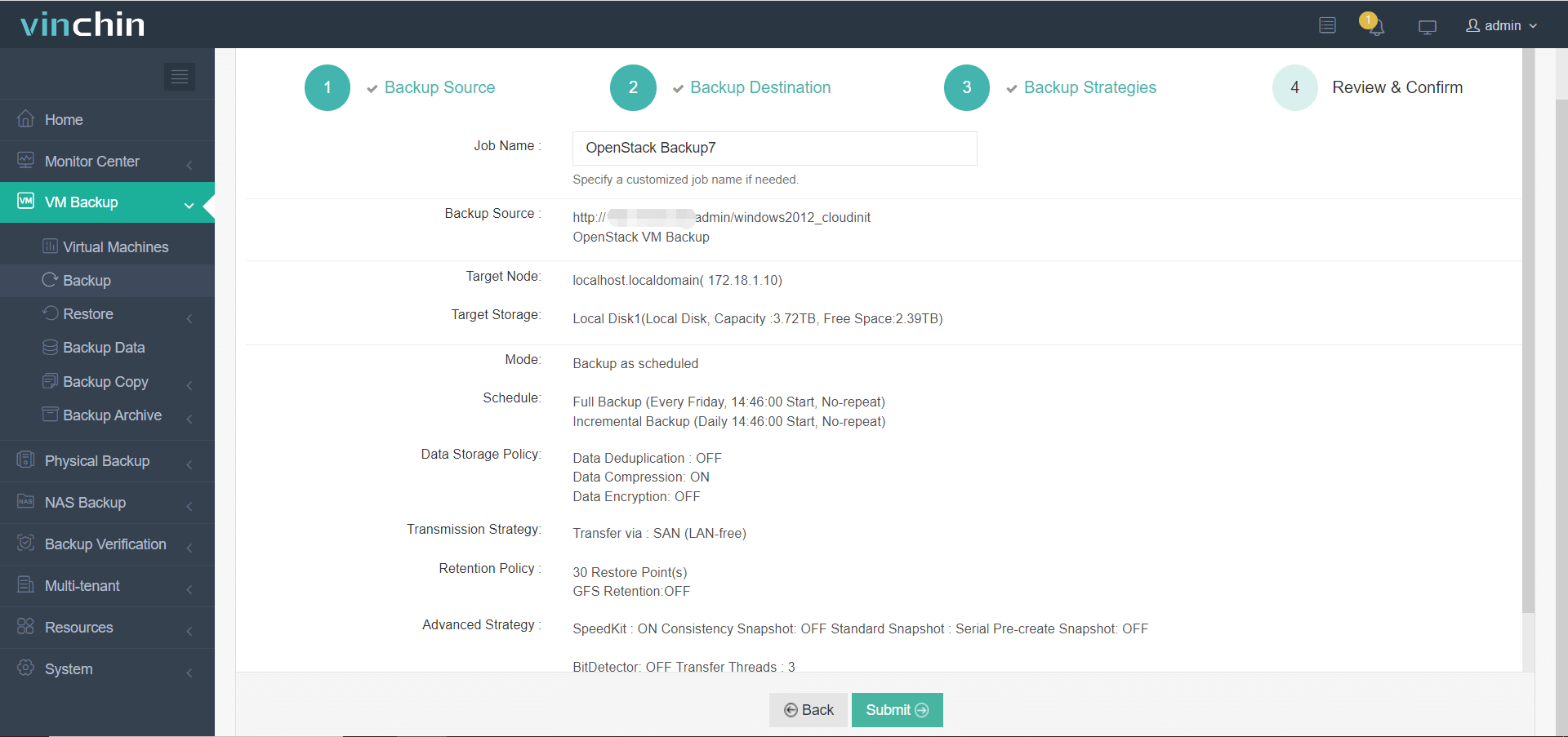
Vinchin enjoys global recognition among enterprises thanks to its reliability and high customer satisfaction ratings—and now offers a free 60-day full-featured trial! Click below to download the installer and start protecting your environment today.
OpenStack Keystone FAQs
Q1: How do I reset my forgotten admin password if locked out?
A1: Connect directly to the database update the password hash field for ‘admin’ then restart Apache/httpd.
Q2: How often should Fernet keys be rotated?
A2: Rotate Fernet keys at least once per month using KESTONE-MANAGE FERNET_ROTATE then synchronize updated key files across all controller nodes immediately afterward.
Q3: How do I add a new API endpoint/service URL into my existing service catalog?
A3: Run OPENSTACK SERVICE CREATE followed by OPENSTACK ENDPOINT CREATE specifying region interface URL type.
Conclusion
Keystone forms the foundation of secure scalable multi-user cloud environments powered by OpenStack—without it nothing else works safely! For reliable protection of those workloads Vinchin delivers powerful easy-to-use backup features plus much more—all ready today with a free trial download!
Share on:






